by Felicien | Jan 30, 2018 | Education
Not only are healthcare organizations at risk due to cybercrime, so are their patients. Imagine having to turn away patients because your computers are shut down due to a ransomware attack. Or, having to “blindly” treat your patients because you can’t access their medical records unless you pay criminals a ransom. A ransomware attack can halt your workflow, data processing and jeopardize your ability to properly treat your patients.
Patient data is now a popular target for cybercriminals. It can easily be monetized, making healthcare organizations and practices increasingly vulnerable. Believe it or not, ransomware poses even larger risks to patients than failure to properly disinfect medical devices. According to the ECRI Institute:
“This is the first year ransomware has been included in the ECRI Institute’s Top 10 Health Technology Hazards list,” says Juuso Leinonen, senior project engineer at the health devices group. “Cybersecurity topics have been covered in the past, but this is the first year a cybersecurity topic has been ranked No. 1 on the list.”
A New Ransomware Threat–”Defray”
Cybersecurity experts discovered a new ransomware threat that targets healthcare organizations. Defray uses Microsoft Word attachments in emails to infect a network. In one instance it attacked a hospital in the U.K. using an attachment entitled “Patient Report.”
The email looked legitimate because it included the hospital’s logo and the name of the director of information management. Once the attachment was opened, the victim’s files were encrypted.
Defray includes a note asking for $5,000 in bitcoins to return the encrypted files. It also suggests a victim contact them via three email addresses if they have any questions, doubts or want to negotiate. The email addresses contained domains from Russia, Germany, and Switzerland.
There are no tools available to restore files encrypted by Defray. The only thing you can do is restore your files from a recent backup. Unfortunately, some healthcare providers aren’t doing all they can to prevent ransomware attacks, or even backup their data properly in the event their patient information is held ransom.
Medical Devices Are Also Under Attack.
According to a May 2017 article in Forbes, medical devices were hit by ransomware for the first time In U.S. hospitals:
“When the NSA cyber weapon-powered WannaCry ransomware spread across the world this past weekend, it infected as many as 200,000 Windows systems, including those at 48 hospital trusts in the U.K. and so-far unnamed medical facilities in the U.S. too. It wasn’t just administrative PCs that were hacked, though. Medical devices themselves were affected too.”
The Food and Drug Administration is especially concerned about the safety of medical devices. Suzanne Schwartz, M.D., associate director for science and strategic partnerships at the FDA’s Center for Devices and Radiological Health, writes:
“A computer virus or hack resulting in the loss of or unauthorized use of data is one thing. A breach that potentially impacts the safety and effectiveness of a medical device can threaten the health and safety of an individual or patients using the device.”
Manufacturers, hospitals, and other facilities must work to prevent these pervasive cybersecurity threats. With the development of innovative technologies, protecting patients’ safety from malware attacks must be a priority. However, this is difficult when hospitals and healthcare centers use many different types of medical devices from a multitude of vendors.
The Solution? – A Defense-in-Depth Strategy
Mitigating the risk of data breaches and malware infections requires professional IT service and support from experts who are up to date on the latest cybersecurity threats and who utilize defense-in-depth strategies.
Originally coined in a military context, the term refers to an even more comprehensive security strategy approach than layered security. If one layer of protection is breached, the attack can be defended with one or more of the other layers. Layered security is only one part of a defense-in-depth strategy.
Defense in depth addresses a broad range of tactics to mitigate ransomware and other threats to data security. It comprises:
Monitoring, alerting, and emergency response,
Accounting of authorized personnel activity,
Disaster recovery,
Reporting of criminal activity, and
Forensic analysis.
Defense-in-depth security means recognizing that no one security solution is ever enough for healthcare organizations. The best cyber security experts find the right combination of new and tried-and-true techniques and tools that address the organization’s unique security and privacy requirements.
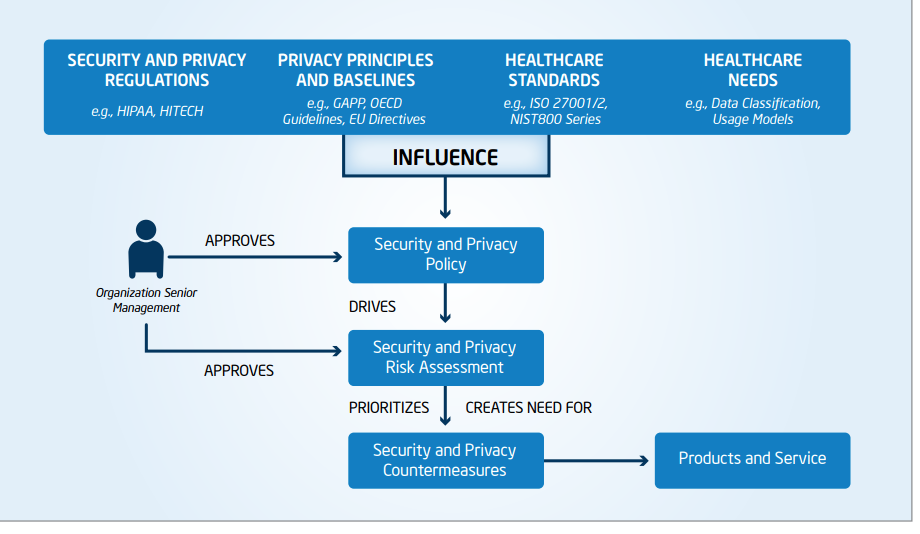
The diagram below depicts the guidelines suggested by the International Standards Organization’s ISO 27001 and ISO 27002 for Information Systems Management Security and Security Techniques, and principles such as the American Institute of CPA’s Generally Accepted Privacy Principles (GAPP) to determine security and privacy requirements.1
Only with a multi-layered, defense-in-depth strategy can healthcare organizations guard against patient safety infractions and best address the ever-increasing and evolving forms of ransomware.
Hopefully, this won’t happen, but if your hospital or healthcare facility is ever victimized by ransomware, be sure to contact the HHS for guidance.
For more information about Ransomware and Defense-in-Depth protection for your organization, contact {company} at {email} or {phone}.
1. Intel: “Health Information at Risk: Successful Strategies for Healthcare Security and Privacy”
http://www.ehealthnews.eu/images/stories/pdf/successful_strategies_for_healthcare_security_privacy.pdf

by Felicien | Jan 29, 2018 | Education
More than 20 years ago, retail began to shift from the shopping mall to online shopping. Amazon.com, the brainchild of Jeff Bezos, had been around for a few years. It was born as an online bookstore in 1995. A brilliant premise, Amazon offered a digital “storefront” that ran from the garage of Bezos’ home. Amazon’s virtual catalog represented nearly a million titles sold at prices lower than competitors’ due to wholesale agreements with major publishers.
After only two months, Amazon.com was bringing in US$20,000 weekly in sales. Its first sale was a copy of Douglas Hofstadter’s Fluid Concepts and Creative Analogies: Computer Models of the Fundamental Mechanisms of Thought. Just two years later, Amazon launched an IPO at US$18.00 per share.
Did you know that today Amazon trades at over US$1,300 per share on the New York Stock Exchange?
Mere days before its IPO, Amazon was sued by Barnes & Noble—They alleged that Amazon was operating under the pretense of being the world’s largest bookstore. They claimed that Amazon didn’t have inventory, rather they resold on behalf of publishers. Plus, Amazon’s habit of hiring former Walmart executives led to accusations of stealing trade secrets. As a result, Amazon soon restructured internally. What it didn’t change was its business plan, famously modeled after an “expansion- at-all-costs” motto.
This modus operandi stuck and has proven immensely profitable for Amazon. Close to its 20-year anniversary in 2005, Amazon launched its Amazon Prime membership model. With fast shipping guaranteed, members signed up in droves and enjoyed a smorgasbord of benefits, including the ability to share their membership with family members to cut the cost.
Today, Amazon Prime members number roughly 75 million globally and considering that each member pays a flat annual fee of US$99/year, this alone is a revenue stream of over US$7 billion a year. Contracts with freight companies like UPS keep shipping costs low so as not to chip away at this revenue. In fact, with only one membership price increase in over a decade, Amazon Prime members are fiercely loyal – and often comparison shop while they physically shop at “big box” stores before making purchasing decisions.
Amazon is well aware of this and takes full advantage. Does Amazon want to be the one-and-only shopping destination for consumers? In a perfect world, this could be the case. Recently, the company began test-marketing AmazonFresh, a grocery delivery service. They even “stretched their legs” into the meal kit market, competing with the likes of Blue Apron and HelloFresh. In Q3 2017, Amazon jumped into the grocery channel when it announced a merger with Whole Foods. With this came a promise to lower the cost of high-quality organic food and make it more readily available to the average American household–directly competing with stores like Trader Joe’s.
Standard brick-and-mortar grocery stores like Kroger and subsidiary Harris Teeter have been competing with stores like Trader Joe’s for years. Trader Joe’s only sells house brands, so store chains offered digital coupons to remain competitive, including for their house brands. Not to be outdone, in 2016 Kroger brands rolled out digital shopping services to meet the needs of their customers’ busy lifestyles. They now provide online ordering with pick-up and delivery options and incentives for customers who are willing to pick up during less-busy times like the middle of the day on non-holiday weekdays.
Not to be outdone, Amazon launched Amazon Go, testing a single store in Seattle where customers come to shop for prepared foods, meal kits, and other limited food and beverage items. The entire experience invokes innovative technologies, where much of the shopping process is automated and revolutionary. Customers download an app linked to their Amazon account on their smartphone and shop at their leisure. Using ceiling cameras and shelf sensors, selected items are detected and added to or removed from a virtual shopping cart. Then the automated checkout and payment process charges the customer’s account when they leave the store.
Unfortunately, the store’s opening was delayed for an entire year due to malfunctioning sensors that improperly detected purchases and even misidentified shoppers with similar body types. For an organization like Amazon where innovation is a mundane daily process, this was unexpected.
Amazon has mastered inventory management and streamlined the supply chain to the point where they are on par with Walmart – even ahead of Walmart in many regards. Walmart, however, beat Amazon to market with the “smartphone app” technology. Yes, Walmart’s “Scan & Go” product beat Amazon, the multibillion-dollar global organization behind the Kindle, Echo, Alexa, and on-demand cloud computing. Announcing “Scan & Go” in 2017, Walmart launched a test in 50 stores in select markets, where customers would – again, use a smartphone – download a proprietary app, store their payment information, scan items as they shopped, bag them, and are charged as they exited the store.
Kroger responded to Walmart with an announcement of its new initiative, “Scan, Bag, Go,” which takes its ClickList a step further. But as technological innovation isn’t a grocer’s forte, for now, customers must still visit self-checkout registers to finalize their shopping.
This exciting concept, along with the expansion of stores like ALDI and LIDL into more U.S. markets, and the price wars begin! With the goal of delivering fresh, healthy, and more economical food options, more adoption of this advanced technology isn’t far behind.
Amazon’s announcement for Q1 2017 made Walmart leap into action. Walmart went live with their program in Q3 2017 in 12 stores in the United States, with a store in Texas being the first. Walmart’s value proposition is that their customers aren’t limited to grocery items with “Scan & Go,” intensifying the competition.
Are you ready for the juiciest detail yet? Walmart launched this program in 2014, three full years before Amazon’s target launch date. The public version of the reason why the program was pulled from stores was that shoppers didn’t take to the app, but it was more likely that the app needed to be more user-friendly. We’re curious why it took three years for the “fix,” but the logical speculation is that it wasn’t deemed a priority for the organization that was seemingly ahead of its time.
With Amazon, the chief innovator of the tech industry going gangbusters with its version, Walmart could simply tweak their app and hop on board for some free publicity. This was made even better by beating the tech giant to market.
With Amazon Go incorporating Prime customers’ accounts into the experience, the simplification of the process wins. Amazon is known to take on retailers like Walmart head-to-head in price competition, with its “bots” crawling the web every nanosecond to compare prices just like “real people.” it’s no wonder they want their newest concept to be an ironclad success.
We expect nothing less from the e-commerce giant that holds a Federal Maritime Commission license as a non-vessel-owning common carrier to manage its international shipments coming into the U.S–and is building a logistics and air freight fleet, potentially rendering its agreement with UPS obsolete.
Given that Amazon is also now producing original programming and distributes through Amazon Video and that its Fire tablets are meant to compete directly with the Apple iPad, but at a much lower price point, it seems that breaking through barriers and challenging competitors is what Amazon does – and does quite well.
What will Amazon think of next?

by Felicien | Jan 29, 2018 | Education
There’s some good news for the 1.4 million people of Ontario: The Fair Workplaces, Better Jobs Act, 2017 (Bill 148) was passed into law on November 22, 2017, and took effect on January 1, 2018. The bill includes better wages and working conditions for workers in Ontario. Lawmakers say that this is the most significant change to workplace standards in several decades.
General provisions of the new bill
The Fair Workplaces, Better Jobs Act:
Raised Ontario’s minimum wage to $14 per hour on January 1, 2018.
Raises it to $15 on January 1, 2019, followed by annual increases at the rate of inflation.
Gives workers two government-paid sick days per year.
Increases the holiday entitlement.
Provides greater protection to temporary employees.
Requires employers to pay part-time, temporary and seasonal employees the same wages as regular employees.
Exceptions to this rule include situations where wage differences can be attributed to factors such as a merit system or a seniority system. Employees can ask for a review of their pay rate if they believe that discrimination has occurred.
Two studies may have impacted legislative decisions
The Bill is a result of years of hard work from workers’ advocacy groups. For some time, these groups have lobbied on behalf of workers, pushing for better government-sponsored leave time and better pay.
The landmark Fair Workplaces, Better Jobs Act, amends several essential pieces of employment legislation, including:
The Labour Relations Act, 1995 (LRA)
The Employment Standards Act, 2000 (ESA)
The Occupational Health and Safety Act (OHSA)
Many believe the bill’s successful passage was primarily due to two recent studies performed by McMaster University and United Way. For two years these institutes studied the conditions and pay of Ontario’s thousands of workers. The studies revealed that many workers consider their jobs at risk and feel that their livelihood could be cut off without warning by corporate leaders looking to cut costs.
Employees need better job security
Because of today’s competitive marketplace, companies sometimes move portions of their organization to foreign countries where cheap labor is abundantly available. Though moves like this can cut a business’s monthly expenditures, they can be unsettling to workers. Worker advocacy groups see this as a big win for Ontario’s workforce. They will now have better job security, along with stronger benefits.
The Canadian labour market has experienced solid growth in recent years, performing well in 2017. The annual unemployment rate fell to its lowest since 2008 to 6.4 percent. An incredible 93 percent of the job gains were for full-time positions. Officials expect these numbers to improve more over the next few years.
The following are some of the most important amendments to the law:
Vacation time is increased to three weeks per year once an employee has been with the same company for at least five years.
Employees will now have ten days of Personal Emergency Leave each year, and the first two will be paid work days. In the past, Personal Emergency Leave was only available to those who worked at a business with over 50 employees. In addition, employees were required to present a doctor’s note explaining their sickness. These two latter stipulations are now removed.
The Pregnancy Leave Entitlement was extended from 35 weeks to 61 weeks. Additional amendments are pending that would allow employees to spread their pregnancy leave over a period of time.
Several important family and personal leave of absences have been added, including leave for domestic violence, child death or disappearance, family medical issues, and critical illness.
How independent contractors are affected
Other amendments include changes to overtime and public holiday pay rules. These new changes better outline how and when employees get paid. Changes also prohibit an employer from misclassifying employees as “independent contractors.” As an independent contractor, workers cannot receive job protection benefits from the ESA. The changes even affect workers from temp agencies. They are now eligible for additional pay if an assignment is cut short. This change will provide partial compensation to temporary workers who were expecting an assignment to last a certain length of time but was inadvertently cut short.
Canceled Shifts
The Canceled Shifts (3-Hour Rule) requires employers to pay workers for 3 hours of work if the person shows up for work and the shift is canceled. This applies even when the shift is canceled the day before. Under the new labour law, employers must give their employees at least 48 hours’ notice of a shift cancellation. The three hours of pay must be calculated at the regular hourly rate, and if premiums were expected (as with holidays) these must also be paid.
Right to Refuse Work
The Right to Refuse Work makes it possible for employees to refuse a shift where they are being called on to work someone’s shift. The employer is not allowed to discipline any employee who refuses to work. 96 hours (4 days) of notice is required.
Minimum On-Call Pay
Employees “on-call” who are not eventually called into work, must be paid for three hours of work at their regular rate. These rates are figured by each 24-hour period that an employee is on-call.
Schedule Changes/Work Location
After three months of employment, employees are eligible to request changes to their work location or schedule. Though employers are responsible for discussing the matter with the employee, they are not forced to grant it. However, the employee can ask about the reasons for denial without any fear of reprimand.
New Record-Keeping Requirements
This will force employers to maintain separate records regarding the changes listed above. For instance, where employees are scheduled to work a shift that is canceled when the worker gets there. New record-keeping requirements also include events where employees were on call for 24 hours and therefore qualify for the three hours of pay for that day. The ESA may feel the need to document incidents like this in case of lawsuits. Many employers already document changes to work schedules or work locations.
Miscellaneous items
A number of other miscellaneous items were included in the Bill that would require Union Certification for those in construction, those in the home care industry, temporary help agencies and community service industries. A few of these miscellaneous items pertain to actions of employees, employers and the union.
As the new changes, requirements, and stipulations unfold, the Fair Workplaces, Better Jobs Act, 2017 may require some interpretation. Employers are already studying the bill to learn exactly how it will affect their employees. They want to fully comprehend how to properly implement the Bill’s provisions. Employees are encouraged to become familiar with the changes as well.

by Felicien | Jan 28, 2018 | Education
January 28th, 2018 is Data Privacy Day, an international effort led by the National Cyber Security Alliance (NCSA) annually for the purpose of raising awareness about the importance of safeguarding data. Data Privacy Day commemorates the signing of Convention 108, which took place on January 28th, 1981 as the first legally binding international treaty regarding data protection.
Your data is your most important business asset, and when it’s lost or stolen, your company faces serious direct financial losses – from legal fines to decreased productivity to lost sales and a damaged reputation. You simply can’t afford to leave your data vulnerable to the sophisticated cybercriminals out there patiently waiting to get their hands on it. {company} has always put data security first and foremost – helping our clients stay as secure as possible.
Data security is becoming more important than ever before as we bank, shop, and communicate online…
That’s why we’ve compiled 6 great tips to help you better protect the privacy of your data online:
Encrypt as much and as often as possible: Encryption acts as an extra layer of security; scrambling sensitive information so it’s unreadable to anyone who doesn’t have the authorization to read it. There are tons of tools available to encrypt your sensitive information at rest and in transit.
Keep your operating system up-to-date: You’ll hear this tip time and time again because it’s so important. Those operating system and software updates might be annoying, but they’re absolutely vital to ensure you have the latest security updates and vulnerability patches installed.
Run anti-virus software periodically: There’s a wide range of dangerous threats out there waiting to attack your system at any given moment. As a result, it’s crucial for you to install a reliable anti-virus software and make sure you’re performing scans on a periodic basis.
Use unique, complex passwords for accounts: Reusing passwords on accounts and/or services is a huge risk. You need to ensure you’re using a unique, complex password for every account and/or service you own. Your passwords need a mix of letters, numbers, and special characters for optimal protection.
Keep up with managing your privacy settings: While it’s daunting to look into the privacy settings of every application and account you have, it’s important to ensure you’re not providing anyone with access to sensitive information you’d rather keep private.
Avoid using free Wi-Fi networks: Almost every restaurant or shopping center offers free Wi-Fi access nowadays, but it’s not entirely safe, especially when you’re doing online banking. At an absolute minimum, never check your bank account on a free Wi-Fi network, but it’s preferable to avoid them altogether.
Need help implementing the 6 tips listed above? {company} is your trusted team of IT security experts in {city}. We put data security first and foremost on our priority list – helping our clients stay as secure as possible. Call {phone} or email us at {email}.
by Felicien | Jan 28, 2018 | Education
If you’re not doing everything in your power to protect your data, you’re leaving your most valuable business asset open to cybercriminals!
January 28th, 2018 is Data Privacy Day, an international effort led by the National Cyber Security Alliance (NCSA) annually for the purpose of raising awareness about the importance of safeguarding data. Data Privacy Day commemorates the signing of Convention 108, which took place on January 28th, 1981 as the first legally binding international treaty regarding data protection.
Are You Keeping Your Customer’s Sensitive Information Private?
As your company continues to grow, you’re creating and storing more information than ever before – and a lot of that information happens to be incredibly confidential, such as financial account numbers, home addresses, and credit card numbers. Are you keeping your customer’s sensitive information private? What about your business’s sensitive information?
{company} helps our clients protect confidential information of all types because we know it’s vital in today’s increasingly unsafe business environment. We make sure our clients are able to:
Handle departing employees appropriately: Unfortunately, departing employees pose a huge risk to your organization. That’s why it’s important to ensure proper access control measures are in place to keep track of who’s able to access that information. It’s also important to perform a complete wipe of all data on corporate-owned devices after they’ve left the company.
Keep hackers out of the network: We all know hackers are getting more and more sophisticated by the day. Installing the proper firewalls and anti-virus software is vital to keeping malicious programs away from your network. Educating your staff members is also crucial so they’re aware of the latest threats.
Properly maintain hardware and software: If your hardware and software aren’t properly up-to-date with the latest patches, it’s easy for cybercriminals to attack vulnerabilities or weak points waiting to be exploited. That’s why properly maintaining hardware and software in a proactive manner is necessary.
If you’re not confident that whoever handles your information technology is handling departing employees appropriately, keeping hackers out of your network, or properly maintaining your hardware and software, get in touch with us. We’ll perform an in-depth review to make sure you’re protecting your data properly.
In the meantime, feel free to download our handy data security tip sheet! It’s filled with simple, easy-to-follow tips that will help you AND your staff start protecting your data.
In honor of Data Privacy Day this year, why not take charge of protecting your data? Call {phone} or email us at {email} to talk about what {company} can do for you.

by Felicien | Jan 26, 2018 | Education
With every New Year comes the chance to reset priorities. Unfortunately, when the topic of implementing a data recovery plan comes up, the comment we most often hear is “I know I should, but I haven’t gotten around to it yet…”
So…what if the pilot on the next flight you’re on announces right after takeoff, “I know we should have run through our preflight checklist, but we haven’t gotten around to it yet…”???
Without a solid backup and recovery plan in place, just one mission-critical file that gets lost or stolen could put your company in a world of serious hurt. When you compare the high cost of replacement, repair, and recovery to the relatively trivial price of keeping good backups, the choice is an absolute no-brainer.
Why Disaster Recovery Planning Matters More Than You Think
Let’s face it; data is the nucleus of your business. That means that a single ransomware attack could wipe you out in a matter of minutes. Today’s cybercriminals are raking in literally billions of dollars (yes, billions) preying on the unwary, the poorly protected, and those who “haven’t gotten around to it yet”.
Let’s consider the facts… Ninety-seven percent of IT services providers surveyed by Datto, a data protection company, report that ransomware attacks on small businesses are becoming more frequent, and they expect that trend to continue. These attacks are taking place despite anti-virus and anti-malware measures in effect at the time of the attack.
Windows operating systems are most often infected, followed by MacOS. Cloud-based applications, particularly Dropbox, Office 365, and Google Apps, are also being targeted.
Ransom demands typically run between $500 and $2,000. About 10% of those, however, exceed $5,000. And even at that, paying a ransom demand is no guarantee that encrypted files will be released. For a typical SMB, downtime from ransomware can cost around $8,500 per hour and will take an average of 18.5 hours of the company’s time. That’s a hit to your bottom line somewhere in the neighborhood of $157,250. Yet in many cases, the ultimate cost has reached multiple hundreds of thousands of dollars.
In a recent survey of 6,000 IT professionals by the Ponemon Institute, 86% of companies had one or more incidents causing downtime in the past 12 months. Typical downtime was 2.2 days, with an average cost of $366,363. And that’s just the average. Could your company survive that kind of hit? It’s no wonder that 81% of smaller businesses suffering such an attack close their doors within three years.
What’s behind these costly incidents? Here’s the breakdown of contributing factors:
Human error: 60%
Unexpected updates and patches: 56%
Fire, explosion or Natural Disaster: 36%
Power outages: 29%
Note that human error accounts for 60% of the breaches. It’s no wonder then that ransomware attacks are on the rise since they can be triggered by just one employee inadvertently clicking a bad link in an e-mail or on a social media site. Human behavior is hard to control. However, the #1 antidote for a ransomware attack is having a secure backup ready and waiting to replace encrypted files.
And when you scan through the rest of the list above, it becomes clear that, while you need to implement a comprehensive set of data security measures, having a solid and reliable data recovery plan in place and ready to go the moment disaster strikes is still your best defense.
Protect Your Company From A Knockout Blow In 2018
Cyber threats are proliferating, and are expected to grow throughout 2018 and beyond. Will this be the year you finally get your data backup and recovery plan DONE?
The choice is yours—exposure to a devastating loss… or rock-solid security. Let us help. Call us at {phone} or email {email} and let’s schedule a thorough Backup And Recovery Plan Audit for your company.
Do NOT wait until disaster strikes. Let’s make 2018 the year you finally get this DONE. Contact me TODAY so we can keep your company’s story from becoming yet another unfortunate statistic.





