Blog / Reports / Resources
Building A Network Hackers Can’t Crack A Priority In Australia
Sadly, hackers are something that many companies have to deal with on a daily basis. What might seem like a fairly uncommon problem is actually more widespread than you might imagine. Hackers are a skilled set of individuals but at the same time, they cause widespread...
Understanding the Value of Managed IT Services
Depending on their scope and impact on your workday, tech issues can take hours to resolve, if not days. In some cases, you may spend far too much time tracking down a problem, only to come up empty-handed in the end. In others, such as security breaches, you may not...
Learn the Power of Google Reviews for Local Construction Companies
Reviews, testimonials and referrals are important to growing a contracting business. In fact, reviews are the backbone upon which a business can establish a working relationship with their local community. In today’s world, people can come to know you, like you and...
Why Do Hackers Target Small Businesses?
Why Small Companies is the First Target for Online Hackers According to the SBA, small business employs less than 500 people and realizes less than $7 million in profits annually. This standard defines a small company across the global business world. A large...
How Do You Measure Your Company’s Cybersecurity Effectiveness?
Many companies are finally taking cybersecurity seriously and have implemented programs to meet their organization’s specific needs. Having a program in place, however, is only the first step. Measuring the effectiveness of a cybersecurity plan is equally...
Moving Into A New Office? (Free Guide)
It doesn’t matter whether you are a 10-person team or a Fortune 500 conglomerate, relocating your office is going to take some planning and forethought. The last thing you want is to be forced to close up shop for an extended period, stalling your business due to...
What Are Some Common Myths With Managed IT Services?
Managed IT Services is a transaction often required by businesses large and small in order to operate efficiently. It’s unfortunate that some owners and managers misinterpret the scale of services provided by a Managed IT Provider. To some extent, there is a...
Should Local Companies Outsource IT?
Technology is the backbone of every business from, the smallest family-owned retail store to the largest international corporations. Companies everywhere depend on their technology to help them to reach their goals and stay competitive in a rapidly growing...
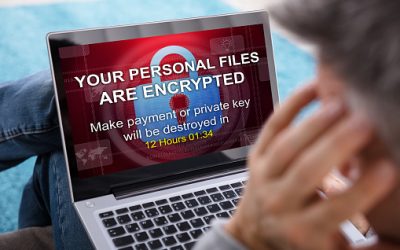
Is Ransomware A Threat to My Business?
What is ransomware? Ransomware is an unusual type of threat because it holds your files for ransom while leaving your systems essentially otherwise operational. A piece of malicious software enters your network and applies an encryption algorithm to your computer...
Moving Into A New Office? Don’t Forget About Your IT Services
If you’ve ever managed your way through moving your company to a new location, you know there are hundreds of details that need attention. If you’re about to do so for the first time, your to-do list is likely miles long. There are square footage concerns, floor plans...
How Will Technology Change Healthcare In 2019?
Technology is transforming virtually every industry, and healthcare is no exception. Digital applications are becoming more readily available for patients and providers alike. Analytics and similar tools are allowing doctors to provide more accurate diagnoses and...
Industry Buzzterm: What Is A vCIO?
Managed Service Providers globally have introduced a new buzzword into their service vocabulary….Introducing, the vCIO! What is a vCIO? How Does A vCIO Benefit Your Company? Technology can be so tantalizing, especially for a small-to-midsized business. The...
Apple Tech Tip: How To Recover A File You Forgot To Save
It happens to the best of us. You’ve invested serious time and effort into a Microsoft Office file for an upcoming presentation. You may even be moments away from finishing your work. Then it happens: your Mac goes down, hard. Maybe the power goes out, or maybe you...
Building on Success: The Indispensable Role of Your Quality Construction IT Services Partner
It is not an overstatement to note that today’s successful construction companies depend on their IT systems as much as they do any hammers and nails. Successful contractors find integrating the role of a quality IT partner critical to meeting budgets and deadlines...
Selecting The Right Business VoIP Provider [2019 Guide]
To experience growth and stay relevant in their given industries, companies rely on productivity-enhancing and cost-effective communication systems that provide a robust, efficient platform for critical interactions, both internal and external. Voice over Internet...
How Advanced eDiscovery In Microsoft 365 Helps Manage Data
Do you have a lot of data? Are you able to organize your data in a convenient logical way and then search for it with ease and/or with advanced search criteria so that the results are not in the hundreds but in the tens or less? Is managing it or finding...
Can 2 or More Monitors Increase Staff Productivity?
Looking for ways to help your team accomplish more? Consider equipping their workspaces with additional monitors. Skeptics are likely shaking their heads at this, wondering, “Will that really improve productivity, or only give my employees an extra incentive to...
A Look At The 2018 Cybercrime Stats
What Is the Big Picture in Terms of Cybercrime in 2018? The past few years have revealed trends that show us cybercrime won’t just go away. The following stats put the breadth of the threat into perspective: Cybercrime was the 2nd largest crime in terms of the...
How Construction Companies Can Benefit From Managed IT Services
Construction companies have specific IT requirements. Time is money in any business, but that’s especially true in the construction industry. You need excellent communication and coordination between management and workers and the ability to oversee contractors and...
Australian MPs Concerned After Recent Cyber Attack
What happens when Australia faces a cyber attack? The Members of Parliament (MP) jump into action. They are concerned about the breach and they want answers. The MPs require that top officials come before Parliament and the Intelligence and Security Committee to...
How Compliance Manager With Microsoft Office 365 Works
Companies today operate under strict regulatory conditions. Complying with those regulations can be daunting, but failure to do so has serious implications. Managing compliance, therefore, is imperative. Microsoft offers Compliance Manager, a unique...
Facebook Finally Allows Users To Delete Sent Messages
Users of Facebook Messenger, which number over 1.2 billion people worldwide, now have a new feature that makes life a bit easier after making an “oops.” An oops is a mistake in an instant message that is immediately noticed, right after sending it, by the person who...
Feeling The Love?
There is a lot to love about the work that you do, and hopefully, your technology is part of that. Loving your IT means having a great relationship not only with the devices, software, and applications you use each day, but with the folks who look after them. ...
What Is Customer Lockbox And Privileged Access Management In Office 365
Microsoft Office 365 is a suite of services that includes Customer Lockbox and Privileged Access Management. Both tools to assist customers in meeting their compliance obligations and maximizing data security and privacy. These tools are currently only...
The Risks Of Using Auto-Complete For Passwords
The auto-fill feature that makes it easy to enter in usernames and passwords on various websites may be putting your information at risk. While auto-fill is a convenient way to keep track of the many combinations of letters, numbers and special characters you need to...
14-yr-old Teen Who Discovered Eavesdropping Bug to Be Paid by Apple
Apple is yet to disclose how much it is going to reward a 14-year-old U.S. teenager for discovering a massive security breach on its FaceTime video call system. It is believed that part of the reward money will be set aside for his high school education fund. On...
Australian Parliament Considering Changes To Encryption Laws
In early December 2018, the Australian Parliament passed into law a bill called the “Telecommunications and Other Legislation Amendment (Assistance and Access) Bill 2018.” Australian and international technology companies immediately voiced intense opposition to the...
Business Insights With Visio and Power BI
Microsoft’s Visio Visual and Power BI are two extremely useful software tools that help business owners store, organize, and interpret data with easy-to-understand visual representations. Using these tools can take your business to the next level. Still, many...
Why Local Companies Need To Hire A Local Cybersecurity Specialist
Cybersecurity threats have shown no signs of slowing down, and small and mid-sized organizations are expected to be more heavily targeted going forward. Although splashy headlines about Fortune 500 companies suffering breaches may lead some business leaders to think...
How Advanced Data Governance Helps Manage Risk & Meet Compliance
Advanced Data Governance (or ADG) is a tool from Microsoft. Available to be used within Office 365, this tool assists businesses in meeting compliance requirements and managing risk. Most of all, it helps organize the massive amounts of data that companies are now...
The Most Common Errors Local Businesses Make When Hiring an IT Consultant
Hiring an IT consultant is a proven method of boosting small to midsize businesses beyond their current capabilities. Rather than hiring full-time employees or tying up internal resources, businesses can allow an IT consultant to do some of the heavy lifting....
6 Top Tips To Why Outsourcing IT Support Makes Sense
If you own or manage a company and are considering outsourcing your IT services, you’re on your way to markedly reduced expenditures and greatly improved cybersecurity and technology. Still wondering about the benefits of outsourcing IT? Not sure how to go about...
Microsoft PowerPoint on the iPad: Sketching Your Thoughts
PowerPoint is a slideshow presentation program that is part of the Microsoft 365 office suite of tools. Now, PowerPoint makes it easy to create professional, engaging presentations right on an iPad Pro. PowerPoint for iPad is finally powerful enough so users can...
Kansas Addiction Treatment Organization’s Email Hack Leads To Data Breach
When people go to their doctors, they assume their information is protected. They freely and willingly provide personal information, like social security numbers. Their primary concern is their health and so they literally trust their lives in the hands of medical...
How To Create A Photo Calendar In Microsoft PowerPoint
What Can You Use Personalized PowerPoint Photo Calendars for? A personalized photo calendar is a great way to provide loved ones with updated family pictures during holidays and birthdays. You can print them out on regular paper or cardstock, or send your projects...
How Can I Enter and Analyze Data via a Data Entry Form in Microsoft Excel?
You can create a data entry form in Microsoft Excel without using VBA or even recording a macro. If those terms don’t mean anything to you, don’t worry. You won’t need to learn them. Excel has a hidden tool you can use to make dreaded data entry...
Ransomware Explained
Ransomware. Ransomware. You have heard the word and know it involves a cyberattack. You assume from news reports that it only happens to large companies like Target, Equifax, and Marriott Hotels for example, and that cybercriminals will not want to bother with your...
Are You Part Of The 55% That Fails To Offer Security Training To Staff Members?
Making sure the employees that rely on computer systems are trained in cybersecurity is the easiest way to avoid compromising attacks. However, only about 45 percent of business organizations actually make sure their employees are properly trained through mandatory...
How Can I Apply Styles With Microsoft Excel?
Excel’s ready-made formatting styles bring life and color to your spreadsheet. It lets you give printed versions a polished, professional look. Color coding makes it easier for audiences to interpret your data. Use this neat feature to take your worksheets up a...
Hacked: The Australian Emergency Warning System — Is Your Business Next?
In Australia, citizens fear a terrorist attack or another national emergency just as much as the next country. For this reason, Australia has what’s called the Early Warning Network or EWN for short. Recently, a hacker was able to breach this system and took it...














![Selecting The Right Business VoIP Provider [2019 Guide]](https://compnetsys.com/wp-content/uploads/2019/02/GettyImages-899355186-400x250.jpg)