Blog / Reports / Resources
It’s Time To Bring Back That Lovin’ Feeling
There are few things worse than feeling trapped in an unfulfilling relationship – especially when it’s a vital business relationship. Technology is an integral part of everything your business does, which raises a few important questions about your current IT...
Insider Advice On Managed Security Service Providers
Learn the seven key questions every business should ask when deciding on which Managed Security Service Provider to hire. A Managed Security Service Provider is an extension of your IT services department that focuses solely on the security of your company. The...
Hey It’s Valentine’s Day Soon: Do You Love Your IT Company?
There are few things worse than feeling trapped in an unfulfilling relationship – especially when it’s a vital business relationship. Technology is an integral part of everything your business does, which raises a few important questions about your current IT...
IT Strategy – Why Businesses Are Turning To Managed IT Services
Partnering with a Managed Service Provider can offer business owners a way to limit risks and increase productivity. Running a business is hard work, but thankfully there are a lot of tools that can help make it less burdensome. Managed Service Providers...
Happy Valentine’s Day: It’s Time To Bring Back That Lovin’ Feeling
There are few things worse than feeling trapped in an unfulfilling relationship – especially when it’s a vital business relationship. Technology is an integral part of everything your business does, which raises a few important questions about your current...
Your Step By Step Guide To Transitioning To VoIP
Get untangled from your landline, and let VoIP boost your business’ efficiency, reliability, and quality. A recent study revealed that 94% of business’ marketing budgets are spent trying to get consumers to call. If businesses are paying so much of their...
Businesses Can Now Schedule Instagram Posts
Following in the footsteps of other social media giants, Instagram is now trying to add flexibility to their platform in order to attract more business owners. Since their inception in 2010, Instagram has had no way to allow users to schedule posts. Posting manually...
Microsoft Teams: Business Without Boundaries
Where you work is no longer defined by four walls and a door – not even by cubicle walls. Gone are the days where productivity requires a set geographical location, at least for some roles, anyway. Recent years have seen the rise of the remote workforce that...
10 Microsoft Office Features You Will Love
Microsoft has dominated the business world for a long time. It is on every computer, in every office, no matter if that is a library or a Fortune 500 company. We use Microsoft Word to create the newsletters for our businesses and collate our data with...
Meet The New Internet Security System Built Into Google Chrome
With the growing threat of viruses, worms, scams and phishing schemes, it seems impossible for computer users to avoid a cyber breach these days. In spite of a massive focus on preventing cybersecurity breaches, it’s still possible to wake up one morning to news...
CEOs and Cybersecurity Specialists: It’s Time to Talk Tech
CEOs are some of the busiest people we’ve ever met, and we’ve met a lot of people. What do CEOs do? The answer to this question is as unique as the company a given CEO is busy running. If we polled every CEO we know and asked what their primary goal is, we’d...
Wi-Fi Calling is Making Life Easier
Wi-Fi isn’t just for your computer anymore. These days Wi-Fi is changing the way we make calls from our cellular phones, and this way of calling has a lot to offer. Instead of using the minutes from your cellular plan, you can make a call by connecting to a Wi-Fi...
How Business Intelligence Tools Help Small Business Make Big Changes In Profits, Efficiency, And Security
Businesses store data like we store clothes. How many times do we step into our closets and wonder “When was the last time I wore this”? This is similar to what we, as business owners, should be asking ourselves. “When was the last time I used this data?”...
Nine Must-Have Cybersecurity Strategies For Small Businesses
Your small business is at risk. There’s no way to sugar coat it and no way to say it any more plainly. Every day there are criminals targeting businesses. Why? Because they want your money, they want your private data, or they just want to cause trouble for you. It...
Business Intelligence Tools For Small Business
We all wish we had a magic crystal ball that would make our lives easier, whether that means knowing when to change our hairstyle, or when to apply for that dream job. In business, there is no magic crystal ball that will tell us what’s going to happen, but with...
The Invisible Dangers of Public Wi-Fi
Public Wi-Fi may be convenient, but it’s not necessarily safe. Are you putting your data at risk when you connect? Have you ever been to a Starbucks? Stayed in a hotel? Taken a flight or had a layover? It’d be hard to find a person who can say...
Money Talks: Are you using every tool available to help your clients make the right decisions with their finances?
There is no such thing as a safe investment. Investing is a scary business. Most people prefer to work with financial experts when it comes to finding the best place to put their money. Just like them, you’ve worked hard for every penny, and you don’t want to...
BYOD in the Workplace: Pros vs. Cons
Many modern companies are now implementing BYOD policies that permit employees to work with their personal laptops, tablets, and smartphones. Bring your own device (BYOD) to work. Who would have thought, even twenty short years ago, that you could use a little phone...
CEOs and Cyber Security
Technology is amazing when it works for us, but not so amazing when it doesn’t. New tech innovations have helped businesses grow at an exponential rate, but as business technology grows, so does cybercrime. Protecting a business’ security is not only a job...
Boost Employee Awareness and Lower Your Insurance Premium
Cybercrime is a common part of business these days. Even if you haven’t encountered a hacking or malware incident at your business in recent years, the fact is that cybercriminals are coming up with new methods of stealing and compromising sensitive business...
What Features Do the Various Wireless Carriers Offer?
We are addicted to our phones. These little boxes of life give us the capabilities to seamlessly stream Netflix or Hulu, update spreadsheets and respond to emails for work, all from wherever we are at the moment–whether we’re on a train commuting to and from...
Why You Should Use an Uninterruptible Power Supply (UPS)
In a world that seems to be growing more technologically savvy every day, we must be prepared for anything, from phishing scams to ransomware attacks. But, what if the threat to your business and data isn’t from technological warfare? What if something...
Are you considering VMware Fusion 10 or Parallels Desktop 13 for your small business?
Do you want your Mac to work like a Windows machine? There are many reasons that small to mid-size businesses like yours want this kind of functionality, but the most common reasons are: I don’t like Macs. My employees don’t know how to use Mac OS. I want to make use...
The Gaps in Data Security That Could Threaten Your Company
In the fight to avoid security breaches, one area has proven over and over to be the weakest link. It’s the human factor. A survey done by CompTIA shows that human errors are responsible for 52 percent of all security breaches. Each day employees open emails;...
Ransomware Preys On Your Employees
Ransomware has quickly become one of the biggest cyber threats to businesses today, especially given the recent Wanna Cry epidemic that infected hundreds of thousands of IT systems in more 150 countries. This kind of malware presents serious data integrity and...
Bye, Bye Server App! How to Run A Secure File Storage Server Without macOS Server VPN.
It’s been coming since 2010—That’s when Steve Jobs announced that Apple was going to kill XServe, its enterprise-level server hardware solution. Ever since that time, Apple has been slowly backing away from the server market. This slow death of Apple server ambitions...
Isn’t It Time to Migrate to Office 365?
If communication is the key to personal and career success, then we should be doing everything in our power to ensure our communication lines are well established, extremely efficient, and thoroughly secure. Migrating to Office 365 might be what your business needs to...
8 Easy Ways to Secure Your Data
Data is the foundation of any business. Building a business without protecting your data is like building a home on wet sand, leaving the tide to sweep it away. With all the ways data is being stolen today, there are a few steps you should take to build a secure...
6 Ways to Prevent Cybersecurity Breaches
It is becoming commonplace to hear of big security breaches. Consumers wonder how this keeps happening. It would seem like every company should be taking their data security very seriously. After all, a data breach typically costs millions of dollars and tarnishes the...
Another Ransomware Attack Leaves Hospital Offline
Once again a hospital has been hit with ransomware, causing staff to rely on pens and paper to keep records and maintain patient care. On January 11th, Indiana’s Hancock Regional Hospital was infected with ransomware by an “unknown party” that has...
Beware of This Ransomware Strain and Its Dangers for Cloud E-mail.
We recently came across some chilling news. A white hat hacker developed a working “Ransomcloud” strain, that encrypts cloud e-mail accounts like those in Office 365, and it does this in real time. This strain uses a smart social engineering tactic to...
Artificial Intelligence Is Transforming Email for Law Firms.
The problem with email Email has been around for decades, and yet it hasn’t changed much. We must sort through dozens of messages to find the ones that matter. Only a small percentage of the emails we receive are important to view; the rests are advertisements...
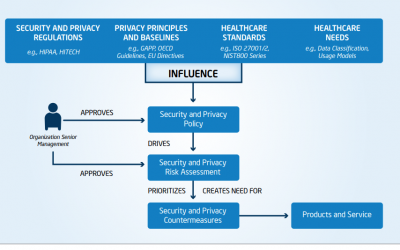
Ransomware and Malware Threaten Patient Safety.
Not only are healthcare organizations at risk due to cybercrime, so are their patients. Imagine having to turn away patients because your computers are shut down due to a ransomware attack. Or, having to “blindly” treat your patients because you...
When Technology Wins, Consumers Win
More than 20 years ago, retail began to shift from the shopping mall to online shopping. Amazon.com, the brainchild of Jeff Bezos, had been around for a few years. It was born as an online bookstore in 1995. A brilliant premise, Amazon offered a digital “storefront”...
Ontario’s Fair Workplaces, Better Jobs Act Becomes Law
There’s some good news for the 1.4 million people of Ontario: The Fair Workplaces, Better Jobs Act, 2017 (Bill 148) was passed into law on November 22, 2017, and took effect on January 1, 2018. The bill includes better wages and working conditions for workers...
Data Security for Beginners: 6 Tips to Maintain Information Privacy Online
January 28th, 2018 is Data Privacy Day, an international effort led by the National Cyber Security Alliance (NCSA) annually for the purpose of raising awareness about the importance of safeguarding data. Data Privacy Day commemorates the signing of Convention 108,...
It’s Data Privacy Day… Do You Know Where Your Data Is?
If you’re not doing everything in your power to protect your data, you’re leaving your most valuable business asset open to cybercriminals! January 28th, 2018 is Data Privacy Day, an international effort led by the National Cyber Security Alliance (NCSA)...
Your #1 MUST-DO New Year Resolution For 2018
With every New Year comes the chance to reset priorities. Unfortunately, when the topic of implementing a data recovery plan comes up, the comment we most often hear is “I know I should, but I haven’t gotten around to it yet…” So…what if the pilot on the next flight...
Best Tips for Using Public WI-FI Safely During Mardi Gras
With Mardi Gras fast approaching, there will be a million people in New Orleans all looking for fun times, and good Internet connections. (Okay, maybe not all one million of them — but enough to keep you on your toes.) Using public WiFi safely during Mardi Gras will...
The Legal Risks of Cyber Theft
With the rising number of cyber thefts in the US, numerous lawsuits have been filed against businesses and organizations. In general, the public expects that their bank will take sufficient action to stop data theft. We expect this of the federal government, credit...