
by Felicien | Jul 12, 2019 | Education
Habits You Want From Your Technology Partner
When you are running a business, you want your technology to integrate well with the other tech you use in your business and with your overall IT platform. When you run into situations where your tech fails to integrate well, it can cause serious problems—leading to lost productivity, lost data, and general inefficiency that is not desirable for any business.
Choosing technology partners requires looking carefully at how those partners play with others. You want to know that your tech will integrate and operate well, which means you want a tech partner that is interested in ensuring cross-compatibility and integration. Many tech partners will be interested in such cooperation, but not all will. It is important to know what to look for in such a partner to ensure that you team up with a business that you can rely on.
Tech Partner Habits—Must-Haves from a Tech Partner
1. Interest in improving the overall experience, not just the bottom line
There are plenty of tech partnerships that develop to increase profits. After all, money drives business and it only makes sense for companies to seek arrangements that will improve their profitability. But creating the best customer experience requires more than just a focus on profitability—it also requires a real and sustained interest in ongoing improvement, which necessitates cross-pollination.
You want a partner who wants to ensure that everything works and strives to avoid tech silos that inhibit customers and companies alike. However, you also want a partner who will offer ideas for improvement and accept constructive feedback for their own improvement. The sharing of knowledge and insight and interest in such sharing makes a great tech partner.
2. Willingness to be part of a team
It may seem like asking too much for a tech partner to treat your business and the other tech vendors you work with as a team—but the fact is, you need a team player to achieve your goals. Sure, it can take some serious self-reflection on the part of one business to decide to team up with another business and actively engage in such teamwork, especially if there is a fear of missing out on extra earnings. But the long-term benefit of teamwork will yield future rewards that are otherwise unachievable. The tech partner that is willing to forgo a little extra profit today for benefits for the entire team, later on, is one worth keeping.
3. Interest in a long-term partnership
Many of the best results are only achievable through long-term planning and implementation. Some tech partners may see the option of a partnership as more of a short-term advantage that is not worth maintaining for the long-term. These potential tech partners fail to realize that whatever short-term benefits they can get now will pale in comparison to the benefits they could realize through long-term engagement and partnership. Of course, the challenge of long-term relationships is that they typically require some sacrifice on the front-end. Tech partners that are wise enough to see the value in such early sacrifice are more likely to benefit your business in the future.
4. Desire to contribute to the partnership
One of the best ways to facilitate a successful partnership in technology is to give as much access to your technology base as possible. There are many reasons for this need. For example, by giving as much open access to their technology base and IT stack as they can—within reason—a tech partner can make it much easier and faster to develop integration between their tech and the tech of other partners. The harder partners have to push to gain access to the information they need, the longer it will take to achieve true integration. It is possible that with enough pushback on access, a partner could just give up on the idea of achieving integration and go somewhere else.
5. Seek regular and open communication
The need for communication in business is significant when partnering with tech vendors and service providers. You want a company that will keep you up to date about everything that is going on—at least all the things that are relevant to you and your business—and you want a company that will take your need to communicate seriously. When you want to communicate, your partner should be available or make themselves available at a reasonable time. You also need to know what your partner wants and expects out of the business relationship, just as your partner should know what you want and need out of the partnership.
by Felicien | Jul 12, 2019 | Education
Microsoft’s Hyper-V Server 2019 Finally Released
After being plagued with everything from data loss issues to a lack of available hardware, Microsoft finally released their long-awaited Hyper-V Server 2019 to their Evaluation Center approximately eight months after the expected release date of October 2, 2018. This is even after the Microsoft team skipped the crucial RTM (“release-to-manufacturing”) stage that allowed hardware developers to deploy and test adequately, forcing a holdup before organizations could even utilize the update. The mysterious delays of this free enterprise-class server virtualization solution may make users a little wary, but the functionality offered may simply be too tempting to overlook the release.
What Is Microsoft Hyper-V Server 2019?
Microsoft’s Hyper-V Server 2019 is a free product that is meant to compete directly with VMWare, providing enterprise-class virtualization for your datacenter and hybrid cloud, according to Microsoft’s Evaluation Center website. Essentially, you’re able to quickly scale and balance workloads to meet the demanding performance requirements of today’s data-heavy businesses. The release contains the Windows hypervisor technology as well as a simple and reliable virtualization component and a Windows Server driver model. The product is intended to help reduce costs and improve overall server utilization. You can easily compare Windows Server versions in this free online tool from Microsoft.
“We Found Some Issues with the Media”
Microsoft’s bland explanation of why they quickly pulled Windows Hyper-V Server 2019 from the Evaluation Center almost immediately included this note on their blog: “As we were getting ready to publish Microsoft Hyper-V Server 2019 in the Evaluation Center, we found some issues with the media. We are actively working on resolving it”. This was after the software giant released the Windows Server 2019 evaluation media, minus the Hyper-V Server portion of the package. While it’s fortunate that Microsoft immediately discovered these issues before the software was widely implemented, there were still some critical features that users had been anxiously awaiting for many months. It appears there were some issues with Remote Desktop Protocol and media installation problems, too.
While it seems that all of the glitches have been safely ironed from Microsoft’s latest release, wary users may want to give the platform a few months before launching into full utilization. After more than seven months of delays, Microsoft has left fans wondering if they’re preparing to phase out the popular — and free — tool in the future.
by Felicien | Jul 11, 2019 | Education
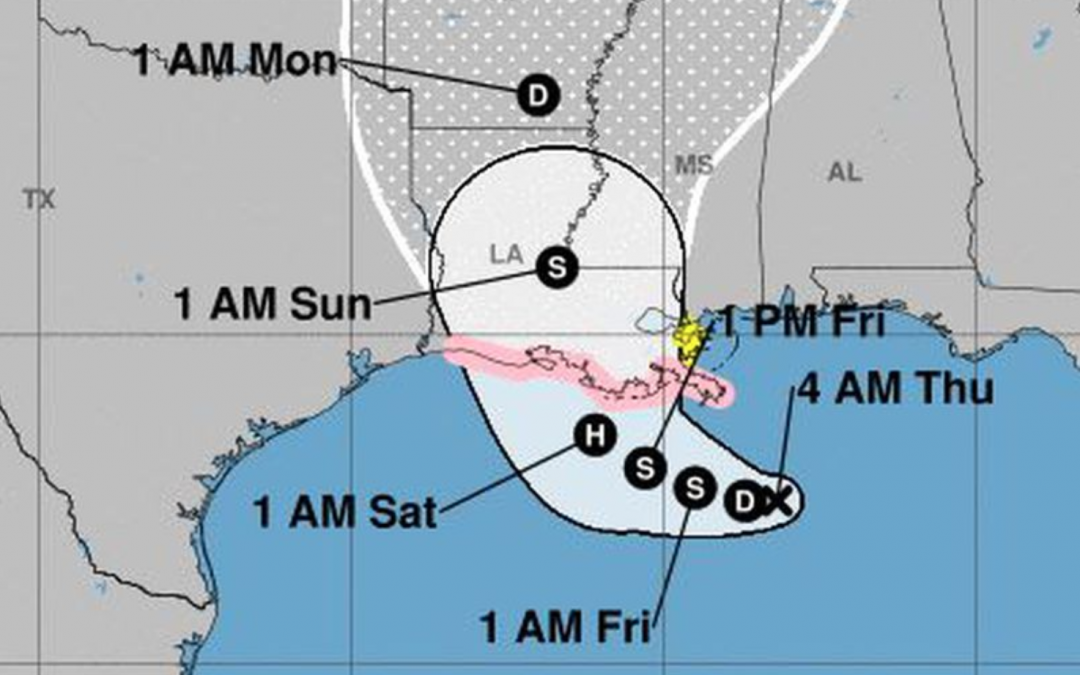
Tropical Storm Barry is expected to hit Louisiana and Texas in just a few days – what steps can you take right now to make sure you’re prepared?
As of yesterday, parts of coastal Louisiana have been put on hurricane watch in anticipation of what could be the first tropical storm system to make landfall in the US this year. Watches apply specifically from the mouth of the Mississippi River and west to Cameron, LA.
Tropical Storm Barry is expected to form in the Gulf of Mexico and develop into a hurricane by this Saturday, at which point it is likely to head through Louisiana and the upper Texas coast.
If you’re located in an area for which a watch has been issued, what steps can you take right now to protect your business?
Develop A Hurricane Preparedness Plan
Your hurricane plan should be carefully constructed and written down for reference and review.
Your plan should put forth policies and procedures regarding employee safety, business continuity, and contingencies that can be activated if your business’ facilities are damaged.
There are three key steps to an effective Hurricane Preparedness Plan:
Protect your property.
While so much of disaster recovery these days is focused on data continuity, it’s important to remember that your facilities are a resource as well, and they should be protected.
Make sure your windows have proper shutters or are boarded up with plywood to keep them safe from airborne debris.
Inspect your roof prior to each hurricane season to make sure it’s in good shape.
Assess whether there are any aging branches or trees that could fall and cause damage during a storm. If you’re unsure, have an arborist check it out for you.
Bring sandbags to areas that could be affected by flooding.
Secure heavier objects, including bookcases, shelves, filing cabinets, computers, etc.
Secure utilities, and raise them off the ground if necessary to avoid flood damage. Prior to the hurricane reaching your area, make sure they’re all turned off.
Relocate any fragile or valuable items to less dangerous areas, if possible.
Protect your documents.
Once all your physical assets are taken care of, don’t forget about your business documentation.
Make sure you have a backup of info on important business contacts.
Backup documents that are not easy to reproduce or acquire in the event of water damage – insurance and legal contracts, tax files, etc.
Keep as much of your documentation as possible in waterproof containers.
Maintain a checklist of survival resources.
Lastly, you’ll want to make sure you have an inventory of all the hurricane-specific resources you’ll need.
These are the types of items you won’t be using otherwise year-round, and so, when you do require them, you don’t want to realize you’ve forgotten something.
Independently powered radio/TV
Three-day supply of non-perishable food for as many employees as you have onsite (including 1 gallon of water per person per day)
Blankets, pillows, cots, and chairs
First Aid supplies
Flashlights (and additional batteries)
Toolkit
Whistles and/or signal flares
Tarps, plastic bags, and duct tape
Cleaning supplies
Smoke alarms and fire extinguishers
Electric generator
A backup supply of gas and additional jerry cans
Cash, credit cards and ID
Emergency contact info
Don’t forget to brief your employees – your hurricane plan should not be written and then left on a shelf. Every employee should be familiar with your procedures and plans to handle any future emergencies. Hold a meeting where your plan is reviewed, roles are assigned, and your staff can ask questions.
Remember – without comprehensive disaster recovery planning, you’re left vulnerable to any and all emergency situations, whether it’s a major meteorological event like a hurricane, or common — and still unpredictable — power outages. Consequences include:
Permanent data loss as onsite copies of your data are destroyed
Severe downtime as your business scrambles to replace hardware and get up and running again
Major financial damages, from the cost of lost business to the cost of replacement hardware and more.
There are still a few days until the hurricane is expected to hit – follow these steps and develop your plan now to make sure you’re prepared.

by Felicien | Jul 11, 2019 | Education
Cybercriminals may be going into a stealth mode, but that doesn’t mean that cyberattacks are slowing down — quite the opposite, in fact. According to the 2018 SiteLock Website Security Report, attacks increased by 59% and accelerated going into December. Record numbers of businesses are being infiltrated by hostile actors, with data breaches affecting hundreds of millions of users in a single attack. This all comes during a time when cybersecurity costs are accelerating as more organizations scramble to bring expensive systems and well-paid IT assets online to help protect their business from attack or assist with recovery. By the year 2021, damage to businesses is expected to exceed $6 trillion annually from cybercrime alone. It’s becoming increasingly difficult for businesses to manage the complexity required for a comprehensive cybersecurity plan alone, but these basics will give you a starting point to managing the risk to your organization.
Understanding “Current State” Security Practices
Many organizations begin crafting their cybersecurity plan by reviewing and documenting the current state of their risk-reduction efforts. This could include everything from data structures and storage locations, physical and cloud-based infrastructure models, third-party vendors and other connections. This “current state” report gives you a comprehensive view of the organization and allows you to capture potential risk centers that will need to be addressed in the future.
Balancing Security Needs with Business Requirements
It’s a fact of life that IT professionals are often in top demand, making it difficult to implement the full range of cybersecurity protections that proactive leaders feel are necessary. This balancing act may take place as ongoing negotiations between business and technology teams as the risks of not taking specific steps to tighten security are weighed against the potential benefits of new functionality. IT teams need to have a full understanding of how data and applications are utilized throughout the organization, including how remote partners or staff members are connecting into business applications and databases. Going through this process prompts conversation around the replacement value of particular platforms. Where an IT team may feel that an older platform could be deprecated without undue business impact, one particular unit may be utilizing that data in an unexpected way. In this instance, business and IT leaders will have to negotiate whether it makes sense to enhance the security or simply move to a newer alternative.
Crafting Your Plan and Training Your Staff
Understanding all of the various assets that your business has available allows you to gain a more holistic view of the business, a crucial element of any successful cybersecurity plan. Define replacement or bypass recommendations for each of your core business assets, and then fully document any changes that need to be made to reduce the risk of a breach or the effect of any malware or ransomware attacks. Having the plan in place also requires determining the training level that your staff will need. According to Cisco, the majority of malicious file extensions are made up of popular files such as Microsoft Word, Excel and PowerPoint, making ongoing training an important part of any cybersecurity strategy.
Small and mid-size businesses are the organizations least likely to have a formal cybersecurity plan in place, but these businesses are a high-risk target that is extremely attractive to hackers. Managing the complexity associated with the various platforms and data sources is often cited as a significant challenge for over-taxed IT personnel. Making regular cybersecurity reviews a priority can help your organization not only stay safe online but also identify processes challenges that need to be addressed to improve operational efficiency. Even with a rock-solid cybersecurity plan in place, that doesn’t mean your organization is completely safe. Instead, it means that you’re ready for an attack and are able to respond appropriately and in a timely manner — which can save your company hundreds of thousands of dollars in the event of a breach.

by Felicien | Jul 11, 2019 | Education
Windows 10 comes a step closer to preventing cyberattacks and privacy threats facing users. It’s a next-generation solution that helps you fight threats from hackers and criminals who target your business. This is a big plus for cybersecurity managers. The past several years have brought some of the worst and most frequent cyberattacks in history. Security professionals are constantly on the lookout for new ways to prevent network breaches and safeguard the data of clients and the enterprise. Let’s take a closer look at how Windows 10 can help.
What Are the Security Advantages of Window 10?
Microsoft introduces Windows as a service in this version of their OS. It includes a unique way of creating, implementing and maintaining Windows. Each update adds new features to protect the security and privacy of users. The idea is that protection is layered into the functionality so that it doesn’t affect performance or distract users.
Windows; Core Services Engineering and Operations is thus better able to protect data and privacy. Built-in features identify suspicious activity that can put your business in jeopardy. This helps your security team detect and block sophisticated attacks faster. Releases focus on adding new features that combat new or anticipated risks. This is all possible thanks to the software giant’s finger on the pulse of the latest ransomware and malware hitting around the globe.
Windows 10 is considered to be the most secure version yet released. Because Microsoft has addressed cyberattacks during the engineering phase, improved security itself becomes a major bulwark, protecting your system from files and executables sent by hackers.
How Does Windows 10 Protect Your Data Better?
Here are some of the ways that Windows 10 improves its protection, including the new tools that can detect threats:
Windows 10 disrupts malware and thwarts hackers by changing the playing field. Bad actors can’t attack systems in the same old ways.
Device Guard acts as a shield against malware by allowing you to block unwanted apps. This gives users a proactive way to prevent ransomware and malware attacks as well as spyware.
Windows Defender uses machine learning, the cloud and behavior analysis to respond to new threats. This is like having a smart guard dog that not only prevents intruders from entering but smells them coming a mile away.
Microsoft Edge systemically disrupts malware, phishing and hacking attacks so that fewer threats make it through the system to trick users.
Windows 10 has aggressive data protection that meets compliance requirements without slowing down users, who expect the same solid performance Windows has always offered.
Windows Information Protection contains business data so it cannot be leaked to unauthorized users via apps, docs and the web.
BitLocker helps your security team protect sensitive data from prying eyes. Military-grade encryption takes over when a device is lost, stolen or otherwise compromised.
Azure Information Protection partners with Windows Information Protection to assign permissions that govern how certain data is shared.
What Ways Does Windows 10 Protect User Identify?
Windows 10 has built-in identity and access management protocols. This advanced technology safeguards user identities. For example, Windows Hello presents an alternative to passwords. It uses many factors to achieve solid security, such as a PIN, biometrics and a companion device.
Credential Guard uses NTLM-based authentication protocols, while Windows pass the hash (PtH) method authenticates without displaying the user’s text when a password is being entered. There’s also a hardware-based component that also limits access.
What Does This Additional Protection Mean for Security Teams?
While 57% of organizations offer training and incentives to security recruits, it’s hard to keep these resources for very long. This is due mainly to the high demand for qualified candidates. With additional protection built into applications themselves, busy cybersecurity teams can concentrate on other crucial tasks to protect the company’s data and reputation.

by Felicien | Jul 10, 2019 | Education
Ransomware attacks have caused business interruption and other lingering damage to Australian small- and medium-sized business, enough damage that 22 percent have been forced to close after an attack. Ransomware attacks have paralysed business operations so much so that new research has reported that 31 percent of organisations have yet to determine how they were infected.
A Telstra survey of IT professionals from more than 300 Australian companies found 48 percent of those surveyed had experienced a cyber attack in the past 12 months. This is up from 33 percent in 2018. Of those who suffered an attack, 81 percent experienced a ransom incident, and 51 per cent of them paid it.
What Does Research on Ransomware Attacks Show for 2018?
A yearly study, Malwarebytes Labs State of Malware 2019, has confirmed that potential damage from ransomware attacks extends far beyond the original ransom. Ransomware isn’t the same wide-ranging threat as it was in 2017, however it’s still a sizable problem. Overall trends have shown a drop in volume for the year (Jan – Nov 2018), but an increase in focused, sophisticated attacks aimed at businesses.
How Does Ransomware Affect Consumers vs. Business?
Overall ransomware attacks have dropped when measured against attacks in 2017. In 2017 the study recorded 8,016,936 attacks across businesses and consumers globally. Compare that to 2018, where there were 5,948,417 detections recorded—a decline of 26 percent.
Given that businesses house so much more valuable data and critical systems, they are proving to be a more profitable ransomware target for criminals. Not only do they have the potential funds to pay a ransom, they’re also likely to have multiple pressing reasons for wanting to get back to work. Ransomware delays can be incredibly costly, especially when an affected organisation has no backup plan in place and multiple endpoints to remediate. Incident response and digital forensics all add to the cost, which is often a lot more than simply paying the ransom.
Which Industries are Targeted by Ransomware the Most?
You might be wondering which industries are popular targets for ransomware? Which verticals took the hardest hit? Malwarebytes’ data shows that consulting is the top contender, and education is second place. Here are industries listed in order of most targeted to least targeted:
Consulting
Education
Manufacturing
Retail
Government
Transportation
Telecommunications
Electronics
Healthcare
Technology
Although there were major stories throughout 2018 regarding healthcare and government ransomware attacks, other industries actually felt the brunt of the ransomware menace.
Which Ransomware Viruses Caused the Most Problems in 2018?
SamSam
SamSam caused chaos across medical networks in the US, exploiting and brute-forcing its way into systems to make over $1 million US dollars ($A1445300) for holding systems to ransom. One of its many older variants revamped to be more appealing to criminals, charging victims a more moderate price than alternative recovery methods, making significantly more money as a result. From January to March, SamSam took down everything from hospitals to city services, including departments of transportation and city-facing applications in Atlanta, Georgia. Additional major attacks took place in September, with both the ports of San Diego and Barcelona suffering outbreaks.
Although law enforcement agencies believe they know who is behind these infections, the alleged duo are still at large, and we still continue to see spikes in attacks globally. SamSam will continue to be a strong source of malware infections well into 2019.
GandCrab
GandCrab was also a major player in 2018, making use of various exploit kits shortly after its first appearance in January. Numbers steadied and remained constant for most of 2018, with a huge spike of activity in February, thanks to multiple spam campaigns in Q1. Moving to the Magnitude exploit kit for distribution, GandCrab continued to cause trouble for network admins and home users. This is partly thanks to Magnitude’s unconventional malware-loading methods. Everything from fileless techniques to binary padding (where extra data is added to files to bypass scanning) were used in the race to make it the biggest source of GandCrab.
GandCrab, the top ransomware variant of Q2 2018, is also notable for being the first ransomware to ask its victims for a cryptocurrency payment other than Bitcoin. At a time when business ransomware detections were up by 28 percent, but the overall volume remained low, it became one of the leading sources of malicious ransomware campaigns in 2018.
How Does Ransomware Compare to Other Malware?
Although ransomware has lost ground to other malware players, such as cryptominers and Trojans, it still causes quite a bit of damage, and 2018 has been a year of quiet experimentation and reassessment. The public at large are much more aware of such attacks now, and the same old tricks won’t work forever. Expect to see more innovative reworkings of older files and strengthened ties to cutting-edge exploit kits to push ransomware further still in 2019. The Australian Government tracks malware attacks on the Australian Cyber Security Centre for the public to stay updated.





