Blog / Reports / Resources
Reduce Travel Costs & Expenses With Video Calling Apps
Endless airline terminals. Overpriced airport food. Overly-close seating on packed planes. What’s there to love about business travel? Sure, there are some road warriors who appreciate never having to clean a room or make a bed as they spend all their time in...
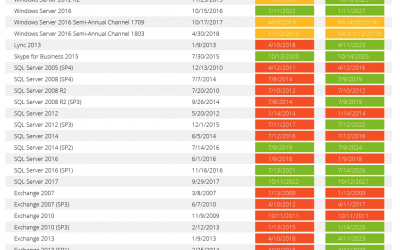
Your Guide To Microsoft’s End Of Support
In an ideal world, you’d never have any technical issues, and you’d never have to call Microsoft technical support. Everything should work perfectly, without bugs, slowdowns, crashes, or corruptions. Of course, technical issues are inevitable, and when you experience...
Review Your Calendar Monthly For Better Perspective
Life is extremely busy with people scheduling every moment of their day while still looking back and wondering where their month has gone. It’s all too easy to find yourself reviewing a 6-month plan only to find that you are seriously off-course....
Cloud Computing For Lawyers (2019 Introductory Guide)
Attorneys have unique needs for the storage of information while needing to access data on clients and cases from remote locations. That’s why cloud computing has become such a popular option for lawyers. However, the value of cloud computing needs to be...
5 Cybersecurity Tips For Employees
Imagine waking up one day only to realize that the company you work for has been hacked. Your files are missing, bank accounts are hijacked, and sensitive information is on the loose. Although this sounds like a rare situation, it has become more prevalent in this day...
Severe Ransomware Attack Hits Global Firm
Norsk Hydro just got hit with a major ransomware attack that took down their entire worldwide network. It happened this morning, Tuesday, March 19, 2019, and we wanted to share this with you. They experienced widespread system outages. This has been such a disaster...
Reduce Travel Costs & Expense With Video Calling Apps
Endless airline terminals. Overpriced airport food. Overly-close seating on packed planes. What’s there to love about business travel? Sure, there are some road warriors who appreciate never having to clean a room or make a bed as they spend all their time in...
New Threat Advisory: TrickBot (Warnings/Recommendations)
TrickBot is up to its tricks again. Once cyber experts get a handle on it, TrickBot releases new modules that advance its capabilities. Here’s what you need to know to protect your organization from TrickBot. Don’t Get Tricked By TrickBot TrickBot is up to its...
What Is A Business Continuity Plan?
Creating a business continuity plan is one of the most important things a company can do. Business continuity ensures that your business is back up and running after a critical disruption, such as a natural disaster or cyberattack. What Is Business Continuity?...
How Composing Email On Multiple Devices Keeps Business Moving
Email is one of the primary forms of communication for today’s active businessperson, but there are certainly some challenges when you’re on the go. It’s not unusual to start an email on one device and save it as a draft to finish up later from your...
Staying Safe Online: Are You the Target of a Fake Check Scam?
Great news! You’ve posted a batch of pricey items from your business on Craigslist, and someone has offered to purchase the lot. However, when you receive the check you realize it’s not for precisely the right amount. Perhaps you contact the seller to get...
Healthcare Fines For Breaches Are Increasing
Healthcare was a lucrative target for hackers in 2018. Cybercriminals are getting more creative despite better awareness among healthcare organizations. And fines for breaches of patient information are increasing. What more can you do to ensure your patient data is...
Windows Server 2008 End of Support (Questions and Answers)
Unfortunately, all good things must come to an end — and on January 14, 2020, Microsoft will be stopping mainstream service for their highly popular Windows 2008 Server. If you are one of the millions of organizations who are still using this secure and highly...
Top Advantages To Local Small Business When They Outsource IT Services
Small business growth is a challenge of keeping up with success without crumbling under commercial weight. Many improvements needed to reach the next stage of success can be prohibitively expensive, leading to debt and risky gambles that could fail from random chance...
Happy St. Patrick’s Day This Sunday
March 17th is one of our favorite days of the year – St. Patrick’s Day. For some, it’s a day to celebrate centuries of rich culture and Irish heritage, and for others, an opportunity to have a pint or two with friends. However you’ll be spending this St....
What Are The Benefits Of Managed Services To Local Companies
Depending on their scope and impact on your workday, tech issues can take hours to resolve, if not days. In some cases, you may spend far too much time tracking down a problem, only to come up empty-handed in the end. In others, such as security breaches, you may not...
Report: Financial Firms See Alarming 480% Increase In Data Breaches
Financial service firms: beware. Your data is a target. A new report out of the United Kingdom (UK) cannot underscore enough the severity of the issue. But it is nothing new. The FBI has put the alarms on since 2011, from threats of account takeovers to third-party...
Top New Additions To Microsoft Office 365
Microsoft Office 365 has rolled out an impressive array of new features that business owners will appreciate. These range from handy mobile-to-PC interactions to intuitive, behind-the-scenes IT integrations to keep a business running smoothly. Here are some of the...
Georgia County Pays $400,000 Ransom
Not even Georgia county governments are safe from ransomware attacks. Jackson County just paid a $400,000 ransom after hackers used a ransomware attack to deactivate their computer systems. It’s still not known how the hackers managed to breach their county IT...
How To Create Information Gathering Forms With Microsoft Office 365
It may surprise you, but Microsoft Office 365 has a fantastic solution for creating simple quizzes, polls and surveys — and you already have access to this functionality! Microsoft Forms is relatively new, as it was only launched in June 2016, but this...
Is Having a vCIO Essential?
Are your company processes aligned with the technology you have? Have you purchased different software for different things when one software could have been used for multiple things? Do you feel there are technological gaps or challenges not being appropriately...
How Much Time Are You Losing To Technology Issues?
No matter how good technology gets, technical issues are still and will continue to be a major cause of lost productivity for individuals and companies. Problems with slow or crashed computers, loss of internet service, printers not working, dropped telephone calls,...
What Can Businesses Learn From The First GDPR Fines?
Less than a year ago, the European Union instituted the General Data Protection Regulation (GDPR) to protect customer rights to data privacy. The regulation created quite a stir in May 2018 when it was enacted, and has recently created even more of a stir because the...
Are Hackers Targeting Managed Service Providers?
When you think about it, it makes sense that hackers might target managed services providers (MSPs) — those organizations that are responsible for protecting the data and technology systems for hundreds or even thousands of other organizations. The...
Warning: Foreign Hackers Compromised Citrix Systems
Citrix said the FBI warned them on Wednesday, March 6th that hackers compromised its IT systems and stole “business documents.” Citrix doesn’t know precisely which documents the hackers obtained nor how they got in. It’s suspected that this is a...
How To Limit What Others See From Your Browsing History
If you’re like most people, you’ve got valid concerns about your personal privacy while browsing the internet. After all, Facebook and other organizations with a huge online presence have recently been caught dropping the ball regarding protecting the...
What Is This Chromium Application That Just Appeared On My Computer?
Have you seen a new application — Chromium — suddenly appear on your computer? It’s likely that if you did not intentionally download it, the app is malware that should be removed immediately. While Chromium is a legitimate product, hackers have been...
Never Lose A Receipt Ever Again
Tired of Not Getting Reimbursed for Business Expenses? Never Lose Your Receipts Ever Again! Maintaining receipts is a fact of life for many people, but it can be extremely frustrating. Tiny pieces of paper that have to be maintained and categorized long enough...
When Does Moving Away From The Cloud Make Sense?
In 2018, Dropbox announced it was shifting away from cloud-based services in favor of managing some of its data storage and application hosting itself. The company noted that while Amazon Web Services (AWS) initially allowed Dropbox to delay the purchase and...
Learn the Power of Google Reviews for Lawyers & Law Firms
There’s no better means of promoting a professional business today than the use of online reviews. Positive third-party online reviews can take your law firm to the next level. Personal referrals and word of mouth have their place in drumming up new business, but they...
Time To Set The Clocks Back
Daylight Saving Time for 2019 starts on Sunday, March 10th. I’m sure you know how Daylight Saving Time (DST) works, but did you know not everyone in the US observes this time change? Arizona hasn’t observed DST since 1967, and Hawaii has never used DST. Michigan...
Spring Forward This Sunday
Daylight Saving Time for 2019 starts on Sunday, March 10th. I’m sure you know how Daylight Saving Time (DST) works, but did you know not everyone in Canada observes this time change? Parts of British Columbia and Nunavut don’t observe DST, while a small part of...
Toyota Australia Hit With Data Breach
In late February 2019, Toyota Australia was hit by a major cyber attack that knocked out its online presence and email systems. For days, the automaker had its ability to connect with customers significantly compromised. The Toyota incident is yet the latest reminder...
What Is BlockChain?
Business executives, business owners, C level executives, and business managers share Blockchain information. One of the outstanding leaders of IT service companies across the globe is known as Infiniwiz. Our IT service strives to educate and train professionals in...
What are the Top Benefits Of IT Services To Local Small Business?
Why Do Local Small Businesses Need IT Services? Many small business owners are entrepreneurial and want to do as much as possible on their own. However, specific tasks require technical expertise that would distract owners from operating their businesses. IT support...
4 Questions Every CEO Needs To Ask About Cybersecurity
With the ever-increasing rate of digital interconnectedness and accessibility, IT systems are more at risk of attack by hackers and spies than ever before. Yet, many companies still haven’t seriously addressed the issue of cybersecurity in their organizations. If you...
Importance of Managed IT Services in Improving Your Business Operations
The sudden development of IT problems can quickly throw your team’s workday off track. Even simple login issues can prevent you and your employees from getting any work done until you can fix the problem. To do so on your own, you may have to spend hours...
Inside The Anatomy Of The Human Firewall
Each year, around 61% of small businesses become the victims of a malware attack. While many small businesses may think no one would ever come after them because of their size, know that over half of the total global attacks hit small businesses and, for thieves,...
The Ultimate Small Business Owner’s Guide to Ransomware
Your employee innocently clicks a link within an email or visits a sketchy website and the next thing you know your digital assets are being held hostage by a cyber attacker. It only takes a few keystrokes to cause potentially irrevocable damage to your systems, and...
Why You Need A Plan For Sharing Critical Passwords
Many companies password protect their files and applications and for good reason. There are hackers trying every day to break into a system and obtain files and information. Most businesses are smart about applying passwords to protect their information. However, many...