
by Felicien | Jul 22, 2019 | Education
As the business world continues to evolve, digital transformation becomes even more important for every company, regardless of the industry. However, successfully moving into the digital arena and remaining on top requires companies to make the right choices when it comes to their money and their time.
Below are some tips to help your company achieve ongoing digital success.
1. Create a designated budget for digital projects.
In order to become a digital success, monetary investment is always required. Carve out a section of your budget that will be dedicated to digital projects only. In general, your digital expenses should represent at least five percent of your annual expenses. However, depending on your situation, you may decide to scale this amount up or down.
2. Involve your employees.
Investing money in digital projects alone is not enough to guarantee your success. You must also involve your employees in these endeavors. Every employee on your staff should be aware of your goals with regard to digital projects, and some of your employees should be working exclusively in roles related to digital.
3. Stay on top of emerging technologies.
The digital world is always changing, with new technologies on the horizon every day. To be successful digitally, your company needs to be aware of the new technologies as they emerge so you can incorporate them into your operations when appropriate.
4. Consider digital when looking for new talent.
Bringing your current employees onboard with your digital projects can be helpful, but it isn’t enough to ensure lasting success in this arena. As digital continues to become more widespread, hiring employees who are comfortable with technology becomes even more important for every company. When looking for new talent to add to your team, make digital skills a priority.
5. Make use of data.
To improve customer experiences digitally, your company needs to invest in and utilize data. Data allows you to customize every customer’s interactions with your company so he or she can have the highest level of satisfaction possible. Data also allows you to gain valuable insights about every aspect of your business’ operations so you can identify strengths and weaknesses.
6. Seek professional assistance.
Bringing digital to your company successfully can be a challenge, especially if you aren’t an expert in this field and/or if you have many other responsibilities. If you aren’t sure how to incorporate digital into your daily operations, consider hiring a consultant or even a full-time digital team to help you make the most of your investments and your efforts.
These are just a few of the strategies you can use to make your company a digital success. Keep in mind that success rarely comes overnight, so ongoing effort will likely be required before you will see the results you desire.
by Felicien | Jul 22, 2019 | Education
Apple’s mobile iOS operation system is one of the most popular platforms in the world. With more than 1.3 billion devices running iOS worldwide, Apple has clearly done an excellent job of providing a world-class experience for its users.
Watch the video below or click here to watch on YouTube.
One area of the operating system that has undergone significant development in recent updates is in notification management. With more apps — and corresponding notifications — than ever before, it is important for mobile operating systems like iOS to provide ways for users to manage these notifications in a simple and streamlined way.
Here are some of the ways Apple is helping users manage their notifications in iOS 12:
Notification Grouping
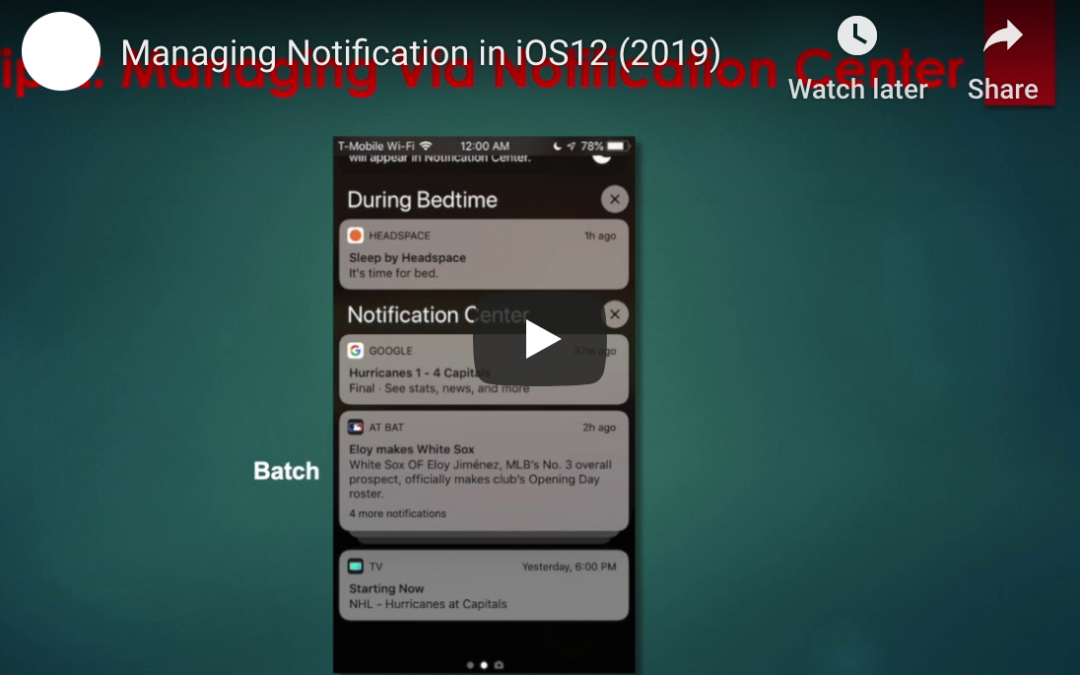
One great innovation in iOS 12 is the ability to have notifications from individual apps “grouped”. This means that, instead of having a long list of every notification from an app, you will see the most recent notification for each app, with previous unanswered notifications stacked behind them. This makes it easier to see notifications from multiple apps, without the notifications from one app taking up all the space on your screen.
Grouped notifications can be expanded by tapping on the top notification, so you’ll still have access to all notifications when you’re ready to view them.
Deliver Quietly
Another new feature is the ability to have notifications delivered “quietly”. The “Deliver Quietly” function can be activated from the notification screen. When this setting is turned on, notifications will not cause a vibration or notification tone, but will still be visible when looking directly at your device. In essence, “Deliver Quietly” is very similar to the “Do Not Disturb” function — except that it can be app-specific.
App-specific notification settings
In addition to the “Deliver Quietly” feature, iOS 12 also gives users the ability to change other notification settings for individual apps. In addition to the ability to “Deliver Quietly” and turn notifications off completely, users can choose where notifications appear (notification screen, lock screen, banner at the top of the screen). In addition, individual apps can have sounds and badges turned on or off. Even notification grouping can be turned on or off for individual apps.
For the privacy-conscious, iOS 12 also gives users the ability to turn notification previews on or off for individual apps. This means you can still keep non-sensitive apps showing previews while protecting potentially sensitive data by turning off notification previews.
Quick notification setting changes
Perhaps the most convenient notification feature in iOS is the ability to quickly make app-specific notification changes. Instead of going through multiple menus in the “Settings” app, users can simply click on the ellipsis (three dots) that show up in the top-right of notifications. From here, users can make all the changes discussed in this article.
While there are more notifications than ever before, Apple is making them more manageable in iOS 12.

by Felicien | Jul 21, 2019 | Education
Microsoft Defender ATP Security for Macs
Microsoft Defender ATP (Advanced Threat Protection) is a program that detects ongoing attacks on corporate networks, blocks any that are malicious, and then provides response recommendations to improve security. Microsoft has made good on a pledge made in March 2019 by announcing that its sophisticated endpoint security service is available for Mac users.
Microsoft Defender ATP for Mac has been moved to what the company calls “general availability” as of June 28 according to Helen Allas, the principal program manager for the enterprise security team. In a July 8 post to a company blog, Allas reported that “with Microsoft Defender ATP for Mac general availability, all Microsoft Defender ATP customers now have an opportunity to start benefiting from integrated experiences across their Windows and macOS clients in Microsoft Defender Security Center.” The core components of Microsoft Defender ATP, which includes the latest “Threat & Vulnerability Management,” serve Macs as well as PCs.
The Microsoft Defender ATP for Mac supports the three latest released versions of macOS: Mojave, High Sierra, and Sierra. Customers can use Microsoft Intune and Jamf to deploy and manage Microsoft Defender ATP for Mac. Just like with Microsoft Office applications on macOS, Microsoft Auto Update is used to manage Microsoft Defender ATP for Mac updates.
There’s still more implementation to come
With this announcement came the news that this update doesn’t allow for complete integration of Microsoft Defender ATP for Macs quite yet. There are also some quirks that haven’t been ironed out for Mac users. In the “Known Issues” section of the online documentation, Microsoft has written “full Microsoft Defender ATP integration is not available yet.” And there is no date listed for when the entire program will be available for integration for Mac users.
Defense against malicious attacks
Microsoft Defender ATP is a very useful tool as it detects ongoing cyberattacks on corporate networks, blocks whatever it recognises as malicious, and then follows up to investigate and discover information about the attack and/or security breach, after which it provides response recommendations and cyberattack remediation.
How to add Microsoft Defender ATP
This defense service is a component within the highest-level Windows ten licenses, including those provided by a subscription service such as Windows 10 Enterprise E5 or Microsoft 365 E5. In fact, Microsoft claims that ATP is the differentiator between these high-level services and lower-tier bundles. You can also add ATP as an add-on service to Microsoft 365 E3 for an extra $12 per month.
If you want to add Macs to the Windows PCs already reporting and covered by Microsoft Defender ATP, users are required to license Microsoft 365 E5, Windows 10 Enterprise E5 or Windows 10 Education E5 (Microsoft 365 E5 includes Windows 10 Enterprise E5). Any Macs using Defender ATP are required to be running one of three of the newest edictions of macOS – 2018 Mojave, 2017 High Sierra, or 2016 Sierra. Once September’s release of 2019 Catalina, it’s likely that Microsoft will drop the oldest, 2016 Sierra, because Apple will no longer support that OS with regular security updates.
You can find instructions from Microsoft published on how to deploy Microsoft Defender ATP to Macs. On those instructions, users are warned that they will need “beginner-level experience in macOS and BASH scripting” as well as admin privileges to the device or devices in case there are issues and you need to use a fallback of manual deployment to install. Admins can deploy the security service to Macs using any of these platforms: Microsooft Intune, JAMF, or other MDM (mobile device management) platforms.
Instructions on how to configure Defender ATP for Mac are posted here.
Customers can register for a free trial of Defender ATP online.
by Felicien | Jul 19, 2019 | Education
Intel Humiliated by Losing CPU Market Share to Eager AMD
Intel’s continued problems with delivering CPUs are expected to go on throughout the fall and potentially 2020. Intel’s CEO Bob Swan told shareholders during their second-quarter conference call that the delays in processor deliveries would continue until September.
The fallout benefits AMD, which increased its market share from 9.8 percent in 2018 to 18 percent by the end of June 2019.
Why is Intel having trouble shipping CPUs on time?
The culprit is Ice Lake, Intel’s high volume 10nm processor. The chipmaker announced Ice Lake at CES 2019, but the processor hasn’t been forthcoming in the volumes Intel promised. The 10nm project has slowed Intel’s other chip line production. Lower-end processors have especially suffered, leading to supply chain problems for manufacturers, retailers, and customers.
What are Intel’s problems with the 10nm CPU?
The current problems continue Intel’s struggles with 10nm chips which date back to 2013. Intel’s initial goal for 10nm CPUs was 2015. Year by year, Intel has pushed back the deadline for 10nm CPUs. Intel’s second-quarter conference call gave late 2019 as the deadline — but the real date is more likely to be 2020 for most people who want to buy PCs with the new CPU.
The bottom-line culprit is engineering choices. Intel’s 10nm design selections have consistently held mass production back on its 10nm CPU project. As problems continued, Intel responded by refining its 14nm CPU performance and production process. TSMC and Samsung have 10nm CPUs, but their performance is equivalent to Intel’s 14nm CPUs.
What is so good about increasingly tiny CPUs?
Intel and its competitors, including AMD, are continuing R & D on smaller and smaller gate-size processors. Smaller gate sizes allow more CPU cores, or they enable a smaller die for the same performance as a larger CPU.
Smaller CPUs also use less power and generate less heat, a must for mobile devices and laptops. With desktop PCs, heat and power consumption aren’t as important, so processor performance can be improved in other ways.
How have Intel’s supply problems affected its business?
Intel’s stock has increased 6% since January 2019 according to Fortune, but rival AMD’s stock has gone up 83%. Nvidia’s stock has risen 25% since January.
The supply problems are mirrored by leadership problems at “Chipzilla.” Intel’s former CEO Brian Krzanich resigned in June 2018 when a relationship with a former employee was disclosed. Krzanich’s replacement Bob Swan is credited with improving company morale and redirecting the floundering 10nm CPU team.
Has AMD taken advantage of Intel’s delays?
AMD is gaining market share with scaled-up production of 12nm circuits. The Santa Clara-based chipmaker is gaining market share from Intel with its Ryzen 14nm and 12nm CPUs. It has announced 7nm Ryzen and Rome CPUs. AMD’s year-to-year market share in desktop computers grew from 12.2% in the first quarter of 2018 to 17.1% by the first quarter of 2019. In notebooks, AMD’s share grew from 8% to 13.1 %.
AMD also expects the number of Ryzen CPU notebooks to grow significantly in 2019, with desktop units growing by 30% and notebooks by 50%. Lenovo, the world’s #2 PC manufacturer, will be using Ryzen 7 Pro 3700U chips in its upcoming ThinkPads.
Which Intel and AMD news should industry pros and investors watch in upcoming quarters?
Intel has delayed shipments of all of its CPUs, not just the promised 10nm Ice Lake and variant chips. Rivals AMD and Nvidia have taken advantage of ongoing delays to ink new deals with major companies including Lenovo.
Investors and industry pros should keep an eye on CPU market shares for the rest of 2019 and into 2020. This will indicate if the agile upstarts are going to continue to take on “Chipzilla” and change the landscape of computing power in 2020 and beyond.

by Felicien | Jul 19, 2019 | Education
We’re only halfway into 2019, yet data protection specialists and IT analysts have already seen an unfortunate spike in criminal activity across industries.
Thus far, here are the biggest cybersecurity crises of the year.
2019’s Top Cybersecurity Stories
#1 – Supply chain attacks
Unique to 2019 is a growing trend of supply chain attacks.
Supply chain attacks are also called third-party attacks. That’s because they are attacks that don’t directly target you and your company, but that still affect you. This occurs by a hacker targeting a third party that your company works with, thus, in the end, indirectly affecting your company.
For example, if your company contracts with another company to provide your stores with POC (point of sale) units, the company providing your POCs could be hacked in a way that ends up affecting your company.
This trend began in 2017 with NotPetya, a piece of malware that spread when Russian cybercriminals hacked how auto-updates were implemented within an accounting application based in the Ukraine. Since, similar attacks have hit several companies, from Asus and CCleaner (a computer cleanup program), to Visual Studio (an application from Microsoft).
#2 – Breach of the American Medical Collection Agency
The American Medical Collection Agency was hacked over a long period of time from August 2018 through March 2019. During this time, it is estimated that 20 million patients had their data stolen.
Information that was compromised included complete names and dates of birth, addresses and phone numbers, balances due for medical expenses, healthcare provider information, and dates of medical services rendered. Although Social Security numbers and insurance ID numbers were not known to be compromised in the attack, the fact that personal information was lost from so many customers is truly troubling.
#3 – Attacks from Iranian hackers
Iran has certainly been in the news recently for reasons other than cyberattacks. When Trump pulled the United States out of the Iranian nuclear agreement, escalations between the two countries escalated quickly. Although many citizens may not realize it, these attacks are happening both in the physical world and the cyber world.
Trump recently aborted a military strike to Iran after Iran attempted to shoot down a U.S. drone. However, he did approve a cyberattack against the control launch systems of Iran’s missile and rocket program. Since, Iran has fought back in a similar manner and perpetuated the cyber quarrel.
#4 – Breach of a U.S. Customs and Border Protection Surveillance Contractor
After the breach of a surveillance contractor for the U.S. Customs and Border Protection, hackers were able to obtain license plate information and traveler photos for approximately 100,000 people.
Many travelers going across U.S. borders in May were routinely photographed by Perceptics, a Tennessee-based surveillance contractor. Unknown hackers stole this information and later posted it on the dark web.
#5 – First American’s Data Exposure
First American is a title insurance and real estate firm that had personal and financial data from 885 million customers exposed for anyone who wanted a look-see.
This was not a security breach or a hack, but an internal error — and a terrible one at that. Anyone who visited the First American website during the exposure could have stolen detailed financial and personal information from the hundreds of millions of customers that First American had data on. It would have only taken some simple navigation around the site. Information that was available included Social Security numbers, mortgage documents, tax documents, bank account numbers, driver’s license images, and more.
Still, it is not known whether anything was indeed compromised or stolen.
#6 – Ransomware attacks on local governments
Ransomware attacks have long been a problem in the cybersphere. But recently, they’ve been taken to a whole new level.
Instead of targeting individuals or attempting to target huge enterprises, hackers specializing in ransomware are now aiming their attention at local governments and municipalities, such as the city of Baltimore in Maryland, three cities in Florida, Atlanta in Georgia, and many others around the nation.
Ransomware is a type of malicious software or malware that locks down data and/or computer systems from the owners. Once this occurs, the hackers who installed the malware demand a monetary sum (usually in bitcoin) in order for the owners to regain system and data access.
Often, cybersecurity specialists are unable to locate the perpetrators or unlock the ransomed systems or data. In these situations, many target cities have reluctantly decided to pay the ransom. In Riviera Beach, Florida, for example, the city voted to pay a whopping $500,000 in ransom in order to regain access to their computer systems.




