Blog / Reports / Resources
Create Your Own Fonts In Windows 10
Create Your Own Fonts In Windows 10 You may have been using Windows 10 for some time now, but it’s likely that you haven’t mastered all of its features just yet. Did you know that you can create your own fonts? In the Windows store, you can get the “Make Your...
Why Today’s CEOs are Worried About Cybersecurity
The top concern for CEOs today isn’t competitors or a recession — it’s cybersecurity. See why this is becoming the biggest challenge for an organization’s top executive. Why Today’s CEOs are Worried About Cybersecurity A business’s...
What Is Network Segmentation?
What Is Network Segmentation? Businesses that offer WiFi to their customers or have sensitive data needs should consider network segmentation as a necessary component of their IT solution. With network segmentation, your wireless services are separated into different...
Online Excel Training: Tips & Techniques For Managing Workbooks
Organization Shouldn’t Be Complicated Out of all of Microsoft’s Office programs, Excel is one of the most universally used. What started out as a fairly basic spreadsheet program has evolved into a must-have business tool. However, the more you use Excel, the more...
myGov Outage Upsets Tax Return System Causing Mayhem
myGov Outage Upsets Tax Return System Causing Mayhem If you’ve experienced difficulties with the Australian Government’s myGov website, you aren’t alone. The myGov portal — the online system that Australians use to access their employer payment...
Keeping An Eye On The Dark Web?
Keeping An Eye On The Dark Web? Do you know about the “Dark Web”? It’s the part of the Internet where your private data – passwords, social security, credit card numbers, etc. – could be for sale right now. Do you know how to check if they are? The...
Online Free Excel Training: Tips & Techniques For Managing Workbooks
Organization Shouldn’t Be Complicated Out of all of Microsoft’s Office programs, Excel is one of the most universally used. What started out as a fairly basic spreadsheet program has evolved into a must-have business tool. However, the more you use Excel, the more...
Cloud Storage vs. On-Site Data Housing
Cloud Storage vs. On-Site Data Housing: Factors for Healthcare Organizations to Consider Internet technology has opened the way for data storage to be far less cumbersome for modern healthcare organizations. After all, handling all the incoming data in a modern...
How to Respond to a Phishing Attack
Phishing is one of the most commonly-used cyberattacks in Australia. Statistics from the Office of the Australian Information Commissioner show that phishing accounts for 39 percent of all breaches reported. Therefore, it’s important to be aware of how to...
How to Know When to Outsource IT
Nearly every company must now rely on technology on a daily basis. For most companies, the role of technology will only grow in the future, making it even more important for all companies to have the tech support they need at all times. Depending on the situation,...
How to Achieve Digital Success
As the business world continues to evolve, digital transformation becomes even more important for every company, regardless of the industry. However, successfully moving into the digital arena and remaining on top requires companies to make the right choices when it...
Efficiently Manage Notifications In iOS 12
Apple’s mobile iOS operation system is one of the most popular platforms in the world. With more than 1.3 billion devices running iOS worldwide, Apple has clearly done an excellent job of providing a world-class experience for its users. Watch the video below or...
Microsoft Defender ATP Security for Macs
Microsoft Defender ATP Security for Macs Microsoft Defender ATP (Advanced Threat Protection) is a program that detects ongoing attacks on corporate networks, blocks any that are malicious, and then provides response recommendations to improve security. Microsoft has...
Intel Humiliated by Losing CPU Market Share to Eager AMD
Intel Humiliated by Losing CPU Market Share to Eager AMD Intel’s continued problems with delivering CPUs are expected to go on throughout the fall and potentially 2020. Intel’s CEO Bob Swan told shareholders during their second-quarter conference call that...
What Are the Most Serious Cybersecurity Stories of 2019?
We’re only halfway into 2019, yet data protection specialists and IT analysts have already seen an unfortunate spike in criminal activity across industries. Thus far, here are the biggest cybersecurity crises of the year. 2019’s Top Cybersecurity Stories #1 – Supply...
Top Ways to Avoid Phishing Scams (Including Spear Phishing)
Top Ways to Avoid Phishing Scams (Including Spear Phishing) Phishing scams — and, increasingly, spear-phishing scams — are the number one way that cyber hackers gain access to closed computer systems, steal information and money, and corrupt data. Let’s take a look at...
How Do I Choose a Cloud Computing Model?
How Do I Choose a Cloud Computing Model? No matter what your company or organization specializes in, it’s sure that you have some form or forms of data that needs to be stored, well, somewhere. Before the invention of cloud computing, most company data was always...
The Top Cyber Security Threats Facing Enterprises and How to Mitigate Them
The Top Cyber Security Threats Facing Enterprises and How to Mitigate Them As cybersecurity threats become more prominent and the Internet of Things (IoT) devices become more essential, the tactics behind the threats are evolving into more sophisticated forms. This...
3 Ways to Improve Your Cyber Security Plan
3 Ways to Improve Your Cyber Security Plan Cyber attacks cost organizations millions of dollars per incident and often results in system downtime. The average cost of system downtime per cyber attack is as much as $1.25 million, according to Cybersecurity Ventures....
Small Business Owner? How to Choose Tech Support
Small Business Owner? How to Choose Tech Support It is an unfortunate truth that many small businesses assume they don’t need to outsource their IT needs to a professional IT company. This couldn’t be further from the truth. In fact, small businesses...
What Are the Top Tips for Choosing the Best IT Company?
What Are the Top Tips for Choosing the Best IT Company? Website outages, cybersecurity attacks, and any number of other IT incidents can cost your company hundreds or even thousands of dollars — every minute. For this reason alone, you need an outsourced IT company...
How Technology Helps Today’s CFO Improve Operations
How Technology Helps Today’s CFO Improve Operations The business world is increasingly tech-savvy, and organizations are looking for CFOs who are comfortable with the language and strategies of digital technology. The office of the CFO has long been a center of...
Securing the IoT Network in Your Healthcare Facility
From wirelessly connected fax machines to network-integrated treatment equipment, the modern-day healthcare facility has a full list of things that must be a part of their network. As convenient as the IoT may be for modern practices, every device adds a potential...
How Can You Encrypt Files and Folders in Windows 10, 8 or 7?
How Can You Encrypt Files and Folders in Windows 10, 8 or 7? You can encrypt files and folders in Windows (vers. 7-10) using BitLocker. This Vista operating system extension has on-disk encryption as well as key management capability. It’s protected by...
Microsoft Office 365 and Your Business: Boost Productivity with the Right Tech Tools
Microsoft Office 365 and Your Business: Boost Productivity with the Right Tech Tools The workplace is becoming more and more digital every day. New tech tools are developed regularly, and most have the same goal—to make your life easier. While some new developments...
How To Send Large Attachments Over Email
How To Send Large Attachments Over Email When you’re trying to send large files to colleagues, customers or partners, you often can run up against issues that make transmission difficult. Many commercial email programs put size limits on files transmitted over...
Your MacOS Is Under Attack: 2019’s Biggest Malware Threats
Your MacOS Is Under Attack: 2019’s Biggest Malware Threats The Mac operating system (MacOs) has frequently been hailed as one of the best systems for its resiliency to malware and typical viruses. But the days of MacOs standing strong and tall with no worries...
How to Stop Your CEO from Becoming a Phishing Target
How to Stop Your CEO from Becoming a Phishing Target Business fraud affects businesses of all types and sizes, and there are no individuals within your business that are truly immune from the possibility of a targeted attack. However, there are some people who are...
How Are Face and Touch Recognition Changing iCloud Access?
How Are Face and Touch Recognition Changing iCloud Access? Apple may be testing new security procedures for iCloud.com with its next OS release. 9to5mac has reported that the beta for iPadOS 13, iOS 13, and macOS Catalina can use Touch ID and Face ID to secure and...
How Can You Insert a Text Box in Google Docs?
How Can You Insert a Text Box in Google Docs? There are two simple ways to add a text box into your Google Doc. Each lets you set apart text that stands out. Both methods allow you to copy-paste or move the text box between documents. The methods include inserting a...
Data Security is Vital to Reducing Business Risk
Data Security is Vital to Reducing Business Risk Traditional business risk has fallen into a few different buckets with the economy and competitors being two of the major forces under consideration. The tides change, and businesses today must add some additional items...
Slow Broadband Speeds Caused by NBN’s Copper Connections
Broadband internet service isn’t providing the speeds advertised. Modems provided by Australian internet retailers aren’t capable of delivering 100 Mbps download speeds over the average fibre-to-the-node connection, according to the consumer...
Habits You Want From Your Technology Partner
Habits You Want From Your Technology Partner When you are running a business, you want your technology to integrate well with the other tech you use in your business and with your overall IT platform. When you run into situations where your tech fails to integrate...
Microsoft’s Hyper-V Server 2019 Finally Released: Here’s What You Need to Know
Microsoft’s Hyper-V Server 2019 Finally Released After being plagued with everything from data loss issues to a lack of available hardware, Microsoft finally released their long-awaited Hyper-V Server 2019 to their Evaluation Center approximately eight months...
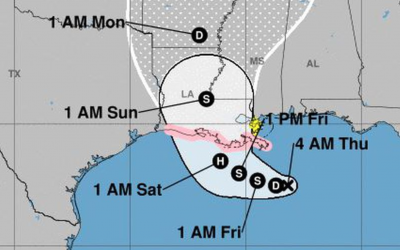
Louisiana Is On Hurricane Watch – How Should You Prepare?
Tropical Storm Barry is expected to hit Louisiana and Texas in just a few days – what steps can you take right now to make sure you’re prepared? As of yesterday, parts of coastal Louisiana have been put on hurricane watch in anticipation of what could be the first...
Building a Rock Solid Cybersecurity Plan
Cybercriminals may be going into a stealth mode, but that doesn’t mean that cyberattacks are slowing down — quite the opposite, in fact. According to the 2018 SiteLock Website Security Report, attacks increased by 59% and accelerated going into December....
How Does Windows 10 Improve Security and Data Protection?
Windows 10 comes a step closer to preventing cyberattacks and privacy threats facing users. It’s a next-generation solution that helps you fight threats from hackers and criminals who target your business. This is a big plus for cybersecurity managers. The past...
Australian SMBs Severely Affected by Ransomware Forcing 1 in 5 to Close
Ransomware attacks have caused business interruption and other lingering damage to Australian small- and medium-sized business, enough damage that 22 percent have been forced to close after an attack. Ransomware attacks have paralysed business operations so much so...
Why Is Wi-Fi So Slow on My Phone?
Just about nothing is more frustrating when using a smartphone than connecting to a sluggish or broken Wi-Fi network. In most places, mobile data is so effective and speedy these days that we just can’t accept a Wi-Fi network performing worse than our mobile networks...
Old School Meetings Revisited
You know running a successful business requires much more than just offering a great product or service. It takes constant engagement and collaboration of all of your employees to produce the best results, and it takes your best effort to remain competitive in a...