Blog / Reports / Resources
What Should I Know About Hashcat?
What is Hashcat? Hashcat is a type of hacking tool, and a password cracker specifically. It was created to be able to hack the most complex of passwords, targeting multiple aspects of coding simultaneously. Additionally, according to online sources including Infosec...
What Can Healthcare Providers Do To Make Cloud Adoption Easier?
Microsoft’s Azure cloud service recently suffered a major disruption at one of its data centers in Texas. A truly epic lightning storm caused even the backup generators to go offline. Every time the center struggled back to a semblance of normal operations, another...
How Can I Optimize My Wi-Fi?
With a range of technology continuing to encompass upgrades and versions improving on previous ones, there are constantly new ways for people to improve their Wi-Fi speed. Considering the most recent developments, the below provides instructions for minimizing...
How Could My Office 365 Be Vulnerable To ‘ZeroFont’ Phishing?
What is ‘ZeroFont’ Phishing? ‘Phishing’ is where hackers attempt to get a user to willingly provide personal information, generally through posing to be someone else. It is one of the more threatening forms of hacking, as it is among the most difficult to protect...
The Intelligent New (and Awesome) Data Types Supported by Microsoft Excel
To date, Excel and similar apps deal primarily with text and numbers as data types. However, that tradition is about to be a thing of the past as Microsoft is adding two new data types to Excel. These data types allow cells to contain rich, intelligent data that can...
CIPA Compliance – What Does It Mean For You?
Schools and libraries applying for E-rate technology funding discounts must be CIPA Compliant. CIPA stands for the Children’s Internet Protection Act and mandates that if an institution is receiving a discount for network and network-adjacent services, then it must...
How Can I Benefit From Keyboard Shortcuts?
What Are Keyboard Shortcuts? Keyboard ‘shortcuts’ are the strategic use of combinations of keys on your keyboard to perform some task in your software more efficiently. There are shortcuts you can use in your file folders, word processing programs, and even for your...
What Should I Know About Fluxion Hacking And Protection?
What is Fluxion? Fluxion is a new program that combines social engineering and technology to trick users into giving up their log-in and password information. This program is a step above Wifiphisher, which lacks the ability to verify WPA passwords. Fluxion takes all...
Migrating Your Healthcare IT To The Cloud: What’s It Gonna Cost You?
You may have an EHR system, decision support systems, purchasing, payroll, laboratory, pharmacy, personnel, finance, planning, and a myriad of other systems running on hardware that’s getting very long in the tooth. Many PCs are still running some older version of...
What’s So Important About My Out-of-Office Message?
Vacation and time away from work is a necessity in order to be able to unplug and recharge. As research often tells us, disconnecting from work, talk around the water cooler, office politics, and even checking email can ultimately help us lead a more productive life....
What Do I Need To Know About The Google Chrome Vulnerability CVE-2018-6177?
What is CVE-2018-6177? Today’s new releases of browser software are supposed to be improvements over past versions in terms of functionality, helpful features, security, and the speed of overall operation. However, these changes often involve new vulnerabilities which...
You’ve Heard Of Smart Homes. What’s a Smart Health Care Organization?
What’s smart about a smart home? Well, you can talk to it. You can tell your phone to tell the oven to turn itself down to 200 degrees. You can tell your thermostat to drop the nighttime temperature to 68. You can start the car from the upstairs guest bathroom. And so...
How Can I Best Protect My Business Entity From Current Hacker Potentials?
Improvements in technology have led to increased connectivity with improvements in security, but have also involved unique vulnerabilities and potential for hackers to access a wide range of information. Particularly problematic to businesses is the potential for a...
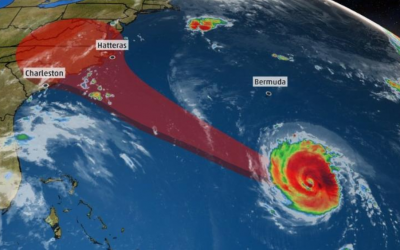
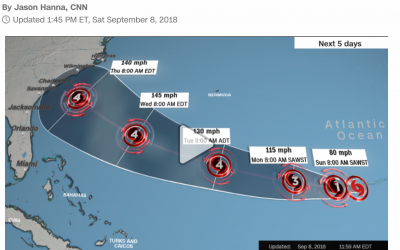
Hurricane Florence Update: Florence Now A CAT4 Major Hurricane
Hurricane Florence strengthens to Category 4 Evacuation Orders Begin in the Carolinas The National Hurricane Center is now saying that Florence has maximum sustained winds of 115mph, with gusts to 140mph. It is now a Category 4 storm and is expected to hit the...
Check Spelling With Microsoft PowerPoint 2016
If you’ve ever attended a high-level education course or business meeting, chances are you’ve come across the PowerPoint presentation. Microsoft’s PowerPoint program has been helping students and professionals organize their thoughts and ideas for decades. From class...
Excel for Mac: The Latest Features
A new release of Excel for Mac came out in January of 2018, and with it, some very useful features were added to its existing capabilities. While some spreadsheet power users tend to shy away from the Excel version for the Mac operating system out of fear they won’t...
How Safe Am I From an IoT Attack at Home and Work?
As convenient as our interconnected world has become, it has also made us vulnerable to an attack from hackers wanting to make a quick buck. Internet pirates are targeting defenseless networks with the sole purpose of hijacking our personal devices for use in their...
Air Canada Data Breach Prompts Enhanced Mobile App Security Measures
Air Canada recently confirmed a data breach occurred between August 22 and 24, affecting users of the Air Canada mobile app. The breach is just the latest in a string of cyber-attacks impacting mobile app users. The Air Canada mobile app has approximately 1.7 million...
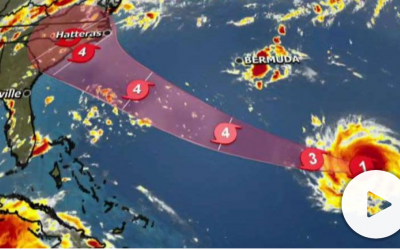
Hurricane Florence: State Of Emergency Announced For Virginia
Hurricane Florence is spinning up to be a Category 4 Hurricane. It’s predicted to make landfall between North Carolina and Georgia this week. Virginia may be impacted when Florence comes ashore at the end of this week. Virginia announces a state of emergency...
Hurricane Florence Is Ready To Impact The SE Coast.
Florence is spinning up to be a Category 4 Hurricane. It’s predicted to make landfall between North Carolina and Georgia this week. Preparing For A Major Hurricane or Tropical Storm When a hurricane is 36 hours from arriving Turn on your TV or radio in order to...
Is Your Cloud Provider Prepared For A Disaster?
When companies fail at or are not prepared for a catastrophe, it’s often because they neglect to think that the unexpected is possible. They often fall into one of two categories: They assume disasters are unpredictable, so why prepare for them? They fall into the...
Do New Laws Improve Employee Stock Ownership Plans (ESOP)?
It seems that small businesses rarely catch a break. Unfortunately, their employees often enjoy fewer perks than those working for larger corporations do. This is primarily because the smaller companies have fewer assets with which to work. Due to the smaller economic...
Health & Human Services OIG Report Finds Maryland Did Not Properly Secure Its MMIS System
An Inspector General’s (OIG) report from the Federal Department of Health and Human Services (HHS) finds that Maryland failed to secure its Medicaid Management Information System (MMIS) against several avenues of attack. What Security Violations Did Maryland Commit?...
Master Google Search In Just 28 Minutes
This month’s training on demand focuses on helping you find the most accurate information you need on Google. We’ll leave no stone unturned in this 28-minute online training session. Learn how to find answers to your queries and questions right through to...
How Can WPA3 Protect Me From Hacking?
What’s WPA3? WPA3 is an improvement to WPA2 security, which is still commonly used after having made substantial improvements over WPA. It is expected to better protect users from software hacking. In partial development for approximately 10 years, this improved form...
What Are The SEC’s Guidelines For Public And Private Company Cybersecurity?
Hand-in-hand with an increased reliance on the internet and networked systems comes to an increased risk for cyber-attacks. Whether conducted unintentionally or deliberately, cybersecurity incidents can wreak havoc on a company’s bottom line, bringing a wide range of...
Are You Spending Enough On IT Security?
IDC Report Focuses on How Real the Threat Actually is for Canadian Businesses How much is your company spending on IT security? According to most analyst numbers, an average of 14% of the IT budget should be shelled out each year to safeguard a business. The reality...
What Should I Know About New Hacking Attacks Against Pairwise Master Key Identifier (PMKID)?
What is PMKID? Pairwise Master Key Identifier (PMKID) is a type of roaming feature in a network. Recent improvements in hacking have been targeting it for exploitation in vulnerable processes, thereby demanding that ongoing security efforts better address it and its...
Clinical Decision Support: When Will Artificial Intelligence Become Intelligent?
Those of us who are in the know about artificial intelligence (AI) in medicine no doubt know that IBM’s efforts to use its Watson system in healthcare have been a mixed bag at best and many of the engineers working on the project have been laid off. What went wrong?...
What Are the Ongoing Challenges to Legal Technology Transformation?
Experts agree that the legal sector is not really on the cutting edge when it comes to adopting the latest technology trends. In fact, with the long-standing history of traditional values, it is rare to see widespread use of information technology (IT) in the...
The Basics of Effectively Scheduling Meetings with Microsoft Teams
Microsoft Teams is a great way to schedule meetings, especially if the participants don’t all work in the same geographic area. It seamlessly integrates scheduling, invitations, updates, and access to virtual meetings. This might sound a bit complicated, but once you...
7 Great Benefits of Using Computer Tablets in Schools
Tablets aren’t just digital babysitters for young kids or fancy versions of ereaders. They offer real value as educational tools. Their versatility, portability, and ease-of-use make them an excellent conduit for learning. Below are seven benefits of using tablets in...
Your Medical Device May Be A Computer. Treat It Like One!
We all know about Food and Drug Administration (FDA) food recalls. Remember the ban on romaine lettuce from Arizona? That was finally tracked down to a contaminated irrigation pipe. Quite a bit of tainted lettuce was eaten or discarded before that happened. The FDA is...
What Are PhishPoint Attacks And How Can I Best Protect Against Them?
What’s PhishPoint? Phishing attacks are attempts to get e-mail recipients to provide sensitive information that can be used by the sender, generally presented as the authority of some account or business. They request that recipients provide information that could be...
What Are the Legal Impacts of California’s Potential Privacy Policy?
California is known for being on the cutting edge of most things, and consumer privacy is one of them. Scheduled to take effect in 2020, the California Consumer Privacy Act gives consumers broader control over how their personal information is used. This was developed...
Using Yammer With Office 365
Social media has become an integral part of everyday life for many people. From Facebook, to Instagram and Snapchat, a growing number of internet users are embracing the power of instant connection. And while this is par for the course for social life, social media...
How Can Instagram Accounts Be Hacked?
What Is Instagram And How Is It Vulnerable? Instagram is a recently created social media site that allows users to share images and videos. It is owned by the same soul that owns Facebook, Mark Zuckerberg. Originally created in the partnership of Kevin Systrom and...
What Is a VPN, How Does It Work and Why Should I Use It?
Does it make you nervous when you consider how much of your personal information is essentially spread all over the internet? In spite of antivirus programs and firewalls, all data is somewhat at risk on the web. One of the most proven techniques to ensure your data...
Microsoft Files Patent Application for Eyewear that Measures Blood Pressure
Why are Tech Giants Diving into the Health Care Business? In a report by Christian Holz and Edward Wang of Microsoft Research, the researchers revealed that Microsoft is creating eyeglasses that measure blood pressure. What Microsoft is calling Glabella, the glasses...
Tropical Storm Gordon Update
Are You Ready For Tropical Storm Gordon? Gordon made landfall over the southern tip of the Florida Peninsula on Monday, September 3rd. It’s now predicted to make its 2nd landfall as a Category 1 Hurricane over the central Gulf Coast from Louisiana to Mississippi...