Blog / Reports / Resources
The Security Issues Caused By Misdirected Emails
When we consider the security of our business technology, we often think of scams or phishing e-mails. These get easily shrugged off, as we assume no one would fall for e-mails that simply ask for money or state other falsities such as your having won a lottery in...
The Comprehensive Guide to Understanding and Stopping Ransomware
Cybercriminals are everywhere. Both domestically and around the world, countless hackers work day in and day out to penetrate the digital defenses of businesses just like yours, using a variety of proven, effective, and ever-evolving methods. Whether they infect your...
Three Surprising Cybersecurity Mistakes Law Firms Make
Law firms once considered themselves to be immune from cyber attacks. However, this is no longer true. In fact, last year alone, cyber attacks against law firms increased. One report estimated that one in four law firms in America had suffered a significant data...
Meltdown and Spectre Update
With TV shows like Black Mirror captivating audiences around the world, it’s no wonder this addiction to technology is also reflected in the marketplace. This theatrical fiction became true when it revealed the vulnerabilities in technology. The press named them...
Introducing…The Facebook Tango
Do you like to dance? Dancing is both a science and an art. The waltz is a beautiful and romantic flowing dance, the foxtrot involves intricate alternating fast and slow steps, and the tango is rigid with its pace starting slow and increasing in intensity. Each of...
5 Things Your Healthcare Organization Needs From an IT Provider
Healthcare is a complex and tightly regulated industry, which requires a careful and thoughtful approach to technology and its place within your organization. Technology has an incredible capacity to revolutionize the way you interact with patients and provide patient...
Be a Social Superstar: The Unofficial Guide to LinkedIn Etiquette
The world of social media has only been around for about 15 years. From MySpace and LinkedIn to Instagram and Snapchat, there are a variety of social platforms to suit every person and every purpose. Younger generations not only accept that much of their day-to-day...
Cyberattacks: How to Prevent Online Terrorism
These days it seems like no one is safe from a cyber attack. Small businesses, however, are especially vulnerable because of their value and the fact that they’re easy to infiltrate. Larger companies tend to have better measures in place to prevent attacks....
Legal IT: Will Machines Take Over the World?
This is what people sometimes say when you start talking about machine language and artificial intelligence. Though it’s true that a computer can perform long, complex mathematical computations, it could never understand a small boy’s love for a cute puppy. All those...
Cubicle or Couch: Which Works Better?
Washington State’s New Proposed Telecommuting Bill If you ask anyone about their daily commute, you’re likely to hear tales about traffic woes, time complaints, and grudges against gas prices. By contrast, someone who works from home will boast of a...
Facebook: Making Changes With You in Mind
When Facebook first launched back in 2006, the world was introduced to a brand-new way of communicating. Friends and family that lived hundreds and thousands of miles away from one another now could bridge the distance. If you have been living under a rock for the...
The Oracle for Cybersecurity
Cybersecurity is a big, scary word with big, scary implications. The word conjures mental images of a dark room and someone in front a dimly lit computer. The black screen flashes green and is dotted with lines of code entered by a nameless, faceless “cyberterrorist”...
The Future of Big Data and the Legal Industry
There’s no doubt that Big Data, Data Mining, and Machine Learning have changed every industry on the planet. Recent political campaigns were won by experts who knew how to use all data available regarding key factors. Many were surprised to learn how certain types of...
The Future of Internet of Things (IOT) And The Risks (And Benefits) For Business Owners
The Internet of Things (IOT) is simply the connection of devices to the internet (and/or each other) with an on/off switch. Your phone, tablet, and laptop computer are all connected to the internet, and for some each other, with an on/off switch. But this isn’t...
RANSOMWARE IN REAL TIME
Technology is advancing faster than ever before. We can now connect and create on a broader scale than many ever thought possible. However, as our technology advances, people are questioning the security of these cutting-edge systems. While most of our private and...
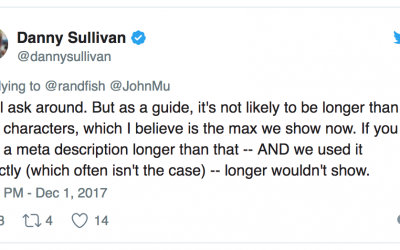
Google Extends Search Result Snippets
First impressions are important. This is even more so in the world of technology. When searching for a company online, your first results appear in a small 160-character snippet. Now Google has officially extended the search results snippets to a maximum character...
Marketing with LinkedIn: The Secrets to Masterful Marketing
LinkedIn is the largest professional marketing site with 500 million users, and 40% of them use the platform daily. LinkedIn is still growing in popularity and remains one of the best online platforms to market your business. Here we’ll discuss some ways to...
How to Consolidate Duplicate LinkedIn Profiles
Occasionally, we all set up duplicate accounts on sites without realizing it. A spouse, friend or employee may have set up an account for you on LinkedIn trying to be helpful. Though it can be a bit inconvenient, it’s fairly easy to fix. At this time, LinkedIn...
Introducing Alexa for Business – Changing the World One Company at a Time
The world is evolving incredibly fast with the help of various technological advancements. Both our homes and our offices are becoming more efficient than ever before. Previously, screens of all shapes and sizes were dominating the marketplace, but now, we’re...
LinkedIn: Brands and the Rules of Engagement
Social is here to stay. That’s the unanimous sentiment regarding social media as a communication tool – and as a marketing channel. LinkedIn launched publicly before Facebook (2003 and 2006, respectively), and in these past 15 years we’ve seen an evolution, and some...
Evolving PCI DSS 3.2 Requirements Become Mandatory on February 1, 2018
The latest updates from the Payment Card Industry Data Security Standard, known as PCI DSS 3.2, will become mandatory on February 1, 2018. This will affect all merchants and service providers who accept credit card payments from Visa, MasterCard, Discover, and...
Do You Know About This Compelling Grant Available for Canadian Businesses?
The Canadian Internet Registration Authority (CIRA), incorporated in 1998, is a member-driven not-for-profit organization with approximately 15,000 members and growing. The not-for-profit organization manages the.CA Internet domain, as well as the entire...
WebMD and Alexa Join Forces
Alexa, Amazon’s incredibly smart voice-activated assistant, is capable of just about anything – from ordering a pizza to calling a taxi to turning on the smart bulbs around the house. Alexa truly enhances the lives of those who use it, and it’s recently...
Dark Web Monitoring Keeps Your Information Safe
Many of us are guilty of using the same password, or a variation of the same password, for our personal and business-related accounts. Unfortunately, these bad password habits only make it easier for hackers to steal our information. When they do, they hold that...
Technology Advances Bring the Future of Healthcare to Life Today
The adoption of seemingly futuristic technologies is creating a new reality in healthcare today. The following are some of the remarkable healthcare technology advances of 2017. The Leadless Pacemaker The pacemaker has come a long way since the 1960s when investor Dr....
Connect with Businesses on LinkedIn
LinkedIn is the most popular business and employment-focused social networking site around. Whether you’re happily employed at a fantastic company or you’re still searching for your dream job, it’s simply a must-join site for your professional...
How to Remove Rogue Employee Profiles from Your LinkedIn Company Page
Employees on your LinkedIn Company Page are people who affiliate their work experience with your business. When LinkedIn members add or edit a position on their profile, they specify the company they work for. If they select your company from the LinkedIn list, the...
Amazon’s Echo for Visually Impaired Employees
If you employ a person who is blind or visually impaired, you know that you must make accommodations to minimize or eliminate workplace barriers. By doing this, you not only ensure their safety but their productivity. In some instances, making these accommodations can...
Mattel CEO Knows The Future Of Business Is In Tech
Even leaders in tech-adjacent fields — like the toy industry — know the importance of investing in technology expertise and a more robust IT infrastructure. As much as we try to predict the future, it’s never been easy. The catch has always been that...
Meltdown and Spectre Spawn New Round of Phishing Scams
The recent announcement of the vulnerabilities found in the Intel, ARM, and AMD processors has sparked a new phishing campaign and not the good kind of fishing with bait and largemouth bass. Although, these hackers are using a particular kind of bait. While Meltdown...
Rogue Employees and How To Stop Them
Technological advancements have, without a doubt, had a positive impact where your business is concerned. But they have also led to hacking, data breaches and the likelihood that rogue employees will use tools to jeopardize the security of your data. What is a Rogue...
Is LinkedIn Premium Really Worth the Splurge?
We know LinkedIn is the most popular ‘social network’ for professionals in a wide variety of industries. It’s filled with fantastic features and functions that will propel your career or business in terms of expanding your professional network and...
How to Consolidate Two LinkedIn Profiles
Accidentally creating two LinkedIn accounts is a common mistake. You may have created the accounts years apart, having forgotten that the first account existed, or maybe you were invited by different users based on different email addresses. Whatever the case, there...
Healthcare and The Threat of Ransomware in 2018
It’s no secret that the healthcare system is wracked with ransomware attempts. In fact, it was one of the leading concerns for 2017. These ransomware attempts are due to the significant amount of personal information that’s in the hands of the healthcare providers....
5 Tips For Writing The Perfect InMail Message To Make LinkedIn Connections
LinkedIn’s InMail can be a powerful communication tool once you’ve figured out to craft messages people will actually want to respond to. Anyone who has had a completed LinkedIn profile for any length of time will have at least a passing familiarity with...
Windows Update and Antivirus
Microsoft has identified a compatibility issue with a small number of their antivirus software products. The compatibility issue arises when antivirus applications make unsupported calls into Windows kernel memory. These calls may cause stop errors (also known as blue...
Does Your IT Have You Feeling Snowed Under?
Information Technology is a critical and often confusing part of your business operations – which is why great IT support makes all the difference. As technology becomes more and more integral to the way businesses do business, making sure you have the right...
Windows 10 Enterprise: How It Facilitates Greater HIPAA Compliance
Since the implementation of HIPAA in 1996, several revisions were made to it including the ARRA/HITECH Act in 2009 and the Omnibus Rule in 2013. But one thing that remains consistent is the overall lack of understanding of this Act. The Health Insurance Portability...
Slack Was “Slacking” Today
The Slack messaging tool suffered a major outage today that left users unable to connect to the service. In a post on its systems status page, Slack reported that their customers were experiencing connectivity issues as a result of the outage: “A majority of customers...
Meltdown and Spectre – How to Handle the Phishing Scam and Other Problems
The most talked about hardware issue in the news right now is the “Meltdown” (CVE-2017-5754) and “Spectre” (CVE-2017-5753 and CVE-2017-5715) exploits. Nearly all the computers around the world are affected by one or both bugs. All the big-name software and hardware...