
by Felicien | Feb 6, 2019 | Education
You can create a data entry form in Microsoft Excel without using VBA or even recording a macro. If those terms don’t mean anything to you, don’t worry. You won’t need to learn them. Excel has a hidden tool you can use to make dreaded data entry fast and easy. Using a data entry form lets you view one record at a time while entering the data, but also makes it easy to analyze multiple records in a tabular format.
1. Open an Excel file.
2. Place the Form tool in your Quick Access Toolbar.
3. Click the Form command to bring up the data entry form view (no other step is needed for this).
4. Use the Find Prev and Find Next buttons to analyze your data one row at a time.
How do I Format the Data for the Data Entry Form?
To use the data entry form, simply put the data in the following format:
One record of data goes in each row in Excel.
Include column headings above the data.
You need at least one record prior to activating a data entry form.
How Do I Add the Forms Toolbar to Excel’s Quick Access Menu?
You can add the Forms… command to Excel’s Quick Access Menu for convenient usage. Here’s how to do that:
Press the options icon that lies to the right of your quick access toolbar.
Choose More Commands when the drop-down list appears.
Add the Form command to the quick access toolbar.
Go to the Choose commands drop-down list. Select Commands Not in the Ribbon from the list.
Scroll down until you come to Form… and click on it to highlight it.
Press Add.
This brings the Form… command in the rightmost box.
Press OK.
How Can You Analyze the Data?
Here are some quick tips for navigating the data block created by your entries.
Place the cursor anywhere inside your data block.
Each row has a single record.
Each column has a column heading.
Press the Form button in the quick access toolbar.
The data entry form activates, allowing you to view data or add records one at a time.
Use the Find Prev or Find Next button to surf through the records.
Add a record using the New button or delete existing records with the Delete button.
by Felicien | Feb 6, 2019 | Education
Ransomware. Ransomware. You have heard the word and know it involves a cyberattack. You assume from news reports that it only happens to large companies like Target, Equifax, and Marriott Hotels for example, and that cybercriminals will not want to bother with your small or medium-sized business (SMB). Unfortunately, that assumption is wrong.
The Federal Trade Commission (FTC) notes that ransomware is a major concern of small business owners across the country. Another report notes that since nearly 50 percent of SMBs have no employee security and awareness training, they are particularly vulnerable to cyberattacks, including ransomware.
The U.S. Department of Justice (DOJ) reports that since January 1, 2016, more than 4,000 ransomware attacks have occurred every single day. Business owners suffer the temporary or permanent loss of their proprietary information, disruption of their daily business operations, and the extreme expense of restoring files, if that is even possible. Their reputation in their community may also be damaged.
What is Ransomware?
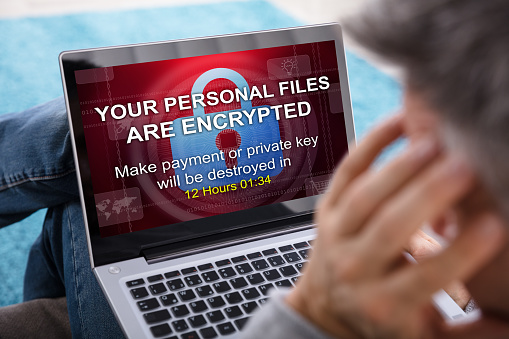
Ransomware is a type of malware, a software program intended to damage computer files. It quietly invades your computer, encrypting as many files as it can locate on your local and network drives. The encryption is done by using a complex mathematical algorithm. When the encryption is complete, your files become unreadable unless you have the key to unlock them.
The only one with the key is the cybercriminal who demands you pay a ransom in order to regain access to your files. Your data has been kidnapped. A simple virus scan cannot undo the encryption. Your data is being held hostage by the cybercriminal.
In many cases, there is a time limit for payment. A count-down clock may even appear on your screen telling you that you must pay the ransom within a certain period of time or forever lose access to the files.
How Ransomware Gets into Your System
Ransomware enters your computer most often by a “phishing” approach. This happens when an innocent user receives an email that appears to be from a friend, co-worker, or reputable company. It includes an attachment. When the user clicks on the attachment, it is downloaded and, voila, ransomware invades that device and all other devices connected to the network.
Some websites have malware lurking in the background. It only takes one keystroke and the malicious software will now infect all the files it can access. The intent is to cause as much damage as possible to your network so that it shuts down and you can no longer access any of your files.
Should you Pay the Ransom?
The DOJ does not advise SMBs to pay the ransom. But, it does note that victims of ransomware have tough decisions to make when considering whether or not to pay. It recommends ransomware victims consider the following factors before paying the ransom:
How to best protect employees, customers, and shareholders.
Paying the ransom does not guarantee that the cybercriminal will provide the key to decryption.
Some victims who paid the ransom and did get the decryption key were again targeted by other cybercrminals.
The DOJ encourages businesses who have been invaded by ransomware to report it to law enforcement. There is a chance that they can use legal tools, including working with international law enforcement, to locate the encrypted data.
How to Prevent Ransomware from Invading Your Network
The most important step of preventing ransomware from invading your network is education. Your employees need to understand how ransomware works, and they need to be constantly aware of the importance of not clicking on any attachment no matter how legitimate the sender appears to be. The attachment must first be scanned for malware.
Every file needs to be backed up so it is accessible off of the network so that if there is a ransomware attack, your business is not crippled beyond repair. If an attack is discovered on one device, immediately shut down all devices connected to the network.
Cybercriminals are getting smarter and learning how to circumvent cybersecurity that is installed to prevent the ransomware and other malware attacks. There are Managed Service Providers (MSPs) who can provide a robust cybersecurity system that can withstand the threats. They should also be able to ward off a threat before it can cause any harm.

by Felicien | Feb 4, 2019 | Education
Making sure the employees that rely on computer systems are trained in cybersecurity is the easiest way to avoid compromising attacks. However, only about 45 percent of business organizations actually make sure their employees are properly trained through mandatory training, and roughly 10 percent make cybersecurity an optional training. This information is alarming for a lot of reasons.
Most Attacks Happen via the Compromise of an End User
Primarily, this new study means that 55 percent of organizations do not think their end users have a big enough role to play in keeping their network safe. In actuality, the end user is usually where systems are compromised in business settings. Phishing messages and other business security threats target people opening emails, performing things on social media, and doing basic functions that end users tend to do. Even if business owners do train their higher-ups, such as management members and team leaders, there is a major risk if the typical system users are not properly trained.
Formal Security Training Is a Struggle in Most Business Settings
Even organizations that offer security training as a mandatory thing to all system users in the work environment, most do so in a limited fashion. According to Mimecast, only about six percent conduct cybersecurity training sessions or courses on a monthly basis. Four percent of business owners do training four times a year, and nine percent only require training when they bring in a new hire. Surprisingly, many places don’t really offer any kind of formal cybersecurity training; they just send out a mass email of tips on occasion.
Employees Are Often in the Dark Where Cybersecurity Is Concerned
Because business owners are not taking the time to ensure their team members are adequately trained in cybersecurity, employees are left in the dark about the threats that could be sitting in wait when they log in to the company system. Studies actually show that one out of four employees have no idea what some of the most common cybersecurity threats are, let alone what they look like or how to avoid making major mistakes.
Considering that one in ten employees are using devices at work, connected to the work network, for personal reasons for at least four hours a day, the aforementioned facts show just how relevant cybersecurity training should be to all team members. Team members may be checking personal emails, hitting up social media sites, or otherwise doing things that could leave companies wide open for an attack. Even if the risks are handled through intranet email, for instance, threats can still get through on other email platforms that an employee uses on a network device.
Implementing Cybersecurity Training Does Not Have to Be Difficult
The majority of business who do not have a good cybersecurity training plan in place avoid the process because they believe it will be too time-consuming. Some wrongly assume that formal training really is only necessary for people who have higher ranks in the company, which is obviously not true. Implementing a good training plan does not have to be a difficult or time-consuming thing. A few ways to incorporate a good training plan include:
Working with a cybersecurity company who provides employee training material with their services
Making cybersecurity a mandatory part of other training processes, such as safety training
Creating basic cybersecurity training modules employees can do in their spare time throughout the day
Handing out informative resources and worksheets on cybersecurity threats and protection
In addition, cybersecurity training should be an ongoing thing. Threats are always changing and evolving by the day as criminals get smarter with every thwarted attack or exposed risk. Therefore, it is critical that business owners get proactive about training and make it a priority over the long term. In the long run, this can be a change that saves the livelihood of the business from a serious cybersecurity attack.
Overall, cybersecurity training should be just as important to a business operation as any other form of training. In 2017 alone, cybercrime cost the world an estimated $600 billion, according to CNBC. If you believe your business is not adequately training all employees in cybersecurity, reach out to a cybersecurity training or consulting company for advice.

by Felicien | Feb 4, 2019 | Education
Excel’s ready-made formatting styles bring life and color to your spreadsheet. It lets you give printed versions a polished, professional look. Color coding makes it easier for audiences to interpret your data. Use this neat feature to take your worksheets up a notch.
What is a Preset Excel Style?
A cell style puts together font size and style, number formatting, borders and shading into pre-fab-style packaging you can apply with the click of a button. The software comes with built-in options in a variety of palettes to suit almost any taste. Once you become more familiar with them, you can customize cell styles and make them available in all your workbooks.
Keep in mind that cell styles are affiliated with the theme of your document and applied to the whole workbook. If a document’s theme is changed, the cell styles change as well. Also, you can use the lock cells feature to prevent other users from modifying the styles used in your workbooks.
How Can You Apply Cell Styles?
It’s relatively easy to apply cell styles to jazz up workbooks and impress your internal and external clients. Just follow the steps below:
Select a range of cells to format.
On the Home tab, click on Cell Styles to view a gallery of style choices.
Click on the cell style that fits your spreadsheet or personal preferences.
How Can You Create Your Own Cell Styles?
You can also create customized styles that reflect your company or personal branding by taking the following actions:
Select a single cell in your worksheet.
Apply your favorite formatting options to the cell. A built-in style may be the easiest starting point. Then, you can tweak it to add your own flair.
Click the Home tab on the ribbon and choose Cell Styles to access the Cell Styles Gallery.
Now, choose the New Cell Styles option (It’s near the bottom.)
Enter the name for your new style in the Style name box.
Excel lists the formatting options applied to the selected cell for your reference.
How Can You Modify an Existing Cell Style?
To preserve the built-in styles, it’s safest to duplicate them and then make your modifications to a saved style. However, you can make changes to pre-set and custom styles, as follows:
On the Home tab, select the Cell Styles icon.
In the Cell Styles gallery, right-click on any cell style, then choose Modify to access the Style dialog box.
Click the Format button to reach the Format Cells dialog box.
Use the various tabs to apply your changes and click OK to get back to the Style dialog box.
In the Style dialog box, under Style Includes, clear the check boxes of formatting elements you no longer want.
Click OK to exit the dialog box.
This takes you back to your worksheet and the modified cell style should now reflect the changes.

by Felicien | Feb 4, 2019 | Education
In Australia, citizens fear a terrorist attack or another national emergency just as much as the next country. For this reason, Australia has what’s called the Early Warning Network or EWN for short. Recently, a hacker was able to breach this system and took it over. The result was terrible in that it caused widespread panic. But it was also catastrophic in that it lessened the confidence Australian citizens have in their Early Warning Network system.
A Breach of Australian National Security
The breach of the EWN occurred on January 5, a Saturday evening. Hackers had somehow breached the EWN system and sent out an unauthorized alert to thousands of Australian citizens. Today, experts at the EWN have confirmed that their system was hacked. They say that an unauthorized individual somehow obtained login credentials for the system. Some of the EWM’s customers received a spam notification. The notification went throughout the entire country of Australia.
The notification read:
“EWN has been hacked. Your personal data is not safe. Trying to fix the security issues.”
Also in the message was an email address. The email address was alongside a prompt that users could unsubscribe to the EWN service. In addition to being posted on the website, the message was also sent through landlines, via text, and over email. Throughout Australia, tens of thousands of individual citizens use this service to get information from the government. All levels of the Australian government use EWN.
Right away after the attack, EWN understood that there was a breach in their security. They sent out a message and posted it on their Facebook page. It read:
“At around 930pm [A]EDT 5th January, the EWN Alerting system was illegally accessed with a nuisance message sent to a part of EWN’s database. EWN staff at the time were able to quickly identify the attack and shut off the system limiting the number of messages sent out. Unfortunately, a small proportion of our database received this alert.”
Contrary to what the original message from the hacker said, no one’s personal information was compromised. Only white page information could have been accessed, such as basic address information. Representatives from EWN also stated that some local, state, and federal government agencies were affected by the hack, but not all clients who subscribe with EWN were affected.
EWN was able to regain control of their services directly after the attack and are investigating the issue to prevent further breaches.
The Importance of Fortified IT Security in an Age of Rampant Cyber Hacking
It is common knowledge that the majority of businesses — no matter whether they are private, publicly funded, government related, or otherwise — are at risk of being hacked. Furthermore, hackers from around the globe are improving their techniques for accessing your private data and information.
This often begins with breaching the system by obtaining login credentials from individuals who already work or subscribe to a specific company, business, organization, or government agency. Naturally, this information is not given up willingly. Instead, it is obtained in a conniving and sneaky way so that the person giving up the login information doesn’t realize what they’re doing. Email phishing and phone call phishing are the top two ways that hackers obtain login information.
Chances are, your business organization is not completely safe from cyber hacks like the one that happened to EWN. Consider hiring an outsourced IT service provider who can improve your company’s security and prevent breaches from occurring.




