Blog / Reports / Resources
10 Ways to Maximize Amazon’s Alexa for Business
We all wish that we had a personal assistant who would manage all aspects of our lives. Wouldn’t it be great to have someone who would order your Uber rides while telling you about the newest and greatest restaurant in your area? And wouldn’t it be even better if that...
When Is It Time To Think About Replacing My Aging Server?
Server hardware is the backbone of all that you do in your business. With the appropriate hardware, your company can remain competitive in a world dominated by tech. Needs such as connected devices, analytics-driven processes, and social media marketing are reliant on...
Phishing Season Is Here – Do Your Employees Know What To Look For?
Tax season is one of the most active times of the year for cybercriminals – without the right IT security support, your business could be an easy target. It’s that time of year again – the IRS, state tax agencies, and finance professionals across the...
The Difference Between Business and Home Phone Services
If you think that all telephone services are equal and that there’s no difference between a business phone and a home phone system, you’d be wrong. In fact, there are several differences between a phone used for business and a phone used for personal calls, including...
Are Emails Compliant with HIPAA Laws?
Healthcare providers are searching for simpler ways they can communicate with patients. It can be tedious to schedule all communication in person or over the phone, so medical professionals are looking for another way. Email has become a popular form of communication...
Apple Products Not Immune to Meltdown or Spectre
The year 2018 started with a Meltdown that even Mac and iOS users aren’t immune to. Meltdown is a flaw in processors that allows a hacker to gain access to the personal data stored in your computer. Meltdown, and the similar Spectre were discovered January 3rd. They...
Major Security Flaw Discovered In Intel Processors
Potentially every Intel processor sold in the last 10 years could have a critical security vulnerability that puts users at severe risk. It’s often these days that poor IT security comes down to something like human error, and lack of awareness on the...
The Risks Multifunction Printers Pose To Your Healthcare Practice
This often-overlooked security gap can create a surprising number of serious security risks. Multifunction printers are great tools, offering your team the ability to do just about anything their duties would require them to do from a single piece of hardware....
Did You Know That Texts Could Be a Threat to Your HIPAA Compliance?
Text is an umbrella term that covers any electronically transmitted written message between two devices—And it’s is a widely used form of communication today. Texts are showing up in both our personal and work lives on a daily basis. In fact, even medical practices...
Is Microsoft Office 365 a Cloud or Software as a Service?
This is a question that comes up all the time—Is Microsoft Office 365 considered a cloud solution or Software As A Service? I guess it all comes down to interpretation. Cloud technologies are all the rage these days. Businesses now have many options when it comes to...
Healthcare and The Threat of Ransomware
It’s no secret that the healthcare system has been wracked with ransomware attempts. In fact, it was one of the main concerns for 2017. This is due to the large amount of personal information that’s in the hands of the healthcare providers. All this private data is an...
Is It Time To Retire That Old Server?
You may have been using your server for years, and haven’t noticed any decline in performance. But what if I were to tell you that servers lose efficiency the longer you use them? It’s important to use devices that are up to date and function at peak performance—Which...
Employee Awareness Training—Your First Line of Defense Against Cyber Threats.
An increasing number of information security officers agree that awareness training for employees is the number-one defense against cybersecurity threats. In fact, the nation’s first Chief Information Security Officer (CISO), Greg Touhill, said that if he had extra...
2017 Cost of Data Breach Study: United States
The 2017 Cost of Data Breach Study is an annual study that looks at the cost of data breaches in companies, focusing on different countries such as the United States. This study gives a good idea of the effects a data breach can have on a person and their business....
How Scammers Use Familiar Phone Numbers to Steal Your Information
Scam phone calls aren’t a new thing, but today’s scammers are now bolder and more sophisticated. In 2010, more than 84,000 people reported phone-related scams to the Federal Trade Commission (FTC). Scammers can spoof phone numbers from your local area code or a number...
Experts Rush to Get Ahead of New Ransomware Attacks
Ransomware is now a household name, and there’s no going back. Even though cybercriminals have been using ransomware for years now, it wasn’t until the global WannaCry attack that awareness reached critical mass. Doctors and nurses went to work as usual...
Be Prepared to Combat Insider IT Security Risks in 2018
Did you know that in 2016, IBM found that 60% of all cyber attacks were carried out by insiders? Of these three quarters were due to malicious intent, and one fourth due to negligence or error. Accidents: According to Verizon’s 2016 Data Breach Incident Report,...
Don’t Wait To Start Training Your Employees To Protect Your Business During W-2 Phishing Season
W-2 Phishing season is about to begin – without the right IT security services, your business will be left vulnerable. You and I know that effective communication with co-workers and clients is crucial, but are you sure your employees are practicing safe...
5 Tips For Avoiding Tax-Related Identity And Data Theft
Theft and fraud are serious causes for concern both in and out of the office, which makes education and awareness on the subject crucial. Cybercrime comes in many forms and uses many different tactics to put valuable data in the hands of hackers and scammers. Often a...
How to Access All Documents in Word
Microsoft Word is what many of us use to read and create new documents. This might mean writing essays for school, novels in your free time, or step by step instructions for work. Whatever you’re doing, it’s important that you be able to access your files...
Customize the Ribbon Bar in Microsoft Outlook 2016
How many emails do most business people send each day? Email is the most popular form of business communication and it’s going to increase according to the 2014-2018 Email Statistics Report, by The Radicati Group. Here are some interesting statistics highlighted in...
Is It Time for An Upgrade of Your IT Management?
There’s no denying that in today’s world, information is more accessible and easier to obtain than ever before. From the Internet, tablets, laptops and even your smartphone, information can be accessed anytime and from anywhere. But do you know all the “ins and outs”...
Ensure Your Cybersecurity For 2018
Cybersecurity, no matter the size of your business or how many employees you have, is a vital part of today’s business. Everyone in your organization must be up to date on how to spot a cyber threat and what to do about it. In addition, there are some fundamental...
Why You Should Create a Business Continuity Plan For 2018
Data loss is always a concern for businesses, and now with cloud storage, there’s more of a concern than ever before. “It can’t/won’t happen to me” attitudes among small businesses often end in disaster, costing their owners a pretty penny. Reduced profits, lost...
5 Reasons Why You Need to Make the Switch to Microsoft Office 365
If you run a business, chances are that you’ve thought about moving to an online productivity suite. The two most popular in recent years is Google’s G Suite and Microsoft’s Office 365. Touted as “innovative” and “the next big thing,” Microsoft’s...
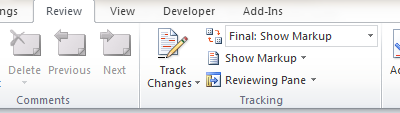
How to Use The Track Changes Feature in Word 2016
Microsoft continues to add exciting features to Word with each new version that’s released. The “Track Changes” feature has been around since Word 2003, and it still works the same today as it did back then. When creating a Word document there’s nothing extra you need...
Weekly Tech Tip: Make backup copies of important business data and information
Regularly backup the data on all computers. Critical data includes word processing documents, electronic spreadsheets, databases, financial files, human resources files, and accounts receivable/payable files. Backup data automatically if possible, or at least weekly,...
When Was the Last Time You Tested Your Business Backups?
Best Practices for Testing Data and Application Backups. Data protection is essential for all businesses today. The most important reason is to prevent monetary loss. If you lose your information it can lead to reduced productivity, lost sales, a harmed...
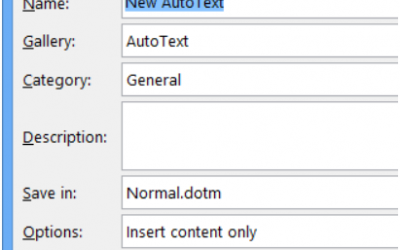
How Do I Make my AutoText Entries Created in Microsoft Word 2016 Available in Microsoft Outlook 2016?
The AutoText feature in Word 2016 (and older versions) can make typing long or complex words much simpler. For instance, let’s say you are writing a paper on the psychological effects of war on soldiers. Imagine having the type the word “psychological” over and over...
8 Easy Steps To Thin Your Bloated Inbox For The New Year
The new year is right around the corner. Thinning your inbox before next year may seem like a daunting task. It doesn’t have to be when you use our 8 easy steps and the tools we recommend. You will have that streamlined inbox of your dreams and a happy mail...
10 Time-Saving Tips For Microsoft Word
Using Word more efficiently is as easy as figuring out the tricks, shortcuts, and features that can make simple tasks even simpler. Microsoft Word is not exactly a new programme. having been on the market since the early days of home PCs. However, new versions have...
Top 12 Tech Gifts of 2017: Sphero R2-D2 & BB-9E
We like tech, it’s what we do. As the holiday shopping season kicks into overdrive, we are bringing you 12 of the most requested, most wanted tech gifts for 2017. Check back each business day between now and December 19th for another must-have tech item and why you...
How To Secure Your Passwords in the New Year
With the approaching new year, it might be time to start thinking about ways that you can improve your life. Some common resolutions include losing weight, exercising more and spending less. Have you considered bettering your digital life as well? Why not take steps...
10 Business Intelligence Trends To Follow In 2018
Getting more out of your business data is quickly becoming an industry all its own, and there are some exciting things on the horizon to help you do more, learn more, and grow more. Data has long been your business’ most valuable and essential asset, and...
Top 12 Tech Gifts 2017: TCL S405 4K HDR TV
We like tech, it’s what we do. As the holiday shopping season kicks into overdrive, we are bringing you 12 of the most requested, most wanted tech gifts for 2017. Check back each business day between now and December 19th for another must-have tech item and why you...
Why Is Everything In Tech “As A Service” These Days?
Leading ‘As-A-Service’ Trends In Technology And What They Can Do For Your Business The advent of cloud computing brought with it more than just a place to store data, the cloud could be used for running, as well as building, applications and other...
7 Tools Businesses Can Use to Automate Their Social Media Presence Today
Everyone with something to market, whether it is a business, service or product wants to stand out and get the public’s attention. We want to be the website that people visit for whatever it is that we are selling. Social media can be a great way to get our product or...
Top 12 Tech Gifts for 2017: Samsung Galaxy S8
We like tech, it’s what we do. As the holiday shopping season kicks into overdrive, we are bringing you 12 of the most requested, most wanted tech gifts for 2017. Check back each business day between now and December 19th for another must-have tech item and why you...
Reasons You Must Update Your Software
Software updates are often seen as an interruption to people when they are using their devices. Who wants to stop and take time to update their JavaScript or iTunes? The answer is, those who wish to have the highest performing software that is secure and easy to use....
Top 12 Tech Gifts 2017: SanDisk Ultra Dual Drive USB Type-C
We like tech, it’s what we do. As the holiday shopping season kicks into overdrive, we are bringing you 12 of the most requested, most wanted tech gifts for 2017. Check back each business day between now and December 19th for another must-have tech item and why you...