Blog / Reports / Resources
Reset Your Computer System Today Using Windows 10
Do you need to reset your computer system? Resetting is different from simply refreshing or restoring a computer system. Resetting means reinstalling Windows but during the process, you delete your personal settings, apps (unless the apps originated with the...
Reasons for Choosing Microsoft Teams as an Alternative to Zoom
Microsoft Teams as an Alternative to Zoom COVID- 19 induced lockdowns and social distancing measures helped spur Zoom’s growth. The video conferencing app managed to attract 300 million users by April 2020 compared to 10 million in December. Its rise to...
Convert a User Mailbox to a Shared Mailbox in Microsoft 365
How to Convert a User Mailbox to a Shared Mailbox in Microsoft 365 After converting your regular mailbox to a shared mailbox in Microsoft 365, you retain all your existing calendars and email. The only difference is that it will be visible to several people. You can...
What Does $150K Ransomware Payment Say About Your Cybersecurity?
$150K Ransomware Payment A recent news piece published by Tech Republic highlights the discouraging reasons why too many businesses fall prey to hackers and pay ransoms for their digital property. Perhaps nothing adds insult to injury quite like someone burglarizing...
What’s the Best Way to Switch IT Managed Service Providers?
The Best Way to Switch IT Managed Service Providers The COVID-19 lockdowns have naturally changed how many organizations and companies operate. Educational institutions are embracing virtual classes, events that were previously held in person are now fully virtual,...
Microsoft Edge Browser FAQ
Have You Tried The Microsoft Edge Browser? Microsoft’s Internet Explorer has been around from the early beginnings of the World-Wide Web. Over the years, it was sometimes immersed in controversy since it was “built into” some previous Windows versions....
Internal IT vs. Outsourcing IT
Internal IT vs. Outsourcing IT: The Value of Outsourcing to an MSP The question of whether to outsource or rely on an internal IT team is common. Services that were once considered ‘nice to have’ are now necessities. They include machine learning, artificial...
Alleviate Customers’ Booking Frustrations with Microsoft Bookings
Microsoft Bookings: Part Of Your Microsoft 365 Subscription For service-based businesses, a significant paint point in the customer experience is the simple process of scheduling an appointment. A traditional appointment-booking system requires the customer to call...
Microsoft Office Lens Lets You Scan Virtually Anything
How Microsoft Office Lens Lets You Scan Virtually Anything As businesses move online, more of their documents become virtual. Even with the mass migration to the digital world, however, there’s still plenty of work done on paper and other real-world canvases....
Did You Really “Reply All” On That Last Email?
Office Workers Rejoice: Microsoft is Finally Subduing the Dreaded’ Reply All’ Do never-ending reply-all threads emails put a damper on your business chewing up precious time and resources? The good news is, Microsoft rolled out Reply-All-Storm Protection...
Are You Ready For Pandemic 2.0?
Will We Have Another Wave Of COVID-19? Dr. Anthony Fauci has made clear that he is almost certain the novel coronavirus will come back in the fall. Even so, a whopping 42% of CFOs don’t have a plan for what to do if the pandemic and accompanying shutdowns hit...
Microsoft Outlook: FindTime With Colleagues
Everything You Need to Know About Operating and Using FindTime Scheduling meetings seems like it should be an easy task. However, anyone who does business knows with everyone’s busy schedules how difficult it can be to find a time that works for everyone who...
How to Use Microsoft Teams
How to Use Microsoft Teams Technology Microsoft Teams has quickly become one of the most popular tools businesses are using as employees have migrated to working from home. How can your business best use Teams and its features to keep employees connected and...
Microsoft Teams Options Improve Remote Presentations
Microsoft Teams Options Improve Remote Presentations Until the recent rollout of Microsoft Teams background customization feature, videoconferencing was a sometimes less-then-enviable communication vehicle. Users would have to tidy up the workspace, scrunch the camera...
Cybercrime & Coronavirus: What You Need to Do to Protect Business, Employees, and Profits
Cybercrime Spikes During Coronavirus: Tips to Protect Your Business Learn why cybercrime tends to spike during times of global crisis. Get tips on how to protect your tech environment from cyber criminals during the coronavirus. Right now, people are hanging onto...
What You Need to Do to Protect Your Team From Coronavirus Phishing
How to Protect Your Business From the Surge in Phishing Websites Look at the spike in phishing websites during the coronavirus. Learn how cybercriminals are leveraging the pandemic. Find out how to protect your business. As the entire world is worrying about the...
COVID-19: Safety How to Clean Your Phone Effectively
How to Protect Your Phone From the Coronavirus Find out how long the coronavirus can live on your phone. Learn how the coronavirus gets onto phones. Get tips on how to clean your phone or other devices. Around the world, people are taking unprecedented measures to...
What Is Two-Factor Authentication (2FA) and Why Does it Matter?
What Is Two-Factor Authentication (2FA) and Why Does it Matter? What is two-factor authentication (2FA) and why does it matter? If you are unfamiliar with this extra layer of protection for all of your logins, keep reading. It’s no secret that we live in a time where...
Hackers Target Zoom Meetings for Cyberattacks
Zoom Scrambles to Address Cybersecurity Issues in Meeting Platform As the usage of Zoom has skyrocketed during the coronavirus outbreak, the company has had to respond quickly to security flaws and potential phishing attacks As Zoom usage skyrockets around the...
Coronavirus Forcing Your Workers to Stay Home? Quickly Shift to an At-Home Team in the Midst of Crisis
How to Create a Work-From-Home Team Quickly As Your Business Deals With the Coronavirus Stay productive and secure your tech network as you deal with the coronavirus. Get support for at-home employees. Learn how to switch from an in-office to a remote team. In the...
What You Need to Know About Two Factor Authentication
Everything You Should Know About Two Factor Authentication Does your business use 2FA? With the prevalence of data breaches today, it’s time to start employing this simple security feature within your business. Without a doubt, you’ve read and heard about the...
Smart Steps When Working From Home
Working From Home Due to Coronavirus? Consider These Tips If you’re suddenly working from home due to the coronavirus, maximize productivity with a dedicated workspace, enjoyable breaks, and engagement with colleagues. For the vast numbers of Americans suddenly...
Remote Workforces Deliver Business & Employee Benefits
When considering the employee and employer benefits of working remotely, businesses are wise to change. The alternative could make your outfit less competitive. If you would like to gain a little perspective on how radically our culture has changed, try this...
Coronavirus Spreads Computer Viruses as Hackers Target Businesses
Hackers Target Businesses Concerned Over COVID-19 Hackers are capitalizing on fear and concern related to coronavirus to launch ransomware and malware attacks. Here’s how to protect your business and employees. As the COVID-19 spreads worldwide, hackers are...
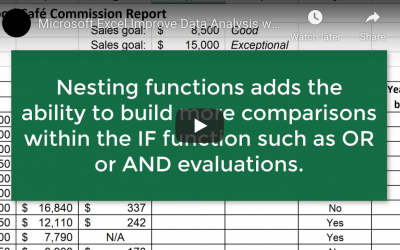
Top Tips for Improving Data Analysis with the IF Function in Microsoft Excel
Improving Data Analysis with the IF Function in Microsoft Excel Have you ever wondered what the IF Function in Microsoft Excel actually does? Here we explore a few top tips for making it save you time while evaluating data. There’s no doubt that Microsoft...
What Is Two Factor Authentication?
Protect Yourself – Use Two-Factor Authentication for Your Business Learn about what two-factor authentication is and how it works. Once you understand its benefits you will see how helpful it could be for your business. Two-factor authentication is...
Does Your Cybersecurity Plan Include Incident Response Measures?
Has Your Business Fallen Behind In Its Incident Response Strategy? Incident Response plans are proving to be a key element in data breach recovery. That’s why proactive industry leaders are adding and updating these strategies. Entrepreneurs and other...
[Video] What Is Ransomware?
What Is Ransomware: 5 Tips To Protect Your Business Ransomware can damage and take a heavy financial toll on your business. What is ransomware and 5 tips you can take to protect your business today? For businesses and organizations of all types, the Internet...
[VIDEO] COVID-19 (Corona Virus): Business Continuity Plan Ready?
Coronavirus Spreading: Make Sure Your Business Continuity Plan Is Ready The spread of COVID-19 (coronavirus) has taken root across the country. More and more locations are starting to report cases and this number continues to raise alarm bells throughout the medical...
Know the Digital Threats: 6 Dangerous Malware & How to Stop Them
Know and Protect Your Network From These Malware Threats Every day, new malware is discovered that threatens U.S. business and individual security. Continue reading to learn about six of the most recent named and dangerous malware threats. Back in 2018, U.S. Cyber...
Use SharePoint to Keep Business Data Organized
Metadata Gives You Control of Disorganized Online Filing Systems SharePoint gives you a simple solution to keep your online files organized, using metadata to create customized ways to sort and find the information you need. It’s an all-too-common occurrence....
Is Your IT Company Doing These Bad Cybersecurity Practices?
Watch Out for These Bad Cybersecurity Practices in Your MSP How good is your MSP at providing security for your business? Watch out for these potentially harmful cybersecurity practices in your managed service provider. In a recent speech, Kyle Ardoin, the...
Ransomware Explained…
Ransomware is a form of malware that encrypts your files and demands a ransom payment in exchange for the decryption key. I put together a video that explains how it works and how to stay safe. Take a look and let me know your thoughts… Watch the video below or click...
7 Myths Small Businesses Still Believe About PC Technology
The 7 PC Myths Draining Your Business Technology Budget Evaluating your business technology budget? These 7 PC myths could be costing you a lot of money. From slow computers to hacker vulnerability, see how to fix it. Think you’re saving money by keeping those...
Bolster Cybersecurity Readiness with Strategic Investments
Bolster Cybersecurity Readiness with Strategic Investments Protecting your organization from cybercriminals is gaining complexity and requiring more resources than ever before. Do your leaders understand the implications of a lack of cybersecurity funding? Every...
These Phishing Headlines End Up Fooling The Smartest IT Professionals.
Modern Phishing Email and Article Headlines That Even Fool Savvy Tech Professionals Learn more about the kind of email phishing headlines that end up fooling the smartest tech professionals, and how you can better protect your business. Any tech professional worth...
Hackers Increasingly Targeting Business Conversations
‘Conversation hijacking’ Seeks Sensitive Business Intelligence Your employees probably know not to open unexpected file attachments or click on random links, but what if an attachment arrives as part of an email conversation with trusted colleagues?...
January 28th: Data Privacy Day
Data Privacy Day commemorates the anniversary of the signing of the first international treaty focused on data protection. Here’s how you can get involved. January 28th, Data Privacy Day 2020, is here. First introduced in January of 2008, Data Privacy Day...
What You Need to Know about Cyber Security
Cybersecurity education is essential in order to keep businesses one step ahead of this evolving space. Learn about types of attacks and preventative actions. Cyber solutions are the future of business, with innovation such as the Internet of Things (IoT) gaining...
Scammers Convinced Erie Employee to Wire Million Dollars
Small Town Reeling After BEC Scammers Get Employee to Wire $1M Would you fall for this scam that cost a small town $1M? Find out what a BEC scam is, how it works, and what you can do to keep your company from falling victim. What would you do if you found out your...



















![[Video] What Is Ransomware?](https://compnetsys.com/wp-content/uploads/2020/03/Screen-Shot-2020-03-08-at-10.21.06-AM-400x250.png)
![[VIDEO] COVID-19 (Corona Virus): Business Continuity Plan Ready?](https://compnetsys.com/wp-content/uploads/2020/03/Screen-Shot-2020-03-05-at-8.24.39-AM-400x250.png)








