by Felicien | Aug 22, 2018 | Education
Step-by-Step Instructions on How to Add your Email Signature in Outlook, Outlook.com, and Gmail
Creating a signature that will leave a lasting impression at the end of an email is essential in today’s business world. However, users often struggle to know which font to use, how to make it stand out, but not make it too flashy, and so on.
If your company doesn’t specify a detailed way to create a signature, you may end up searching for professional email signature examples every time you change jobs, get a promotion, or feel the need to improve your current signature.
Let’s take a look at how to add a signature to the two most popular email platforms used today: Outlook and Gmail. We will also identify shortcuts and tips to make your experience using these email platforms easier and more effective.
Outlook
Frequently Used Keyboard Shortcuts
Knowing keyboard shortcuts can speed up the process of sending emails, formatting documents, and searching through the toolbar. Let’s look at some great shortcuts for Outlook.
Go to Home tab: Alt+H
New message: Ctrl+Shift+M
Send: Alt+S
Insert file: Alt+N, A, F
New task: Ctrl+Shift+K
Search: Ctrl+E Alt+H, R, P
Reply: Alt+H, R, P
Forward: Alt+H, F, W
Reply All: Alt+H, R, A
Copy: Ctrl+C or Ctrl+Insert
Send/Receive: Alt+S, S
Go to the calendar: Ctrl+2
Create appointment: Ctrl+Shift+A
Move to folder: Alt+H, M, V, select folder from list
Attachment SaveAs: Alt+JA, A, S
Navigating Through Outlook Using Shortcuts
Outlook has great shortcuts that can quickly allow you to hop around from email to calendar, and so on. Let’s look at these shortcuts.
Switch to Mail view: Ctrl+1
Switch to Calendar view: Ctrl+2
Switch to Contacts view: Ctrl+3
Switch to Tasks view: Ctrl+4
Switch to Notes: Ctrl+5
Switch to Folder list in the Folder pane: Ctrl+6
Switch to Shortcuts: Ctrl+7
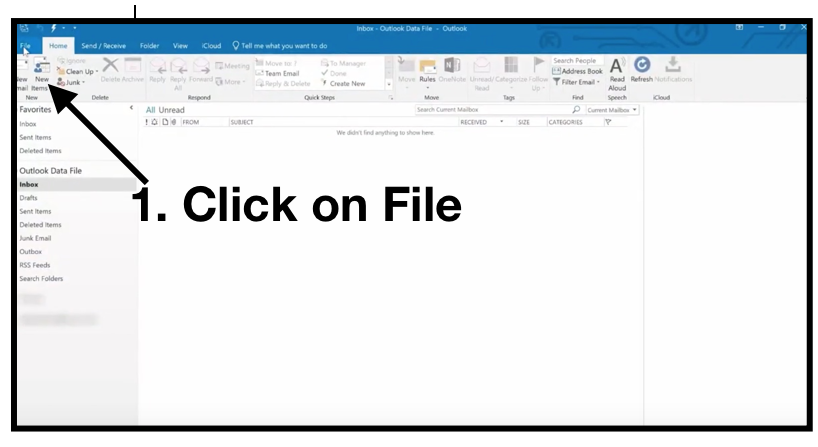
Adding an Email Signature to the Desktop Version of Outlook
Step One: To begin, open up your Outlook email client and click on File.
Step Two: In the file window, click on Options.
Step Three: When the Options window pops up, click on Mail.
Step Four: In the Mail section, scroll down to Signatures.
Step Five: When the Signature window opens, Click on New.
Step Six: In the Signature window, type in your signature and add a company logo if you desire.
Once you have completed this process, you can select New Email to see the signature you’ve created.
Adding an Email Signature to Outlook.com
If you are using Outlook.com instead of the desktop version of Outlook, adding a signature is a little different. Let’s look at how to add a signature to Outlook.com.
Step One: In your Outlook.com email, click the gear symbol in the top right corner.
Step Two: In the dropdown, scroll down to options, and click on it.
Step Three: In the Options window, scroll down to mail, and click on Signatures.
Step Four: When the Signature window appears, add your customized signature.
Step Five: After adding your signature, click the Save button.
Once you have completed this process, you can select New Email to see the signature you created.
Gmail
Frequently Used Keyboard Shortcuts
As with Outlook, knowing keyboard shortcuts in Gmail can quicken your tasks of sending emails. However, with Gmail, you first need to turn the keyboard shortcuts on.
Turning on Keyboard Shortcuts in Gmail
First: In your Gmail window, click the gear symbol in the top right corner.
Second: Click on Settings.
Third: Scroll down to the “Keyboard Shortcuts” section.
Fourth: Select Keyboard Shortcuts On.
Last: At the bottom of the page, click Save Changes.
Gmail Shortcuts
Once you have your keyboard shortcuts turned on, here are some great shortcuts in Gmail:
Open keyboard shortcut help: Shift + ?
Select a series of messages: Shift
Select all unread messages: Shift + 8 + u
Archive selected messages: e
Mark selected messages as important: =
Compose Email: c
Undo last action: z
Search for messages: /
Go to tasks: g + k
Add a conversation to tasks: Shift + t
Reply: r
Reply all: a
Forward: f
Mark current messages unread: Shift + u
Mark selected message as important: =
Archive selected message: e
Jump to newer email: k
Jump to previous email: j
Jump to next message in email thread: n
Jump to the previous message in email thread: p
Jump back to inbox view: u
Insert link: Command + k
Insert numbered list: Command + Shift + 7
Insert bullet points: Command + Shift + 8
Bold/Italicize/Underline: Command + b/Command + l/Command + u
Remove formatting: Command + Control +
Send Email: Command + Enter
Adding an Email Signature to Gmail
Step One: After you have signed in to your Gmail account, click the gear symbol in the top right corner.
Step Two: In the drop down, click on Settings.
Step Three: In Settings, scroll down to the Signature window, and add your Signature.
Step Four: At the bottom of the page, click Save Changes.
Wrap Up
There you have it! Easy ways to add a custom signature to today’s most popular email platforms. Plus, as a bonus, all the shortcut keys you need to make sure you’re saving time and being productive each day.

by Felicien | Aug 21, 2018 | Education
Ushering in the Modern Workplace with Microsoft 365
Do you think your team has the liberty to do their best work? Are they engaged and satisfied on a day-to-day basis? Are you providing your team with the tools that enable them to have a digital, adjustable workplace in today’s modern age?
Every business leader wants to be able to provide a work environment in which their team can enjoy secure and reliable platforms. This type of collaboration encourages the exchange of ideas, creative thought, and better workflows. The bottom line is that when you give your teams the tools and resources they need to do their jobs correctly, the whole business just runs better.
That’s the thought process behind Microsoft’s innovative new program. The tech giant is now making it possible for businesses to provide their employees with the ability to have fluid communication while utilising several different devices at the same time.
When Microsoft Core Services Engineering (CSE) planned a redesign, this is what they envisioned to provide each company that used Microsoft 365:
Inspiring employees
Engaging customers
Optimising operations
Changing the nature of the company’s products, services, and business models
They knew that if they incorporated Microsoft technology and products fluidly together, they could provide a valuable and familiar resource for both employees and customers. Microsoft wanted to present the possibility to businesses that Microsoft 365 could be the vehicle that could deliver their products and services to consumers in the modern world.
What is a Modern Workplace?
Employee expectations are always changing and evolving at a rapid pace. Business leaders sense the demand to keep up with a widening skills gap, diversity in their employees, and a need to think globally when assembling their teams. These pressures require a business to provide a reactive, modern workplace to meet the evolving needs of its consumer base. The modern workplace requires continuous communication while using multiple devices and platforms. All this must be accomplished while simultaneously being able to incorporate top-notch security that keeps your data safe.
A Modern Workplace Provides Seamless Collaboration
The modern workplace requires businesses to train their employees to be less static, and more dynamic. They need to assemble groups of people who come together to solve a problem, which shifts the focus from “me-centric” jobs to “we-centric” jobs. When a team can unite quickly, solve a problem, and collaborate with other teams, a business succeeds, and the employees feel empowered.
A Modern Workplace Provides a Multi-Device Experience
Enabling employees to utilise the devices they love is a way of letting personnel know that the company’s bottom line is for the employees and the consumers to come out winning. Microsoft mobile application management and mobile device management solutions decrease complexity and make for a happier environment. For example, an employee can start a meeting on an iPhone at a coffee shop and seamlessly end the meeting back at the office on a desktop computer. The user experience is no longer bound to a device—it travels with you.
A Modern Workplace Provides Intelligent Security That Protects the Company and the Customer
Having IT that is focused on protecting corporate data is crucial in today’s business. With the turn toward an intelligent cloud, a company can no longer just concern themselves with securing the perimeter. Their security stance must evolve or die.
Microsoft 365 protects both a company’s and consumer’s identity on your apps, data, and devices with comprehensive enterprise security. Also, the emerging cloud causes companies to ensure security for their customers. Microsoft 365 security stack works to proactively defend against malware, phishing, and zero-day attacks. Microsoft 365 security addresses business challenges that deal with intelligent security, such as:
Identity, app, data, and device protection using Azure Active Directory, Microsoft Intune, and Windows Information Protection.
Innovative protection with Office 365 Advanced Threat Protection and Windows Defender Advanced Threat Protection.
Data archiving, control, and detection with Advanced eDiscovery.
Instead of protecting companies by looking at dealing with an asset or device, they incorporate their intelligence systems to counter threats at a fundamental level.
A Modern Workplace Changes the Culture
A company’s culture begins with their values and vision and then translates to their practices, teamwork, and relationship building. Facilitating employees so they can be flexible and not afraid to make mistakes, but learn from them, is what a dynamic and successful company should strive to do.
Wrap Up
The modern workplace empowers your personnel to embrace change and be a part of shaping the culture of the company. A culture shift takes place when a team is empowered. Microsoft 365 gives you the tools to make it easier for you to build experiences like this. This makes it possible for teams to be more productive and successful in their jobs. It’s a win-win for both the employer and the employee.
Digital transformation is just as much about people as it is about technology. You will succeed when you show employees that they are vital to your company’s success. With the familiarity and ease of Microsoft 365, your team can place an emphasis on providing excellent goods and services to your customers. The complexity and challenges brought on by the advancement of rapidly evolving technology shouldn’t be an obstacle to employees. It should be an opportunity for them to display their creativity while adding value to your organisation.

by Felicien | Aug 21, 2018 | Education
EdTech has a long history of being misunderstood, underutilized, and of lacking support in every way. It is one of those bugaboos in education that seems like such a wonderful idea, but often falls apart in execution as money fears cause administrators to scale back. Lacking proper follow-through lessens the efficacy of even the best in educational technology – and that’s just a plain old waste of money.
Educators need support, but it’s nearly impossible – and very expensive – to put together an in-house ed-tech support team. And with 80% of schools now using cloud-based data storage, adequate tech support is crucial. Districts are limited by their budgets and the size of their staff. Any large-scale upgrades or maintenance can take forever and tie up literally every member of the IT support team. When there isn’t anything big going on, layoffs have to come down. Otherwise, there are too many people drawing salary and benefits for almost no work. That’s obviously untenable, so the default is to simply under-staff and makes do (which never works out optimally).
It’s an unenviable position to be in as an educational administrator. The solution is third-party tech support services.
Schools Are Already Doing It, And It Works!
Transportation, software support, substitute teaching, accounting…the list of third-party contractors in education keeps growing. Utilizing a third-party support contractor makes even more sense than some of the other contracts your district may have. IT gets highly technical and specialized. The skill set necessary to cater to a school or district’s needs is worth more than most schools can afford – especially in the public school system.
Plus, districts usually have SaaS applications – “software as a service.” These are applications licensed by schools that have native help sections. SaaS as part of licensing contracts gives districts the ability to call for tech support via phone, email, chatbox, or scheduled in-person service calls. Contracting out for IT services in general works in much the same way.
Scalability
Imagine having extra staff available when needed who just disappear when the need is gone. Contracting with a firm gives the school access to additional staff in emergencies or planned maintenance. Jobs with a large scope can be planned ahead with the IT contractor, with funds set aside for the additional hours and workers needed for projects. Having a contractor already on the books makes it easier to plan and bring in more people. It makes communication stress-free because the third-party will already be familiar with the school.
Using a third party allows administrators to:
Order staffing as needed.
Expect efficient, effective response to emergencies like outages, virus threats, and data breaches.
Ensure smooth, quick execution of planned upgrades with minimal disruption.
Support staff by offering assistance to individual faculty members.
Give faculty and staff immediate remote or in-person assistance.
Cost-Effective Expertise On Speed-Dial, Not On Staff
Even if a district is fortunate enough to have more than a skeleton crew of knowledgeable IT support staff, they likely won’t keep them long enough to become well-acquainted with the ins and outs of the district itself due to the comparatively low pay in school systems.
In Ron Schacter’s “Building An Ed Tech Dream Team” (District Administration March 2012), now six years old, school IT staff might expect to start at about $55,000 for basic support, but staff such as network architects will earn somewhere around $75,000-$80,000. Those IT workers could make a lot more if they went into the private sector, so they’re not going to stay long.
Thus, the supposed benefit of having someone in-house (i.e., their familiarity with the district’s needs) disappears. High turnover rates make for poor planning, disruption of services, and yearly retraining of a person or team upon whom everyone relies. It is poor planning that costs too much.
Moreover, with demands on educational technology growing, having a fully functional team able to respond to small and large-scale emergencies quickly grows too expensive for even larger districts. How can smaller districts or private, parochial, and charter schools possibly keep up? The reality is that many tried-and-true methods and educational tools simply won’t cut it anymore. The world is changing, including the field of education. Districts must find cost-effective ways to keep up.
Third-Party Support Supports Teachers
Teachers are not IT specialists. They are educators and must have the resources to teach. Put the power in their hands to use Ed Tech tools the way they were meant to be used. Stop using tech experts to restart computers and advise teachers to use Internet Explorer rather than Mozilla for their new application. Don’t make a teacher ask a kid from 4th hour to fix a problem with the desktop. Being reactionary rather than planning ahead always costs more. Sound planning that includes using third-party tech support offers flexibility and cost savings that maximize the educational benefits of rapidly evolving educational technology.
Conclusion
Reluctance to change leads to wasted time and money. By hiring less than the bare minimum IT staff and paying professionals well below their value, schools open themselves up to larger scale losses in the long-run, including:
High turnover requiring extensive, repeated searches for competent staff
Purchasing the wrong tech for a school’s needs
Purchasing something that is technically correct, but then cannot be fully utilized because the IT support is not there
Inefficient research carried out by non-tech staff
Network outages and unreliability cost time and money as well as loss of teaching time
Loss of staff and faculty due to frustrations over a poorly maintained infrastructure
When it comes to schools, you simply don’t have the resources to waste.

by Felicien | Aug 21, 2018 | Education
Every day, it seems, another security threat is in the news. The latest one involves some flaws in Intel chips that actually introduce a new vulnerability. The patches are out to address this, and hopefully, someone in your IT organization is tracking and applying them. But this is only one of the many ways your company can be vulnerable to cyber-criminals.
Good Security Is Proactive
Patches have to be applied. That’s good. But it’s also reactive. Doing whatever the news of the day tells you to do in regards to security is not a security plan. So, what is? And what does a good plan look like? Proactive security measures address every potential threat.
Human Factors
The biggest risk to security, by far, is human actors. These include your own employees and bad actors outside the organization. Humans, as the story of former White House Chief of Staff, John Podesta’s hacked email shows, make mistakes. To review, Podesta got an email he found suspicious, asking him to change his Gmail password. He sent a memo to his IT department. The IT staffer involved meant to tell him it was suspicious but made a typo in his reply email and told him it was okay. So, Podesta went ahead and click on the link exposing his database to Russian hackers. What went wrong here?
Facepalm Moment!
There are lots of things, but the most fundamental of them is that if security is a real concern, one does not use a free, public email service for email. Whatever else was in place, this episode shows that the DNC’s approach to security was flawed at the most fundamental level. People working at the White House should not use free, public services for sensitive email. It is a safe bet that, if you examine your organization’s security posture closely, there is at least one such facepalm moment lurking somewhere.
People do stupid things. One of the jobs of IT security professionals is to anticipate those things and make sure they don’t happen. Moving from passwords, which can be insecurely stored, to biometric identifiers, is one way to do this. People can’t easily steal your fingerprints or iris.
Portable devices are another issue. Having 24/7 access to a business device is great. But is it necessary? Laptops and smartphones are eminently losable. Ask whether every employee who has remote access needs it. Make sure you can remotely erase your company data from their device if it is lost or stolen.
The boundaries between work and non-work life grow ever thinner. There is no need to deny employees access to personal email. But on the company email server? Have them take personal mail to a browser-based service. Keep work and personal accounts firmly separated. This is a basic step that every company could and should be doing.
Auditing (Gently) The Vendors
There are good reasons to outsource many IT functions. Day-to-day operations rarely require high level IT expertise. It can easily be obtained from IT consultants and managed outsource providers and used as needed. Moreover, using outsourced IT providers who have many clients allows your organization to take advantage of the mistakes that their other customers have made. Most IT professionals have seen and heard it all. Use of consultants is a very inexpensive means of knowledge transfer, far cheaper than developing the same experience with in-house techs.
Make sure the IT provider knows their stuff. You may find a few whose security is really no better than yours. This is where it’s so important to check the company out before hiring them. Check their feedback online. See what their customers are saying about them. Do they really know how to secure your data and records so that you don’t get hit with a ransomware virus? Will, they set up both onsite and offsite backups so you’re never without your data even if disaster strikes?
Needing To Know
Transparency is, in general, good. But when dealing with health information that is protected by regulations like HIPAA, less is more. That is, less access is better insurance against risk. No one should be deprived of the data they need to do their job. But with protected health information, no one without a need to know should have access. Coders may need to see the physician’s notes in order to properly bill for services rendered. Billers do not. All they have to do is charge for the codes that are given to them. They do not need access to clinical data.
Conclusion
These considerations are very basic. They require no esoteric knowledge. But thinking through them will help you arrive at your own conclusions about whether your data is really safe. Remember these basics:
Be proactive about security.
Never take lightly the human factor.
Ensure third-party vendor security.
Apply the “need to know” concept.
Get help from a professional IT managed services provider if you still feel uneasy about your data’s security.

by Felicien | Aug 21, 2018 | Education
Communication—this is so important for the proper running of any business; however, it is even more essential for law firms where the stakes are arguably much higher. Over the years, communication between attorneys and their clients was a time-consuming process that depended primarily on scheduled face-to-face meetings and paper documents being mailed or hand-delivered for review and revision.
As in-office communication has evolved, fax machines, and then e-mailed messages allowed for a quicker turn-around for sharing documents and information. Unfortunately, this did not make collaboration with others, whether in-office or across the country, any easier. E-mail is notoriously inefficient for collaboration, since it is not totally secure, and as an e-mail chain of correspondence grows longer, it can become difficult to keep track of specific information. Important or sensitive info can become misplaced, or even mistakenly deleted.
Although initially costly and complicated, the platforms in the early 2000s made digital collaboration and sharing possible, especially for larger firms willing to invest in them. As technology continues to improve, it becomes increasingly easier to update and advance to the next level of IT solutions for firms of every size.
Modern methods of collaboration provide more security, better organization, and quicker ways to share ideas, as well as documents. Faster speeds, of course, directly correlate to how much one is able to get done in every given billable hour. As the old adage goes, “Time is money.”
What Do Collaboration Platforms Include?
An attorney’s day is often hectic consisting of communicating with new and existing clients, formulating strategies with associates, and managing cases. Add to that such tasks as updating calendars, logging hours, and making case notes. Often, each of these activities occurs using different management tools, requiring busy individuals to log in and out, consuming valuable time better spent on more important business.
With a collaboration platform, law firms are able to keep all billing and calendar systems, document sharing, emails, messaging, and video communications in one location. It should be available to each attorney and staff member affiliated with the firm who needs to view it. Granting access to all employees can be a big security risk.
Available on your desktop, laptop, or mobile device, collaboration platforms keep all communication in one convenient location. They allow users to chat one-on-one or with a team. In addition, they can organize messages and documents, share quick and concise memos, and start or join a video conference. Collaboration software also enables associates to share computer screens and documents, which facilitates ongoing team conversations. This provides a method for each associate to begin and end his or her day on one platform for ultimate efficiency.
How Does New Technology Improve a Law Firm’s Ability to Collaborate?
Modern law firms realize that effective communication and better organization methods improve their ability to serve their clients. This will also increase their productivity and profits. Collaboration involves individuals with different specialties and strengths working together to produce superior outcomes.
Whether participating colleagues are interacting in person or across a distance, everyone needs to be able to share documents, ideas, and information. Video conference capabilities allow collaborators to speak “face-to-face” even though they are communicating remotely.
As a team of attorneys build on the ideas of each other, brainstorming, combining knowledge and perspectives, they are able to create something that is greater than what each could provide individually. At the end of the day, each has a record of all relevant documents, emails, and messages available via a mobile application on their choice of electronic device.
How to Choose the Right Collaboration Platform
Collaboration software continues to influence how law firms view communication in the office but choosing the right one can be daunting. Savvy buyers look for a straightforward, user-friendly option that provides consumer support and training. They should select a platform that includes the ability to integrate some of their key programs with the existing systems, so work continues uninterrupted. Choosing software that is capable of automatic updates is advised. In fact, access to analytics, depositions, legal research, and AI software are not out of the reach for future options.
Consider choices that allow the administration to set the controls for the system and monitor the initial adoption and use of the platform, as well as ensure associates are complying with all data security standards. Piloting the collaboration platform with a small team eases the organization into the new techniques and allows the administrators to work out any issues before releasing it to the entire firm. This can prevent glitches and time-consuming problems.
In Conclusion
Technology continues to advance and online collaboration is no longer considered a new idea. As innovative technology platforms develop, they will increasingly be demanded in the office. The ability to collaborate online benefits both clients and their legal counselors. Clients no longer have to contact the office to request a hard copy of their file. By using an online portal, all parties involved can review, revise, and comment on documents instantly and conveniently on their personal computer.
As the dynamics of the legal workplace change, organizations must adapt and implement the most efficient and modern options available. Collaboration platforms are a logical and integral part of the legal office’s larger IT approach. Clients expect their lawyers to remain relevant, and law firms that fail to update, are not supplying their clients with the best experience or the most successful results.




