by Felicien | Sep 7, 2018 | Education
When companies fail at or are not prepared for a catastrophe, it’s often because they neglect to think that the unexpected is possible.
They often fall into one of two categories:
They assume disasters are unpredictable, so why prepare for them?
They fall into the allusion that their plans are fail proof (nobody can sink the Titanic).
Most disaster situations are simply due to a service outage or user error. But a catastrophe could wreak havoc on your business when you least expect it. Think about the thousands of companies in Houston that were shut down for weeks due to Hurricane Harvey in 2017. Nobody expected it, but it happened and many people were caught completely off guard.
Companies that take the time to be proactive are more likely to persist, despite a disaster. It requires a higher level of preparation than many businesses currently have. There are too many depending on a simple cloud backup service to save the day, but is that enough?
What is The Condition of Your Cloud Disaster Management Plan?
Current statistics show that more companies are taking inventory and calculating the risks of an attack on their IT infrastructure. However, there are still quite a few who are ill-informed and not doing enough.
Recently, a Forrester Research and Disaster Recovery report showed that up to 40% of companies currently have an official enterprise risk management program that is held accountable by a board or upper management. While the number of companies that are taking cloud disaster management seriously are improving, it’s obvious that not all companies are on board.
The difficulty with cloud disaster management, as with all disaster recovery programs, is that it’s never important until unexpectedly, it is. When a major disaster event occurs, it can take a company down in the blink of an eye.
Could This Happen to You?
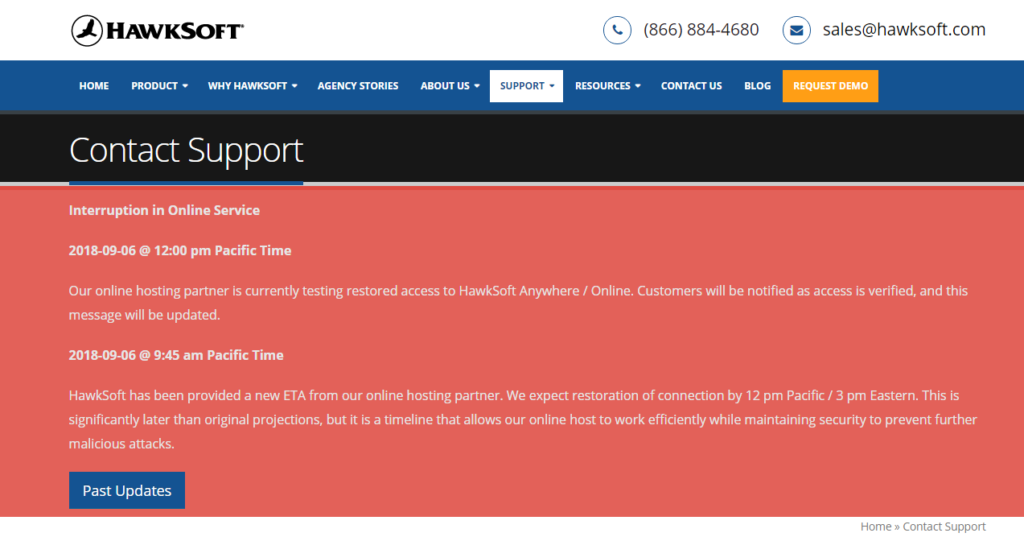
HawkSoft, an Insurance Agency Management platform, was just hit with a ransomware attack. Their business had to shut down until they could deal with hackers. Are you ready for a ransomware attack? Does your team know what to do? More importantly, your employees should be well-trained so that they recognize suspicious emails and attachments and do not click on them to begin with.
Recently, Ticketfly was the victim of a data breach. Over 26 million customers who use Ticketfly to purchase concert tickets were affected. Ticketfly’s parent company, Eventbrite, revealed that customer names, addresses, emails, and phone numbers were stolen by hackers. The breach damaged the company’s reputation and left millions of customers looking for a new place to buy their tickets.
The company had rave reviews from its customers. They most likely had a very sophisticated security system. So what went wrong?
When it comes to disaster recovery, it’s vital to choose an IT services provider that consistently tests their disaster management procedures. They need the best security resources money can buy, but they also need a well-qualified team of pros who understands what’s at stake.
Your IT services company should do more than just provide dependable hosting. They must stay on top of new hacking schemes. They should be running simulations on a regular basis that test disaster preparedness. They should be doing this internally and for their clients.
How Can You Manage Cloud Disaster Recovery Solutions?
A good disaster recovery plan includes the core IT services and infrastructure that your company depends on. These assets should be fully protected with today’s most effective security solutions. You need a qualified team of people who know what to do in case there is a breach. Acting quickly always limits the damage and makes your company look better in the media. Your shareholders and investors should be fully involved.
What Does Your Company Need to Survive a Disaster?
Did you know that service outages are the most common disasters that companies encounter when it comes to IT issues? However, even though possessing a strong data center solution is essential, there are many other situations that can wreak havoc, such as earthquakes, fires, floods, and severe storms. Your team should have a thorough plan to address events like these. That means backing up your data both onsite and offsite using a reliable cloud solution.
Do You Have a Complete Disaster Management Program?
No one ever thinks about what would happen if heavy rain caused the roof of your data center to cave in. What if your offices were flooded in a big rainstorm? How long would it take to get things back up and running again? You could lose several weeks’ worth of work.
Cloud disaster management isn’t something you should figure out on your own. You need a partner with the information, experience, and resources to know what could happen and how to respond. Sometimes you don’t get a second chance.
You need a business leader in cloud disaster recovery, with proficiency that guards every part of an IT system, from application management, to cloud hosting. All your software programs and data should be backed up regularly so that everything can be restored quickly.
Disasters Are Expensive
Each day that your company is shut down costs you money. Many small businesses in Houston never recovered after Hurricane Harvey. They had to close their doors. They learned the hard way how important disaster recovery is, but you don’t have to.
Look for experts in cloud disaster recovery who will get to know your business and develop a unique plan that addresses all the areas that are important to your business, from applications to servers. Make sure they have a good track record and can deliver on their promises. Working with a proactive IT services provider can ensure that your company survives no matter what.

by Felicien | Sep 7, 2018 | Education
It seems that small businesses rarely catch a break. Unfortunately, their employees often enjoy fewer perks than those working for larger corporations do. This is primarily because the smaller companies have fewer assets with which to work. Due to the smaller economic cushion, they also have a greater risk. That is why, when a fresh law is put into action for the “little guy,” it is newsworthy.
As with any new law, however, there are those that it benefits, those that are unaffected, and those that it may hurt. That’s why it’s good to stay informed.
What Are ESOPs?
ESOP stands for Employee Stock Ownership Plan. An ESOP allows the owner of a business to shift that ownership to his or her employees. This is often done by way of stocks or “shares.” In some companies, members buy stocks outright.
Other businesses require no upfront cost. The ESOP is part of an “employee benefits package.” It is considered part of his or her pay, and maybe figured as 50/50. This is where the company matches monies contributed by the employee. Often, the shares are held until retirement, and maybe, in fact, the bulk of that employee’s retirement.
Although ESOPs have existed much longer (just in different forms), they became prevalent in the 1980s. According to the National Center for Employee Ownership (NCEO), a few of the largest ESOP companies include the following:
Brookshire Brothers
Enercon Services, Inc.
Krueger International, Inc.
McCarthy Building Company
Publix Super Markets, Inc.
Travel and Transport, Inc
By 2018, the number of ESOPs has been estimated at between 7,000 and 8,900. The number of participants is over 14 million.
What Are the Pros of Employee Stock Ownership Plans?
Reputedly, there are many benefits to participating in ESOPs. For example, they generally have a positive effect on employees. A few of the primary perks include the following:
Employees feel more invested in the company
Invested employees are typically harder workers
Employees feel a greater sense of job satisfaction
They have more job stability
They feel like a part of something greater than themselves
They often make a tidy profit
ESOPs are particularly beneficial in small companies where the primary owner is planning to retire. This allows for a smooth transition of power. As the company succeeds, the employees succeed, and morale rises.
What Are the Cons of ESOPs?
One of the potential problems with an Employee Stock Ownership Plan occurs when the value of the company decreases after an employee buys in. When the business is worth less, each employee’s stock decreases in value. This usually occurs with companies that have inconsistent profits.
An example of this would be the case of Lifetouch Inc., which was a popular photography company. They primarily specialized in school photos. As digital photography techniques became the demand, the company struggled to adjust. Business suffered.
The company stock in ESOP declined by $840-million between 2015 and 2018. Lawsuits were filed against individual members of the Board of Directors. Unfortunately, the company’s ESOP was not protected against such losses. This is one example of what could go wrong with this type of retirement plan.
How Does the New Law Work and Who Does It Benefit?
New York Senator Kirsten Gillibrand introduced the Main Street Employee Ownership Act in May 2018. This ESOP law is the first to focus on employee ownership in the last 20 years. It eases the process for distributing loans for those transferring to an ESOP. However, there are no additional funds being allocated for this process.
Generally, the new ESOP law is thought to primarily benefit small to mid-sized businesses. More specifically, it targets the Small Business Administration (SBA) in two ways. First, it directs them to make small business loans more readily available to cooperatives. A Cooperatives is a style of business organization that is owned and run by the employees. They also share in the profits.
Second, it encourages the SBA to work with country-wide Small Business Development Centers (SBDC). SBDCs provide consultation and training to small businesses that are transitioning to an ESOP.
The ESOP Association’s president, J. Michael Keeling, was reported as saying the following:
“This law will help organizations better understand how to pursue a strategy of shared capitalism—something that our country’s founders agreed was vital to the health of our nation.”
In Conclusion
Whether Employee Stock Ownership Plans are the wave of the future is difficult to tell. The new law provides many benefits that make it an attractive proposition. It paves the way for small and mid-sized companies to more easily transfer ownership to employees. Consultation and training are more readily available for those companies wanting to make this transition. It also improves the ability to obtain loans. Overall, it appears things will be brighter for small businesses. As with anything, only time will tell.

by Felicien | Sep 7, 2018 | Education
An Inspector General’s (OIG) report from the Federal Department of Health and Human Services (HHS) finds that Maryland failed to secure its Medicaid Management Information System (MMIS) against several avenues of attack.
What Security Violations Did Maryland Commit?
The report, available in summary form at OIG Report on Maryland MMIS Security, does not go into detail for fear of revealing the nature of the vulnerabilities and possibly exposing the MMIS to penetration. It does note that, in addition to other techniques, automated penetration testing tools were used in an attempt to break into the system. The report indicates that these tools succeeded.
How Attacks Are Evolving
Other reports have noted that automated penetration tools are getting more sophisticated over time, and now far exceed the sort of attacks that were driven by “script kiddies” in the last decade. On top of that, despite increased efforts at email security and training workers in cybersecurity hygiene, phishing attacks, in which a phony email is used to get a user to perform an action that leads to system penetration, are all too common.
Because of the lack of detail in the OIG report, we can only speculate about what was attacked and what methods of penetration were used. Consider this, though. The typical MMIS is a mainframe-based system that is communicated with from terminals. It usually runs some version of Windows over networks that often must, of necessity, be routed partially over the public internet. Even if a virtual private network (VPN) is used for the connection, the “attack surface” – the set of points and vulnerabilities that led a bad actor to attack a system – is expansive.
All the attacker has to do is gain access to an unencrypted portion of the traffic. Inserting malware, such as ransomware or keyloggers, is simple from that point on. The lesson is that one must avoid penetration at all costs.
Was There A Cyber Security Attack on the Maryland MMIS?
The OIG report specifically notes that there is no evidence that the Maryland system had, in fact, been penetrated. But consider what might have happened if it had. The MMIS is used to pay Medicaid providers. While providers often complain that Medicaid payments are less than their cost of service, the aggregate amount of money involved is huge. Nationally, Medicaid spent almost 596 billion dollars in 2017. The expense is very roughly split 50/50 between the states and the Federal government for the traditional Medicaid population. For the people that were brought in under the Affordable Care Act (ACA) Medicaid expansion, the Federal government pays 90%.
A Huge Payday for Hackers
So, there is a pool of more than half a trillion dollars, potentially payable to providers, for hackers to attack. The MMIS in most states has modules for beneficiary enrollment, provider enrollment, recording of services rendered, and provider payments. A hacker who had control of the system could create phantom beneficiaries, phantom providers, bill for nonexistent services, and generate checks to pay the nonsexist providers for not providing them. Once the hacker is in the system, a potentially huge piggy bank is opened. The OIG’s principal worry in its report was the possible exposure of Medicaid data to the public, but the possibilities for fraud are equally worrying.
Why Does It Take So Long For Hacking To Be Discovered?
How quickly such a penetration would be detected is a function of the security measures the state has in place. The mere fact of finding a penetration does not, in and of itself, reveal where the miscreant was or what the hacker did. That requires checking of audit logs and development of a trail. Depending on what events are logged, even that might not be enough. In a worst-case scenario, not until some other event – a beneficiary notice returned as undeliverable, a bank questioning an electronic deposit, and so on – would sufficient suspicion be generated to lead to the discovery of phony providers and phony beneficiaries.
Holes In The Medicaid System
The MMIS includes tools for surveillance and utilization review, but their basic functions are still fairly unsophisticated, relying on detection of statistical outliers. Depending on where the limits are set, cases that are truly concerning may be missed. We can draw some instructive lessons from looking at what has been found out about HIV drug prescriptions under Medicare. In one case, a 48-year-old in Miami went to 28 different pharmacies to pick up HIV drugs worth over $200,000 dollars, in doses that were more than ten times what the typical HIV patient gets in a year (see Suspicious Prescriptions for HIV Drugs in Medicare).
Wrap Up
Maryland’s MMIS has parts that first came online in 1996. A contract to replace the system was terminated in 2015 and the case between the state and the prime contractor is now in the courts. Maryland’s experience in attempting to replace its MMIS system is not unique. Despite its surface simplicity, MMIS systems can involve hundreds of modules providing thousands of different functions that often have to interface with other state systems such as finance, enrollment and eligibility, public health, social services, and the state’s education system.
Designing and programming one is not easy. When it has to interface with multiple-aged legacy systems that the MMIS contractor has no control over, the job is even harder.

by Felicien | Sep 7, 2018 | Education
This month’s training on demand focuses on helping you find the most accurate information you need on Google.
We’ll leave no stone unturned in this 28-minute online training session. Learn how to find answers to your queries and questions right through to advanced techniques using Google.
Click the video play button below to get started.
Click Here To View Online

by Felicien | Sep 7, 2018 | Education
What’s WPA3?
WPA3 is an improvement to WPA2 security, which is still commonly used after having made substantial improvements over WPA. It is expected to better protect users from software hacking. In partial development for approximately 10 years, this improved form of security allows users to experience the benefits of additional features. These features include a wider range of settings, a more complex authentication system, and improved encryptions.
The recent integrations in security have included two versions, a WPA3-Personal version and a WPA3-Enterprise version. Both forms have been updated to include ongoing security improvements for the version. This involved removing legacy protocol and mandatory use of Protected Management Frames (PMFs) that have controlled resistances in networks used for operations. The personal version uses a new processing method referred to as Simultaneous Authentication of Equals (SAE), which secures connections between two devices while challenging external efforts to discover passwords.
The enterprise version provides 192-bit encryptions, higher than the enterprise version, and applies more cryptography tools than previous versions. As the software has only recently been developed, it has been integrated to some extent, but ongoing integration is expected to parallel increasing requirements for its use. This will challenge the current efforts of hackers. According to WiFi Alliance, the security improvement will be the standard for devices labeled as Wi-Fi Certified.
How Can It Better Protect Me From Hacking?
An improvement over WPA2 with increased encryption and tool application, many efforts of current hackers are expected to be again stunted without serious adaptations and improvements on their end of security demands. According to the New York Post, recent improvements in the way hackers operate have allowed them to violate users without waiting for a network connection. This improves their capacity to breach additional security and access information. However, WPA3 is expected to better protect users from both external and internal attacking.
Wired reports 9 billion Wi-Fi devices used worldwide, leading to one of the greatest security demands in computer software. This created the demand to improve WPA2 in terms of both connection security and addressing security challenges in user functions.
WPA3 development has been supervised by the Wi-Fi Alliance, and the organization does not expect WPA3 to be commonly used until the end of next year. WPA3 is also expected to lead to an increase in free connection use, improving the safety of organizations willing to extend access without any charge or subscription to a membership. The upgrade will provide substantially improved security specifically over dictionary attacks by using improved protocols for key exchange. While WPA2 uses a four-way connection between access points and clients, WPA3 will use SAE to avoid WPA2’s vulnerability to key reinstallation attacks (also referred to as KRACKs). This reduction in dictionary attacks is further supported by a system that safeguards traffic that occurred before a hack, restricting hacker access to information after an account has been breached.
Additional Benefits of WPA3 Technology
Other benefits of WPA3 can improve some areas of network and business securities. WPA2 currently allows people on a public network to observe user traffic while leaving users vulnerable to ‘middle man’ attacks and data tracking. WPA3 uses encryption connections without demanding additional credential information, and its encryption (referred to as Opportunistic Wireless Encryption) can protect users and organizations. Nonetheless, it is considered to be an investment that has significant cost to organizational operations. Business managers may not be inclined to spend more for better technology.
The timeline for mainstream integration is expected to span over the next several years. As the first release was just in June of this year, it follows a 2006 release of WPA2 that also continued to be released over several years’ time.
According to SecurityIntelligence, organizations should expect approximately 18 months before devices begin to be commonly certified, followed by additional time in organizations investing in the technology. In addition to certified devices being the foundation of use, people with mismatched hardware may find that their routers are not compatible with WPA3 Wi-Fi connections. Some routers are expected to have preservation potential while being usable with these improved security devices and connections. Some will not be usable with the upgrades.
WPA3 is not expected to address all security demands in the current Internet of Things or IoT landscape. Threats that have their roots in compromised devices will not be protected in the use of connections made by users. This remaining vulnerability alongside WPA2’s generally safe nature have made many consumers hesitant to invest in the upgrade immediately now that it is available.
What Should I Know?
WPA3 provides improved authentication processes.
WPA3 provides increased encryption.
WPA3 does protect all users connected in the IoT.
The upgrade will cost more but should be worth it in the long run.




