Blog / Reports / Resources
Steer Clear of These Negative SEO Practices
Negative SEO is real, and it can have a serious impact on the overall search ranking of your business. Learn what this means and how you can prevent damaging attacks. Search Engine Optimization (SEO) is still the stuff of legend for many business leaders and...
What You Can Learn from HITRUST/AMA Partnership on Cyber Risk Management
Wondering what the HITRUST/AMA workshop partnership means for your business? Here’s a brief primer on the new workshops being rolled out, and what you can do to increase cybersecurity. Cyber risk is everywhere. While we all know it’s real, it’s hard to...
When Law Firms Should Switch to Managed Services
Technology is ever-changing, and law firms need it to run a business. But, a lot of things can go wrong, such as security breaches and forgotten passwords. Some law firms have a small IT staff, but there may be signs that it’s time to hire outside managed services....
Happy Birthday Microsoft Word
Since the 90’s, Microsoft Word has become the standard that every student learns in order to create basic documents, fliers, invitations and more. There is nothing more standard and boring on a computer than Microsoft Word, but whatever would we do without it? If...
Phishing Alert: Beware of Recent String of ‘Social Engineering’ Phone Calls
Thanks to an alert client of ours, a malicious phone caller was stopped in their tracks. If you stay alert for suspicious calls and email, you can also avoid becoming victimized by hackers or scammers. We have started to see an increase in these sort of telephone...
Massive Data Breach At Equifax
Equifax has suffered a major breach of sensitive data since March 2017. Millions of Americans have been affected. The first intrusion was discovered in March, and this agency’s central clearinghouse for sensitive data like driver’s license numbers and social security...
The Benefits of Managed Services for Law Firms
In response to the ever-increasing cyber threats on law firms, “companies are demanding a level of security. Pressure from clients is causing firms to invest and focus on cyber risk. According to the 2016 ABA Legal Technology Survey Report, 30.7 percent of all law...
Is Your Small Business Scrambling to Shore Up Data Security?
Small to mid-size businesses around the country are considering how to maintain data security in the aftermath of one of the largest data breaches in history at Equifax. How can you ensure that your business has critical patches covered while still staying focused on...
Hackers Target Sonic
The Sonic Drive-in is an old-fashioned and popular fast-food chain with roller-skating carhops and has almost 3,600 locations in the US. Just recently, it became a popular hit for hackers. The breach affected an unknown amount of its store payment systems....
Business Continuity And Natural Disasters: How to Be Prepared
Proper planning allows companies to protect data, systems, and people while keeping the business operational during a disaster. The recent devastating hurricanes to hit the mainland United States and Caribbean countries and territories destroyed entire communities....
Law Firms Need to Protect Themselves Against Security Breaches
Cybersecurity is evolving. This is more than just a technology issue or an added clause in the retainer agreement—it’s the biggest risk that law firms face in 2017. Cravath, Swaine & Moore and Weil Gotshal & Manges, two of the largest firms in the United...
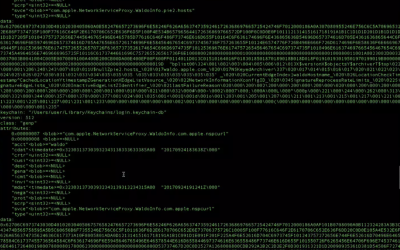
Keychain Makes Mac Users Vulnerable: Protect Your Personal Information
A recently discovered vulnerability within Mac’s Keychain has left Mac users at risk. Find out how you can take steps to protect your personal information and yourself from becoming exposed. Technology is supposed to make our lives easier, and Apple engineers...
NIST Compliance: How to Address Challenging Components
New guidelines governing the transmission, storage and use of protected data create compliance challenges for companies and contractors looking to do business with federal and state agencies. Companies wanting to continue to do business with certain federal...
6 Lessons Small Business Leaders Should Learn From the Equifax Data Breach
The Six Lessons Your Small Business Should Learn After the Equifax Data Breach The most stunning business news in the last month has to come from articles about the Equifax data breach. The company estimated that this cybercrime impacted at least 143 million...
How to Streamline Operations with Software and IT Managed Services
Discover how to streamline business operations with software and IT managed services. Today, businesses can easily streamline operations with software and IT managed services. IT services offer a full range of high-tech solutions that are full-hosted and delivered...
The Benefits of Using IT Managed Services
Discover the many benefits of partnering up with an IT Managed Service Provider. Today, many businesses are partnering up with IT managed service providers. Sixty percent of businesses use IT managed services, and that figure is expected to continue to grow. And...
How Non-Profits Manage to Make Profits With Managed Services
Non-Profit Managed IT Services & Support The primary function of a non-profit should be to fulfill its goal, not worry about IT. Learn how non-profits can use managed services to maximize operational efficiency while minimizing IT expenditures. It seems like a...
Happy Cyber Security Month Everyone!
October is Cyber Security Safety Month—How To Keep Your Business Secure Online. Threats Continue to Increase. Unless You Take Specific Steps, Your Business Is in Jeopardy. Staying safe and secure online is becoming more difficult all the time. Cyber criminals seem to...
Why Do I Need Managed IT Services?
Learn why your company should be using managed IT services. By 2019, the managed-services market is projected to grow by $193 billion. Both small, medium and large businesses are becoming very aware of the reasons to choose the managed-services business model, and the...
Rash Of Phishing Scams Targeting Online Accounting Users Has Cybersecurity Experts’ Attention
A series of online accounting-specific scams popped up in recent months, prompting cybersecurity experts to take notice. Late August saw a series of very similar phishing scams make a brief appearance in the inboxes of online accounting software consumers. By spoofing...
Stop Hunting and Pecking for Apps With the Office 365 App Launcher
How to Use the Office 365 App Launcher to Work Smarter and More Productively Few people will argue that Office 365 offers many features that can help them work more productively. For instance, the cloud-based software and storage will let you work from just about...
Apple and Windows Skip Version 9 — What’s the Story?
The iPhone X was announced a few short weeks ago, but why do major manufacturers skip release numbers? Turns out, there’s a great reason. Apple recently held their annual release party while the world watched and waited to see what new wonders were in store....
How IT Managed Services Solve Nonprofit Budgeting Woes
Maintaining your nonprofit’s strategic mission focus is critical and often requires next-generation technology to an executive on objectives. IT managed services providers offer exceptional support and value, with a cost structure that is sustainable for...
A Bug in the Apple?
High Sierra’s Password Theft Vulnerability Learn how a macOS update named High Sierra can leave your passwords vulnerable to theft. As this tech giant usually does before a new release, Apple generated massive excitement over High Sierra. This free upgrade for...
Just Go with the Flow.
Is your business’ productivity suffering? It may be due to a poor workflow. Using Microsoft Flow can help. Is the productivity of your business slipping? Do projects take longer to complete than they should? Perhaps this has nothing to do with inadequate staff...
Are You Still Risking Your Data with Local Storage?
If you aren’t storing your business data in the cloud, you’re risking physical damage that may not be recoverable. Learn how to quickly overcome these vulnerabilities in the Cloud. There was a time when backing up business data included checking the date stamp on a...
Do You Use WordPress? Watch the “Backdoor!”
WordPress may be one of the world’s most popular content management platforms, but its plugins open up a Backdoor Vulnerability. WordPress is one of the most popular CMS (Customer Management Software) platforms of all time, and for good reason. The overall ease...
Privacy Levels to Pricing: What You Need to Know About Buying a VPN
Virtual Private Networks, or VPNs, provide you with an added layer of security for your business systems and sensitive data. Learn how to find the right VPN solution for your unique needs. If you’re considering adding a VPN, or Virtual Private Network, service...
Ransomware Threats—the Good and the Bad News
Although ransomware threats are real and dangerous, there is actually some good news to be had. By knowing what the good and the bad news is, in fact, people will place themselves in the best possible position to deal with these threats. Of course, these so-called...
Read This Before You Turn On Bluetooth!
As cybercrime tactics continue to adapt and overcome conventional IT security, it’s more important than ever to have powerful cybersecurity support in {city}. Cybercrime is a common part of business these days. Even if you haven’t encountered a...
LinkedIn InMail Hit with Malicious Phishing Attacks
LinkedIn has a few new problems with the recent hack of their paid InMail service. Users beware: links within the popular networking site may be malicious. Learn more and protect yourself from this recent threat. LinkedIn is known as one of the most popular social...
The Equifax effect: IT pros and business data security
Good advice from IT pros can reduce chances of a data breach With the latest cyber hack of Equifax in the news, consumers and businesses alike are scrambling to check on their data’s security, and taking steps, such as freezing accounts, to mitigate any possible...
Sales 101: 5 Presentation Mistakes That Are Costing You Sales
What’s wrong with your Sales presentation? If you’re a salesperson, you work hard to make calls, research the company, attend events and send millions of emails just to get in the same room with a potential buyer. It’s painful when they don’t respond positively...
Tainted CCleaner App Scare Requires Immediate Software Update
Is your business affected by the most recent malware attack on a popular Windows software? Get the details on how to protect yourself. It may be an IT professional’s worst nightmare: an app or piece of software that is meant to clean malware off of your...
Kaspersky Software— Not in the US?
Cybersecurity software from Kaspersky Lab is no longer on the shelves of Best Buy after fears emerge of a connection between the company and the Russian government. There are many reasons a store stops stocking a particular product. However, it’s rare when a business...
Apple’s iPhone X— Is It Worth the High Price?
The annual launch of the new iPhone lineup is here, and the inclusion of iPhone X may seem a bit confusing. Learn why Apple may have chosen to use this unique name for its newest iPhone. It’s no longer a secret. Since a leak just days before the official release,...
Are You Using the Latest Features in Microsoft Teams?
Microsoft Teams introduces more features for educators, Skype users, freelancers, and more! Make sure you’re taking advantage of them for your business. Microsoft Teams is a social space/messaging service for companies using Office 365. It’s great for growing...
Don’t Make These HIPAA-Compliance Mistakes!
Data compliance is growing more complicated. Here are some pitfalls to watch out for. It’s time to get smart about HIPAA compliance today. It’s not just complicated – it’s now more complicated because the healthcare industry has become increasingly...
Don’t Make a Bad Situation Even Worse. Beware of Equifax Scams.
The Equifax breach was bad enough. Read about the most common Equifax-related scams to keep from being a victimized twice. Over 143 million US residents have a reason to worry about the fallout of this year’s Equifax hack. As we all try to sort out how this...
Do You Have a Cloud Plan for Your Business?
Cloud computing is popular, but make sure you’re ready to make the switch. Business owners are considering whether to transition from running software locally, to join the millions of companies already using cloud-based applications. According to RightScale’s 2017...