Blog / Reports / Resources
Are You Using Internet Explorer?
Do you still surf the Web with Internet Explorer? If so, you’re not alone. Even after Microsoft came out with their new Edge browser in 2015, some people are still using Internet Explorer. The Problem? Security experts have found serious security flaws in...
Have You Heard of DuckDuckGo?
The self-proclaimed “search engine that doesn’t track you,” DuckDuckGo is likely the most successful search engine available when it comes to privacy and security. While Google remains the most popular search engine by far, many users are concerned about its practice...
Should CMOs and CIOs Partner On Strategic Information Technology?
For as long as the roles of CMO and CIO have existed, their work has rarely overlapped. CMOs focused on the company’s marketing efforts while CIOs stuck to the technology side of the business. But in today’s digital world, the hard lines that once separated marketing...
What Is Google G Suite and What Are the Benefits for My Business?
There are certain functions that every business requires — word processing, analysis, presentations and calendaring — and Microsoft Office used to be the default option for businesses of all sizes. Over the past few years, Google’s G Suite has become...
Canada Taking Facebook to Court
On Thursday, April 25, 2019, notable news broke that Canada is taking Facebook to court. Daniel Therrien, Canada’s federal privacy commissioner, gave a joint news conference with Michael McEvoy, the information and privacy commissioner for British Columbia. In this...
Four Amazing Tips on Using iPhones and iPads in Your Business
Coordinating interactions between office staff and remote workers can be challenging. One way you can cut through a lot of the confusion that arises when trying to keep everything in sync is by leveraging your worker’s iPad and iPhone devices. It is a way of using...
Can You Legally and Ethically Monitor Your Employee’s Online Activities?
Monitoring employee behavior is nothing new, as supervisors have been stalking their staff for generations. What has changed is the degree to which employee behavior is transparent in the workplace, with sophisticated monitoring solutions in play one could argue that...
How AI Is Saving Orthopedic and Sports Medicine Practices An Hour Each Day
The red tape that normally surrounds the administration of patients in the healthcare industry is a leading cause of physician burnout, as many data experts have noted. Healthcare providers are responsible for a growing volume of paperwork and other off-patient work,...
Managing Your iPhone and iPad Business Notifications (User Guide)
All notifications are not created equally, especially when it comes to business hours. That becomes apparent when sifting through multiple items on your iPhone or iPad. You want the alert from a peer letting you know about the receipt of a critical signed...
UEFI Rootkits & Ugly Heads
Whether you are a cybersecurity expert or not, there are some security risks that every business leader needs to be aware of—and UEFI rootkits definitely fall into that category. These nasty computer viruses are uniquely dangerous to your computer systems because they...
The CFOs Guide To Evaluating Information Technology
Evaluating information technology can be a challenging aspect of the CFO role. Your organization is likely inundated with requests for new IT features, and understanding the true value of many of them requires technical knowledge you may not have. The spending...
Ransomware Hits Popular Cable TV Network
For several years now, sporadic attacks that interrupt major networks’ daily programming have been occurring around the world as hackers try to break in and succeed at their digital violence. In April 2019, the victim was The Weather Channel. The network found...
Hiring Tech: 2019 CEOs Tech Hiring Guide
As your business operations evolve and expand, you’ll likely reach a critical point in your company’s growth where the tasks required will outnumber the staff you have available. Deciding to outsource work might be a difficult decision, partly because of...
New Way To Communicate
The Power to Conference & Collaborate Better Can Be Yours Microsoft has just announced the June 2019 release of its Surface Hub 2, a tool for conferencing and collaboration among teams. This is the Surface Hub’s successor, and it boasts improvements to the...
Hackers Steal Company Information
Cybercriminals have started 2019 off by stealing more than 1.7 billion records. They look for data that is profitable in some way, whether they sell it directly or use it as part of another attack. A successful intrusion attempt comes from various factors, such as an...
Microsoft Accounts Targeted For Months, Hackers Serve A Security Reminder
Microsoft began notifying Outlook.com users of a 2019 security breach that occurred between January 1st and March 28th. Hackers were unintentionally given unauthorized access to some accounts, where they were then able to view subject lines, email addresses, and...
Essential List of Cybersecurity Terms to Know in 2019
As the digital community continues to expand to include more individuals and more devices, enforcing cybersecurity becomes more complicated. The number of opportunities and vulnerabilities for hackers to leverage is continuously growing; it is imperative for...
Foreign Hacker Steals Nearly Half a Million From City of Tallahassee
The Tallahassee Democrat reported on April 5th that a large sum of money had been stolen from the city of Tallahassee’s employee payroll. The perpetrator is suspected to be a foreign hacker. What was stolen in the hack? The breech diverted approximately $498,000 from...
Can Outsourcing Help Your Business Grow?
If the thought of letting go of crucial parts of your business gives you the hives, it’s time to get real about outsourcing. It’s practically impossible for one individual or even a small group of people to adequately perform every function of a business....
What Role Do Robots Play In Healthcare?
Artificial intelligence and robotics are poised to change the entire economic landscape over the coming decades, with an estimated 30% of existing jobs poised to be taken over by robots by 2030. Nowhere is this more evident than in healthcare. Many healthcare tasks...
Happy Administrative Professionals Day!
April 24th is Administrative Professionals Day, which is an occasion worth celebrating. No office can function without hardworking and dedicated administrative staff, so why not take this as an opportunity to remind them how much you value them? Treat...
Inside The New Microsoft Edge Browser
Microsoft’s first version of the Edge browser fell far behind other options, gaining only a 4.4 percent market share compared to Chrome’s 65.5 percent, Internet Explorer’s 9.83 percent, and Firefox’s 9.62 percent. The company went back to the...
Is Healthcare Ready For Digital Communications?
The healthcare industry is currently facing a crisis. Hounded by criticism of insufficient access to providers and poor bedside manner, skepticism abounds on the part of patients and their families. But with administrative tasks and paperwork at an all-time high, how...
CFO Tech Blog: How To Become The Tech Savvy CFO
More than ever, today’s CFOs are expected to have a degree of tech savviness. Big data and analytics are tools that are just too powerful to ignore in the CFO suite. If you’re not particularly tech savvy, harnessing the power of these tools to the fullest extent will...
Celebrate Earth Day This April 22nd!
This year, what will you do to celebrate Earth Day? The 49th Annual Earth Day is nearly upon us. As always, it’s April 22nd and the perfect day to celebrate this beautiful blue planet we live on. Let’s learn more about what Earth Day is, where it comes...
Should We Go With A Private Cloud Or Public Cloud?
Business objectives should help determine how technology will be used. The growth planning helps as technology experts determine the plans for support services. Several companies of many sizes are continuing their research of private and public clouds. The question...
What Is The Dark Web?
According to some in the technology industry, criminals use the dark web to buy and sell stolen data. Identity thieves are a must stop with any Internet offerings. The top priority with all of this is forced compliance for Internet data protection, consumer...
Tech Education: What Is Microsoft Office 365?
The ability to work anywhere used to be limited to freelancers and writers, but today’s professionals need the flexibility to be productive regardless of their physical location. Microsoft Office 365 provides the full-featured suite of services that...
Australian Tax Office Issues Tax Refund Scam Warning
As tax season rolls around, another tax scam has reared its ugly head, this time in Australia. This particular scam is fooling so many people that the Australian government’s Taxation Office has issued an urgent warning about it to the citizens of the country....
Is Virtual Reality For Real In Healthcare?
Over the last couple of years, both the concept and the real world application of Virtual Reality (VR) has moved from the fringes of our imagination, into everyday use. What was once a technology that was considered as only beneficial in computer games and futuristic...
Microsoft Data Breach Highlights Need for MSP Collaboration and Security
A recently announced hack data security breach of Microsoft’s Outlook.com product has many wondering how to work with MSP customers to understand the scope and impact. Ulistic recently spoke with several MSP security experts to understand more about the breach...
Be Aware: ASUS Update Tool Hijacked By Aggressive Hackers
Large software and hardware manufacturers are generally a trusted source for updates, but that same level of trust with consumers is what makes these groups a heavy target for hackers. The recent infiltration of ASUS made it all too clear that no one is safe from the...
How To Encrypt an Email In Microsoft Outlook
There is any number of reasons to encrypt an email in Microsoft Office Outlook, anything from details about your salary to negotiations to purchase a business. With the state of cybersecurity, you need to know that you are protected from individuals who may attempt to...
Tech Education: What Is A PBX Phone System?
The image of a traditional PBX phone system may make you uncomfortable because systems in the past were either tied into a particular type of hardware or an individual vendor. While that may make you want to shy away from the enhanced functionality that you receive...
Tech Education: What Is A Firewall?
Firewalls were developed over thirty years ago and function as the first line of defense for many business networks. This piece of network equipment is a perimeter defense that determines whether packets can move into or out of the network. While the basic concept of...
What Are the Benefits of Outsourcing IT Services For Small Business?
There is a point in every small business’s lifecycle when technology becomes integral to the business. With some organizations, this could be the first day they are in existence — with others, it may be several months to a year or more before technical...
Should Law Firms Start Their Own Podcasts?
Podcasts are huge these days. Popular podcast Serial has been downloaded millions of times and has become a pop culture phenomenon right alongside other “did they really do it” series like Netflix’s Making a Murderer. Podcasts are also used for informational and...
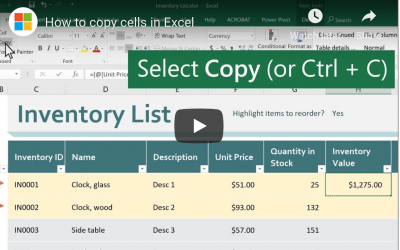
Microsoft Excel Tip: How To Copy Cells In Microsoft Excel
Microsoft Excel is a staple program in Microsoft’s Office suite. It’s a powerful spreadsheet program that allows users to organize data and calculate results using a wide range of formulas. Let’s look at one basic element to this program: how to copy cells in...
A Whopping 94% Of Businesses Don’t Leverage The Software They Purchase
Businesses spend a significant amount on their software solutions, but 94 percent of them don’t get the expected value out of them. Many roadblocks stand in the way of bringing new solutions into the office, from a lack of consideration for the end user to...
Are Healthcare Providers Slow To Embrace Digital Technologies?
Medical appointments and doctors’ visits are not enough. Patients want more contact with their healthcare providers, without necessarily needing to schedule more appointments and spend more time in the waiting room. 74% of patients polled in a recent West survey...