Blog / Reports / Resources
Happy Labor Day
Happy Labor Day (Labour Day – International Workers Day – May Day)! You’ve worked hard all summer. This Labor Day before going back to work and back to school, take some time to relax and enjoy one more backyard barbeque, one more trip to the beach, one more...
Happy Labour Day Everyone!
Happy Labour Day (Labor Day – International Workers Day – May Day)! You’ve worked hard all summer. This Labor Day before going back to work and back to school, take some time to relax and enjoy one more backyard barbeque, one more trip to the beach, one more...
How Can ATP And Safe Links Help Me Prevent Hacker Attacks?
What Are ATP and Safe Links? ATP is a form of security feature developed by Microsoft for Office 365, an acronym for its Advanced Threat Protection software package that users are able to purchase for improved security features within the program. They are recommended...
Education: Digital Literacy and Access Are No Longer Optional
The debate about whether or not tech should be in schools has largely been put aside, technophobes and Waldorf School Curricula notwithstanding. In its place, education stakeholders must sort out the edtech baggage of privacy concerns, equity & accessibility,...
Lightning Fast Guide to Using Slide Master in PowerPoint 2016
Do you find yourself making a lot of formatting changes to your slideshows? Do you have to constantly rearrange the placeholders in each slide so things look the way you feel they should? Do the color options never seem to match what you need? Would you like to add a...
NOAA Predicts Less Active Atlantic Hurricane Season But What Does That Really Mean?
NOAA has revised its May prediction regarding the Atlantic hurricane season, saying that forecasters are now expecting a less intense season than originally anticipated. As we are entering what often proves to be the worst time of year for hurricanes in the Atlantic,...
Is Office 365 Worth It?
A Look Inside a Company Who Has Successfully Made the Switch If you are self-employed or run a business, you more than likely use Microsoft Office in some or most of your day-to-day operations. If you haven’t made the switch to Microsoft Office 365, you have probably...
Important Tips For Law Firms Choosing Outsourced IT Providers
How Does One Choose Technology to Properly Manage People, Planning, and Processing in the Legal Sector? Although law firms are often willing to improve and modernize their level of technology to better serve their clients, they are hesitant, as they do not know where...
BaseStriker Attacks And Defense: What Should Business Owners Know?
BaseStriker attacks are software attacks that computer hackers use in an attempt to break through the defenses of an account or program. These attacks have been developed through unique coding while operating in a phishing-style in recent times. They’ve been so...
Is Human Error the Leading Cause of Data Breaches in the U.S.?
New Study Shows That the Global Cost of a Data Breach Is Up in 2018 The Ponemon Institute recently released its annual Cost of Data Breach Independent Study that was sponsored by IBM Security. This study included two new factors that impact data-breach costs:...
More Than 3M Records Exposed in Q2 2018 Healthcare Data Breaches
A recent study conducted by The Harris Poll on behalf of Scout, a healthcare marketing firm, uncovered some interesting statistics about healthcare data security and public perception. It determined that out of 2,000 US adults, about half are extremely or very...
What Security Precautions Should You Take If Using Snapchat?
What Is Snapchat And What Business Uses Does It Have? Snapchat is a form of now commonly used social media more recent than Facebook, Myspace, or Twitter. It’s unique in that it allows users to create pictures or messages that are only available for a short period of...
Windows 10 Enterprise Is Microsoft’s Most Secure Operating System Ever
Is Windows 10 Enterprise Right For Your Business? With the threats of cyber-attack at an all-time high, there’s no better time to reexamine your company’s operating system to see whether or not it offers the level of protection you, your company, and your clients...
EHR System for Australia’s Northern Territory Nears The Halfway Mark
Australia’s Northern Territory – 1.35 million square kilometers with a population of an estimated 250,000, is not one of the first places you think of when one thinks of installing a state-of-the-art Electronic Health Record (EHR) system. Nonetheless, the Northern...
What Can Companies Do To Prevent Privacy Violations?
Whether it’s physical, virtual, or in the cloud, discovering and blocking sophisticated threats in the network is at the forefront of every company’s mind. However, businesses are finding that more and more data violations are taking place when network security...
How Do I Find the Right IT Managed Services Provider?
Identifying the Right IT Services Provider for Your Business IT service providers, also called managed services providers (MSPs), are in the business of managing a company’s IT needs. IT service providers can offer their services both remotely and on-site. They...
7 Things to Look for in an IT Company for Your Dental Practice
More and more dental practices are outsourcing their IT needs, and are reaping the benefits of such a choice. By using a vendor, you are able to maintain better control of your IT budget, you can leave the headaches and complexity of IT technology to the experts, and...
Major Advance in EHR Interoperability Poised to Take Place This Summer
EHR interoperability – considered by some to be the “holy grail” of electronic health record systems – may be a little closer than you think. This summer, a new architectural innovation will be implemented that is guaranteed to positively impact the way different EHR...
What is a Blockchain? Can It Create New Business Opportunities?
What’s A Blockchain? A “blockchain” is basically a financial record similar to that of a spreadsheet, only for bitcoins and other forms of cryptocurrency available publicly and online. As the use of cryptocurrencies has evolved, it has created some innovative business...
The Critical Aspects of Mandatory Data Breach Notification That You Need to Know About
As of 22 February 2018, the Notifiable Data Breach (NDB) scheme went into effect and included in its requirements is a mandatory data breach notification. Failure to correctly notify those affected by an eligible data breach can result in fines of up to $2.1 million,...
Unified Endpoint Management (UEM): Can This Help Streamline Cloud Security?
What Is UEM and Cloud Security? As technological devices continue to diversify, there is increased demand for streamlining control systems for security. According to Techopedia, Unified Endpoint Management (UEM) is a new digital system that integrates the range of...
Bralin Technology Solutions Ranked Among Top 501 Global Managed Service Providers by Channel Futures
11th Annual MSP 501 Identifies World’s Most Forward-Thinking MSPs & Leading Trends in Managed Services August 21, 2018: Bralin Technology Solutions ranks among the world’s 501 most strategic and innovative managed service providers (MSPs), according to Channel...
Welcome Rabia Tinna
Bralin Technology Solutions is excited to welcome Rabia Tinna to the team! Rabia is joining us as a Help Desk Technician, based in our North Battleford Office. Rabia brings a wealth of education and experience to our company, holding a Master’s of Computer...
You’re A Health Care Organization. You’ve Just Had A Data Breach. Now What?
Of course, you will be living in a kicked anthill for days. The trick is to make sure that all the scurrying around is not just mindless motion, but actually protects the organization by: Meeting legal responsibilities, Protecting the organization’s reputation to the...
Microsoft Launches $4 Million Global Competition For Female Founders
Microsoft’s M12 has recently announced the launch of the Female Founders Competition, a startup initiative aimed at rewarding startup companies founded by women. It will not only identify top female talent within the startup industry but also seek to accelerate...
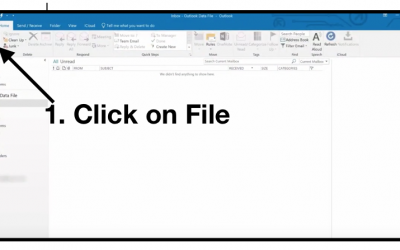
Do You Know How to Add Email Signatures?
Step-by-Step Instructions on How to Add your Email Signature in Outlook, Outlook.com, and Gmail Creating a signature that will leave a lasting impression at the end of an email is essential in today’s business world. However, users often struggle to know which font...
Are You Ready for the Future of Business?
Ushering in the Modern Workplace with Microsoft 365 Do you think your team has the liberty to do their best work? Are they engaged and satisfied on a day-to-day basis? Are you providing your team with the tools that enable them to have a digital, adjustable workplace...
Why Education Should Outsource IT Support
EdTech has a long history of being misunderstood, underutilized, and of lacking support in every way. It is one of those bugaboos in education that seems like such a wonderful idea, but often falls apart in execution as money fears cause administrators to scale back....
Security: Focus On The Fundamentals
Every day, it seems, another security threat is in the news. The latest one involves some flaws in Intel chips that actually introduce a new vulnerability. The patches are out to address this, and hopefully, someone in your IT organization is tracking and applying...
How Difficult Is Collaboration In Today’s Law Firms?
Communication—this is so important for the proper running of any business; however, it is even more essential for law firms where the stakes are arguably much higher. Over the years, communication between attorneys and their clients was a time-consuming process that...
How Can Workforce Management (WFM) Software Help Me?
Workforce management (WFM) software is an all-encompassing term for mobile and desktop programs that are created to support a business at managing its staff scheduling. The software began in call centers and other service businesses that have a large number of workers...
What The Rise In API Data Breaches Means For Your Network
The increasingly digitalized world we live in has a lot of benefits in business and in relationships, but with it also comes a whole new host of problems, including a rise in API data breaches. A number of high-profile companies have been affected by API data breaches...
Third-Party Vendor Breach and Subsequent Delays in Reporting Now Result in Major Problems for an Orlando Healthcare Provider
A recent breach left the protected health information (PHI) of more than 19,000 patients in Orlando, Florida completely exposed online for two months before it was detected. What is more concerning, however, is why it took the group of clinics involved five months to...
Girls in Tech: Girl Scouts of the USA Adds New Badges
Girl Scouts of the USA recently announced the addition of 30 new badges now available for Girl Scouts aged 5-18. The new badges were created to address a number of today’s most important social issues, including environmental advocacy, cybersecurity, robotics,...
Email Scam: Sage and Clare Homewares Business in Victoria, Australia Loses $10,000
How Can I Keep My Business Safe From an Email Scam? Recently, small business owner, Phoebe Bell of Sage and Clare, a popular homeware designer business in Australia, opened up about her company falling prey to email scammers. Sage and Clare lost $10,000 from the...
Do You Know How to Spot Fake Software and Updates? Learn the 7 Red Flags!
If you are connected to the internet, then you are a target for malware, viruses, and hackers. Every day, 350,000 new malware programs come to the surface. Your firewall and anti-virus protection can only provide so much security. That is why it is very important that...
Intel Chip Vulnerabilities: What We Know So Far!
What Do We Know About Terminal Fault (L1TF) Chip Vulnerabilities? Understanding The L1 Terminal Fault (L1TF) Intel has recently confirmed L1 Terminal Fault (L1TF) chip vulnerabilities in its processors that can be manipulated by malware and malevolent virtual machines...
Centers for Medicare and Medicaid Services (CMS) Propose Reducing Submission Requirements for Health IT Security Under MIPS
As providers are all too well aware, their payments from Medicare are affected by their score in the Merit-based Incentive Payment System (MIPS). MIPS imposes a number of requirements; if these are not met, payments may be reduced or denied. The MIPS requirements...
What Are the Top 10 Phishing Email Subject Lines from Q2 2018?
Hackers are constantly throwing in new and clever phishing attacks that threaten email users’ security. KnowBe4, one of the top security attentiveness and simulated phishing platform contributors recently issued the top 10 phishing email subject lines from this...
Why Should My Company Upgrade to Windows 10?
If you are in a startup company or run a small business, the simplest software update can easily cause anxiety for you and your group of employees. Everyone has experienced the update that causes glitches and hiccups that can disrupt the workflow. With that said, why...