Blog / Reports / Resources
Setting Up and Managing Contacts in Microsoft Outlook
There’s no denying that email contacts are the modern-day equivalent of the traditional address book. For modern businesses, digital contacts are a company’s lifeline. They provide the means of connecting with clients, collaborating with team members and communicating...
When’s the Last Time You Checked on Your Domain Name?
For today’s business owners, web presence is everything. Making an impact online is how most modern businesses generate leads and make an impact on their target markets. A big part of a company’s online presence is their domain name. Your domain names serve as your...
Creating Killer CTAs: Increase Email Responses Without Lifting a Finger
Sending an email doesn’t guarantee that your recipient will take action. Create a compelling call to action and get the boost in response (or sales) that you need without lifting a finger! Anyone writing an email will tell you that they’re dreaming of...
Using Technology to Boost Non-Profit Success
Non-profits that utilize technology find that it creates engagement, automates the fundraising process, improves emergency response time, and leads to higher levels of success. “Before the Parade Passes By,” the great song from the Broadway smash musical, “Hello,...
The Changing Face of Browser Histories: Understanding and Managing the Privacy Concerns of Business Browser Histories
There’s a running joke for modern times. If you were to die unexpectedly, you should have a close friend on notice to clear your internet’s browser history to destroy your most embarrassing and private online footprints. However, as the technology landscape continues...
Learn More About Microsoft Outlook 2016’s AutoArchive Feature
It’s a thorn in the side of every modern business. Emails seem to come in faster and faster every day. Even when spam and unnecessary communications are moved to the trash can, inboxes are still jam-packed with important attachments, electronic pay stubs, and critical...
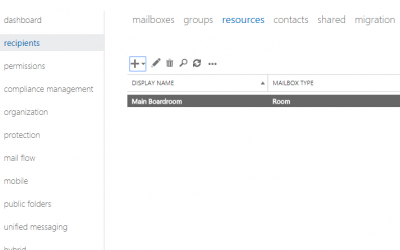
Setting Up Room or Equipment Mailboxes in Microsoft Outlook 2016
Every business has some sort of system for reserving company equipment and booking rooms for company meetings and events. However, these systems are usually disorganized and leave employees groaning. Whether the system involves an on-paper sign out sheet or basic...
ATTENTION US BUSINESS LEADERS: Are You in the Know About the National Cybersecurity Framework?
Mandated by Presidents Obama and Trump alongside the National Institute of Standards Technology (NIST), The Cybersecurity Framework is required for all Federal organizations and is becoming the baseline security standard for commercial organizations at all levels....
Major Internet Outage Cripples the United States
We are issuing a warning to businesses that there is a major internet outage being reported across the United States today. The issue is being reported by several major outlets including Comcast, Verizon, and AT&T. Comcast is calling it an “external network...
IRS ISSUES WARNING: American Tax Refunds Face Theft Due to Equifax Hacking Scandal
Equifax has been all over the news lately. Earlier this year, news of the massive hacking of the credit reporting agency has left the company scrambling to try and make sure client data is secured. However, the IRS has issued a recent warning to consumers that tax...
GIBON – The Next Ransomware Threat
The latest strain of ransomware — GIBON — is making the rounds; make sure your business knows how to protect against it. Ransomware is now a household name, and there’s no going back. Even though cybercriminals have been using ransomware for years...
Warning: Dangerous New Ransomware Attacks
GIBON is a new type of ransomware that first emerged on the scene last week and has since been utilized in a wide range of cyber-attacks. The main way this GIBON-variant is spread is by malspam with an attached malicious document, which contain macros that will...
Understand the Role: Becoming an A+ Compliance Manager
Becoming an A+ compliance manager may not be the most intuitive prospect, but with careful attention to what the role entails and the right IT help, you’ll get there. While most people assign compliance to the same snooze-worthy category as watching paint dry, it’s...
Windows 10 Creators Update is Your Company’s New Best Friend
The Windows 10 Creators update is in full swing and business owners have been soaking in the benefits. The update has been available since April and so far, it is living up to the hype. The update carries on the Window’s 10 mission to make IT more secure and...
Apple Update Leaves Users One-Step Forward & One Step Back
Latest Update Includes KRACK Patch but Comes Alongside News of iOS Zero-day Vulnerability On November 1st, 2017, Apple released its latest stream of updates for a variety of devices and programs across its product line. First and foremost, the update has a number of...
New York State Finance and Insurance Companies Are You Up-to-Speed on the Latest State Cybersecurity Regulations?
The New York State Department of Financial Services (NYSDFS) has issued an updated version of its proposed Cybersecurity Requirements for Financial Services Companies, known as 23 NYCRR 500. The recently unveiled regulation update comes following the mandates original...
Business in the Age of Cyber Attacks: Outsmarting Criminals with Robust Security Strategies
It’s no longer surprising to know that we live in a world where business networks are constantly at risk and under attack. With cybercriminals getting more organized and sophisticated, no company is safe from the potentially catastrophic impacts of a network breach or...
How To Manage Your Email
Learn how to implement the five-folder email system and get rid of email overload. It’s easy to become a slave to your email inbox. Unless you take control and implement a strategy, those emails can become just an unruly inbox, especially when you’re using email for...
The 5 HIPAA Compliance Sins You’re Unintentionally Committing … and How to Avoid Them
HIPAA compliance is critically important, but unfortunately not at all simple. Here are 5 deadly sins you might be committing, and the secrets to avoiding them. Okay, so we’ll admit, we’re pretty biased. We’re all about the strong, secure and streamlined managed IT...
Remember: Daylight Savings Time This Weekend
REMINDER: Daylight Saving Time Ends Sunday, November 5th: Make Sure Your Employees are Ready to Fall Back Safely When talking about Daylight saving time and business productivity, the focus is often placed on when Daylight saving time begins in the Spring. We lose an...
The Cyber Threat of the Future: Anatomy of an Internet of Things (IoT) Attack
Internet of Things (IoT) has been dominating conversations in the tech industry for some time now. The interconnectedness of an IoT network offers streamlining capabilities that are attractive to individuals and businesses alike. Using technology to make life easier –...
Help Employees Understand Cyber Threats
Companies can combat a lack of employee awareness about cyber-attacks by offering regular, consistent training, communication, and awareness A recent study by Wombat Security Technologies reveals some startlingly alarming insights about workers’ awareness of...
Which MS Office 365 Plan is Best for Your Business?
Which Version of Microsoft Office 365 for Businesses or Enterprises is Best for You? It’s easy for most businesses to justify a switch to MS Office 365. Microsoft keeps their apps updated and has a good reputation for providing robust, industry-standard...
Businesses Can Keep Google Maps and Search Updated With Google Posts
Use Google My Business to update your Google Maps and Google Search Listings at any time and for free. Have you ever wished you had a quick way to update your Google listings with new or timely news about your business? Google has rolled out a useful feature for all...
What’s Worse Than Halloween Horrors: How About Digital Security Horror Stories?
Digital Security Halloween Horror Stories: How to Prevent Tricks and Enjoy Only Treats Do stories about digital security horrors keep you up at night? As Halloween approaches, your thoughts might turn to goblins, ghosts, and ghouls. If you really want to give your...
We’ll Will Help You Recover From Tropical Storm Philippe
As your trusted IT service provider, we are available to provide any Business Continuity support needed by companies affected by the heavy rains and power outages across the northeast. The latest tropical storm to hit the US — known as tropical storm Phillippe...
The Increasing Importance of Maintaining HIPAA Compliance in Healthcare Organizations
Anyone who works in the Healthcare or Insurance industry is familiar with and must comply with HIPAA, the Health Insurance Portability and Accountability Act. The United States Congress enacted HIPAA in 1996 to create regulations that were designed to provide the...
The Benefit of Managed IT Services For Large-Scale Construction firms
Construction companies, be they large or small, have some unique aspects of their business that make them a different kind of business from others that rely on a managed service provider. With programs like CAD, construction project planning and procurement of...
13 Time Saving Shortcuts for Microsoft Word
These Microsoft Word shortcuts will save your fingers and your time with quick keyboard tricks and little-known Microsoft Office secrets. Whether you own an Apple or IBM product, chances are you will use Microsoft Word at home, at work, or at your friend’s...
Unveiling the Workspace of the Future: Is Your Business Positioned to Prosper for Years to Come?
Over the last few decades, technology has helped business owners of all kinds make giant strides. Whether it’s better serving clients, optimizing internal processes or driving increased profit margins, there’s no denying technology has played a key role in the...
5 Types Of Social Engineering Scams You Need To Be Aware Of
Social engineering tactics let hackers take cyber attacks to a whole new level by focusing on a specific target. This kind of special attention and extra detail can often be just enough to fool users into clicking, downloading, or otherwise helping a hacker get...
Meet Alan! Your Typical Small Business Owner
Alan owns a small business and he works hard every day to ensure his business is successful. Alan has realized that to be successful, he must be 100% focused on the things that matter…. Things like… … winning new business …. keeping his customers happy … managing...
The Very Latest Cyber Threats To Your Business
Whether in business, at home or out at play we are connected to the internet all day, all the time. We check our smartphones every five seconds. As a business, it’s much of the same thing. We are connected with the office, with clients, and with vendors. You...
Why Every Business Should Consider Outsourcing IT Services
There’s no denying that today information is more accessible and easier to obtain than ever before. From the internet, tablets, smartphones, and even your laptop information is everywhere and can be accessed from anywhere. But do we know all the ins and outs of...
Will Financial Service Institutions Ever Start Migrating Data to the Cloud?
Migrating business data to the cloud has been like a universal cure for a lot of businesses. Having vital information in the cloud allows a company to spend less on IT and infrastructure, which they can put into other projects. It also allows their employees to...
Symantec Users: Here’s the Inside Scoop on Bad Rabbit Malware and How to Stay Protected
A new and malicious strain of ransomware called Bad Rabbit, began spreading this past Tuesday October 24th, with most of the reported infections seen in Russia. However, because the Bad Rabbit virus is self-propagating, and can spread across corporate networks,...
ATTENTION SonicWall Users: Here’s Everything You Need to Know About Bad Rabbit Malware
Starting on Tuesday, October 24th, reports of a new strand of ransomware dubbed Bad Rabbit, began appearing in Russia and Ukraine. The virus is a wide-reaching and fast-spreading malware infection that initially targeted media and government institutions in Europe....
New Ransomware Attack Called Bad Rabbit
NotPetya Malware Refuses to Let Up – Latest Malware Variant Bad Rabbit Targets Business Owners and is Spreading Fast Since Tuesday, reports of the Bad Rabbit ransomware virus have been flashing across news screens everywhere. The virus started its rampage in Europe,...
How Accounting Software is Helping Countless SMBs Save Time, Money and Resources
It’s a familiar story and every business has been there. Deadlines are looming, customer requests are at an all-time high and to-do lists are longer than ever. Then, management remembers there’s a pile of overdue accounting paperwork that needs to be delegated and...
Bad Rabbit: Fast-Spreading Malware Threat Puts U.S. Businesses at Risk
Petya’s Latest Variant — Bad Rabbit — Leaves Companies in Shambles as It Spreads Worldwide; US Department of Homeland Security on Alert. Early Wednesday morning, leading anti-virus security company, Avast, reported that the Bad Rabbit virus – a variant of...