
by Felicien | Sep 11, 2018 | Education
What is CVE-2018-6177?
Today’s new releases of browser software are supposed to be improvements over past versions in terms of functionality, helpful features, security, and the speed of overall operation. However, these changes often involve new vulnerabilities which hackers can target and exploit. A recent release of Google Chrome is a good example. A vulnerability allowed hackers to access user information stored in major web platforms such as Facebook and Google. This vulnerability was identified as CVE-2018-6177. It was only recently addressed with the release of a patch known as Chrome 68.
How Have People Been Affected?
The Chrome vulnerability has caused people to hesitate about upgrading to the most current version of the browser. The previous release’s vulnerability has allowed hackers to have increased access to data stored on online databases, including Google and Facebook, leaving a full range of personal information exposed.
The vulnerability exploits a weakness in audio and video HTML tags used in the engine. It has been listed in the Common Vulnerabilities and Exposures database, a dot.org website dedicated to such issues. The National Vulnerability Database (NVD), a US government establishment also dedicated to this cause notes an entry about these issues that is incomplete.
The most severe attacks that a user can experience include identity theft, resources theft, and system damage through the execution of arbitrary code. Users could also experience common side effects of hacker attacks, including being locked out of their accounts, or having to address unauthorized messages or postings. Users may also be redirected to sites that could involve phishing attempts or some other damaging hacking effort. Denial-of-service and authorized network accounts are also possible for organizations or individuals becoming victims to hackers exploiting the vulnerability.
The Center for Internet Security reported that the most recent release of the browser will show unsecure designations on websites using HTTP rather than HTTPS (standard hyper-text transfer protocol rather than secured protocol of this type). This may make users assume that state, local, tribal, or territorial (SLTT) government websites are not secure. While users are recommended to follow federal and developer organization guidelines for security, the risk of the vulnerability remaining in the software is classified as high for multiple user types. More specifically, the range of vulnerability levels for user types are reported as being:
‘High’ for large and medium government and business entities
‘Medium’ for small government and business entities
‘Low’ for home or individual users
The vulnerability is also referred to as a cross-origin information leak specific to the internal Blink Engine, or web browsing database used as a foundational operating platform for the browser. The Center for Internet Security recommends that users:
Apply the stable channel update available through Google
Run software as a non-privileged or non-administrative user (to minimize impacts of successful attacks)
Ensure non-trusted links are not browsed
Inform all users of the vulnerability and its demands
Apply a Principle of Least Privilege (maximizing security and minimizing accessibility amid organizational requirements) to all systems, users, and services
Reporting on potential instances of successful hacks through this vulnerability, The Hacker News described a scenario where a user with a Facebook account could potentially have their personal information accessed and misused.
A researcher with this source made several Facebook posts, using different combinations of audiences to categorize potential victim types by personal traits categorized by the service, and confirmed the nature of the vulnerability. When a website embeds multiple Facebook posts of this type on a webpage, it loads and displays only some of them, based on matching to individual profile information.
The vulnerability allows hackers to gain access to the personal information of visitors to such pages, and regardless of their privacy settings. The browser version does not have a direct way for administrators to determine if embedded posts were loaded for specific visitors, creating a security demand to check and address this.
Users can attempt to rely on Cross-Origin Resource Sharing (CORS), a security feature within the browser that blocks websites from reading content from other sites without authorization. However, as the aforementioned audio and video HTML tags do not validate the types of content retrieved from other sources or block responses with invalid Multipurpose Internet Mail Extensions (MIMEs), hackers are able to use multiple hidden tags on websites to request Facebook post information.
While the approach does not generate Facebook posts, hackers can exploit the vulnerability while using JavaScript to gauge request numbers and read the sizes of cross-origin resources to determine which posts and information sets they can get from users. Since several scripts run simultaneously, hackers can effectively data mine once they are able to generate these responses.
Hackers can potentially design sites to return different response sizes dependent on the traits of the logged-in users, and then record information from all people observed through the connections.
The vulnerability is similar to another recent browser issue, a related difficulty involved in cross-origin requests that allowed hackers to read Gmail and Facebook messages. The previous issue was patched in June, and although the current issue was addressed in a patch included with Chrome 68, unpatched users remain vulnerable to the described exploitations.
What’s The Bottom Line?
Chrome releases have been subject to audio and video HTML tag vulnerabilities.
Facebook and Google messages, along with personal information are vulnerable.
Chrome 68 has addressed the issue; users are recommended to replace their older version with the patched version immediately.

by Felicien | Sep 11, 2018 | Education
What’s smart about a smart home? Well, you can talk to it. You can tell your phone to tell the oven to turn itself down to 200 degrees. You can tell your thermostat to drop the nighttime temperature to 68. You can start the car from the upstairs guest bathroom. And so on.
What you may not realize is that the technology behind these simple tasks is staggering. All of them wholly or partially involve the transmission of data from the oven, the thermostat, and the car across the internet, and anything involving voice recognition is likely to invoke a mainframe running in the cloud to do the voice processing. All of that takes place in an amount of time short enough for you not to notice any lag between the command and the execution.
If that’s what a smart home looks like, what does a smart healthcare organization look like?
The answer to that question involves noting that we are moving from the first generation of cloud services into the second, while most healthcare organizations are only making partial use of the first generation. And we need to take note of what the renowned consulting firm McKinsey calls the “data culture,” one which most healthcare organizations have yet to adopt.
Is Your Hospital As Smart As Your Thermostat?
The Nest Learning Thermostat is capable of learning the temperature control patterns you use and going through them even when you are away. In addition, you can control it from anywhere in the world with your phone. Simply memorizing a pattern is not very advanced. What is advanced is discovering patterns that no human suspected were even there.
A famous example was Walmart’s discovery, made by an AI system, that there was a surge in sales of strawberry Pop-Tarts whenever a hurricane was forecast in South Florida. Not cinnamon and brown sugar Pop-Tarts. Not green apple Pop-Tarts. Strawberry Pop-Tarts. Hurricanes were forecast, so the Walmart trucks loaded up with strawberry Pop-Tarts and rolled towards South Florida. Walmart’s profits inched up a little bit. Of such small fragments are large corporate incomes made.
What Does The Strawberry Pop-Tarts Story Tell Us?
To make that profit-making discovery, Walmart’s systems needed to have data available – detailed sales records, broken down by ZIP code, inventory records are broken down by store, and weather data, all available to the same system. This is the first lesson. Data can no longer be siloed. If patterns are to be found, the data in which they exist must at least appear as one data set.
The second lesson is like the first: For analysis, old(er) data is fine. For action, data must be real-time. It does no good if the Nest thermostat is adjusting the in-home temperature based on the outside temperature readings from six months ago.
The third lesson, somewhat less obvious than the other two, is this: To be effective, the actions taken must make a difference. The difference here was in profit. In a health care organization, it might be patient load, room occupancy, revenue stream, patient satisfaction, physician satisfaction, nurse retention, or cost reduction.
The key is linking action to some parameter that is important. Analysis for the sake of analysis is likely to be fruitless, and organizations that engage in it will be disappointed and decide that AI is not for them. And if they decide that, they are almost certain to reduce their future competitiveness, and perhaps their very survival.
How Is Cloud Evolution Affecting AI?
The cloud is rapidly evolving from a place where data is simply stored to a place where the vast majority of an organization’s data is used to create a bigger bottom line.
The advantages of a cloud for health care organizations are increased security, decreased hardware and software expenses, decreased IT staff expenses, and lack of worries about capacity in terms of processors, memory, or storage.
The big worry for healthcare organizations is the loss of control. Cloud providers are becoming more sensitive to this issue and devoting more resources to collaborating with clients in health care to increase their comfort level.
Cloud providers are also very aware that their clients are interested in using AI and are moving to capture that market. One piece of advice is not to combine a migration to the cloud with a major rollout of AI unless you know the pitfalls in advance and have made contingency plans for when things don’t work. Having competent consultants can make the difference between success and failure.
What Is Needed For AI Success?
McKinsey refers to the part of organizational culture that thinks about and uses data as the “data culture.” Its research has discovered that there are wide differences in the data culture of organizations.
Key elements are:
General employee awareness of data and its benefits
An integrating of data into the organization’s day-to-day operations (as opposed to “cool stuff” that gets developed and never used)
Executive and board buy-in
The linkage of data with affirmative actions
This latter does not mean that you know what you will do with the results that AI produces before they happen. It does mean that the organization is “reality-based” and is committed to taking the actions that AI reveals as possibilities, provided they are linked to parameters that are important to the organization.
What Are The Key AI-Enabled Technologies Of Cloud 2.0?
Advanced analysis, deep learning, voice recognition, virtual agents (software that acts like humans for specific tasks), robotics, machine learning, image recognition and analysis, natural language programming, and more are all available today.
The key question is what hospitals can use them for. One obvious application is voice recognition and virtual agents for patients able to communicate, replacing the call bell in a hospital room. Instead of having an aide go to the room to answer the bell, then come back and tell the nurse what is needed, just put an Amazon Echo Dot in each room.
The hospital saves time and money while patient satisfaction improves. This is just one of a vast number of ways hospitals could use today’s advanced AI technologies to improve healthcare. The question is whether they’re ready to move into 21st century technology.

by Felicien | Sep 11, 2018 | Education
Improvements in technology have led to increased connectivity with improvements in security, but have also involved unique vulnerabilities and potential for hackers to access a wide range of information. Particularly problematic to businesses is the potential for a phisher to represent a part of the organization, or a supplier with a business connection to it, as they request organizational information or even funding.
What Are Current Major Risks?
Business managers and employees run the risk of being phished from their work accounts while seemingly doing normal business, only to find that they inadvertently provided company funds or information that could be used to damage the company’s systems or even their reputation. This creates new demand for organizational and network security processes and defenses, with phishing, internet-of-things (IoT) security, and general WPA2 hacking being among the greatest current threats to major organizations, small businesses, and individuals alike.
Phishing internally can lead to thousands or even millions of dollars accidentally provided or outright stolen after the critical information is inadvertently provided. An individual can create an email using some phishing technique to hide, mask, or otherwise misrepresent their actual identity while claiming to be an active member, supplier, or some other legitimate affiliate of the organization. The recipient may receive a SharePoint document link that is hyperlinked to malware capable of hacking or damaging system software, and while being directed to a login screen or invoice to request funds or sensitive information to be further misused.
Hackers have the potential to work around even the most advanced anti-phishing filters, using tactics such as reducing the triggering text to a font size of zero to avoid detection. This allows them to pass the filters with how the data is read while displaying apparently legitimate communications and requests to an organizational manager or employee.
According to the Business Owner’s Guide to Technology, these instances have been common. The reporters cited two recent instances of tens of thousands of dollars being accidentally sent amid a phishing campaign. This campaign went beyond the fake login screen to record credentials in attempts to involve phony invoices as well. There have been cases where millions of dollars were lost through a similar approach.
Another major risk that organizations have, amid a false sense of security, is the size of their network in their maintained IoT. While it has become common for tablet devices, personal laptops, mobile phones, and other devices to be used within a business network for increased internet connectivity and email, it is also becoming more common for hackers to use their own devices to access information. This can potentially be done internally or externally, creating a demand for increased security or upgrading beyond vulnerabilities in the WPA2 security protocol. This issue follows along the lines of phishing potentials in terms of general security vulnerabilities that are the greatest threat to large businesses, small businesses, and individuals alike.
WPA2 hacking, in general, has become more effective, as the protocol itself has been upgraded and developed for security vulnerabilities realized to demand a completely new protocol, WPA3.
Inc. explained that hackers may very well have preferences for businesses, due to the probability that at least some bit of useable information can be recorded from the network. While managers and even network administrators may assume that the most recent mainstream releases of security software and protocol recommendations are enough to protect them, hackers continue to work against these, demanding that upgrades and software that have yet to become mainstream be implemented. This, therefore, demands ongoing research and dedication to optimizing network security.
What Other Specific Recommendations Are There For General Risks?
Beyond general best practices and the issues listed above, experts continue to make recommendations for the optimization of security. To optimize defenses against phishing, a combination of proactive awareness campaigns of recent threats and optimizing the use of available security features is all experts can recommend avoiding inadvertent user cooperation.
To optimize defenses against WPA2 hacking, if transfer to the now-available WPA3 is not possible or deemed sufficiently feasible, minimizing network accessibility to essential job functions or requirements only for all users, while maximizing all relevant security, is recommended. Multi-step user authentications can help against both phishing and hacking attempts.
Other issues are not as commonplace or severe, but are still regarded as important. Network owners are advised to watch out for privilege escalations, which hackers may use in an attempt to gain increasing access to information once they have breached the network to any extent. Maintaining control though rootkit detection is also recommended, as are methods to scan activities and ‘backdoors’ for forms of malware left by hackers who may have been able to remove their event logs before installing their own backdoor access.
As a final measure, taking extra steps to ensure that all employees are actually operating in compliance with security protocols is recommended, as many organizational managers may not even be aware of the extent of shortcuts or vulnerabilities they effectively allow for the sake of convenience. Purple Griffon is one online source that has compiled additional details regarding these potential threats and recommended protective actions.
What’s Most Important?
Ensuring compliance and best practices against phishing
Advanced anti-phishing protection (ATP) or related software
Network security optimization or WPA3 integration
Remaining current with news, research, and developments
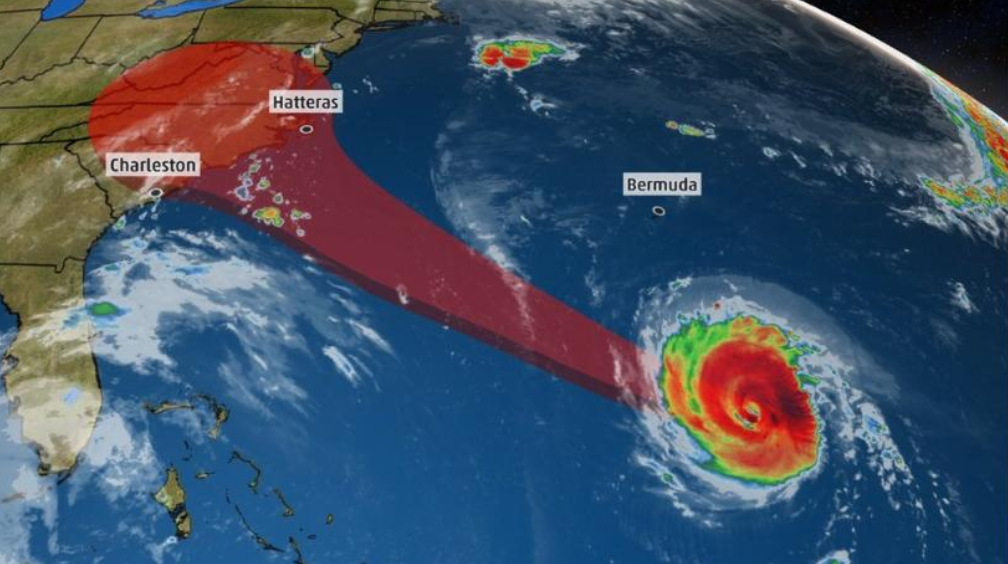
by Felicien | Sep 11, 2018 | Education
Hurricane Florence strengthens to Category 4
Evacuation Orders Begin in the Carolinas
The National Hurricane Center is now saying that Florence has maximum sustained winds of 115mph, with gusts to 140mph. It is now a Category 4 storm and is expected to hit the Southeastern US coast on Thursday.
North Carolina, South Carolina, Maryland, and Virginia governors have declared a state of emergency and urged residents to be prepared by stocking up on the essential supplies of food, water, flashlights, and batteries.
N.C. Governor asks Trump for Federal Declaration
With Hurricane Florence setting its sights on the Carolinas, North Carolina Governor Roy Cooper has asked President Trump to declare a federal disaster. The Governor said on Monday, the federal declaration would allow for federal assistance and increase the state and local efforts in providing for a proper emergency response. Governor Cooper said he had a conversation with FEMA Director Brock Long on Monday.
Governor Cooper Says to Prepare for the Worst
The North Carolina governor also forewarned citizens in Hurricane Florence’s path to prepare to be without power for an extended period of time.
In a Monday Morning press conference, Cooper said, “When it comes to utilities, families need to be ready. They need to prepare to be without power for a while; that’s why we’re urging people to have their emergency kits and prepare for this.”
Currently leaving it up to local and county governments, Cooper also anticipates the other coastal communities in North Carolina to issue mandatory evacuation orders for residents and visitors just like Dare County and Hatteras Island have already done.
Military Bases are Preparing for Florence
In Norfolk, Virginia, the U.S. Navy has directed all working warships and submarines in the area to leave port in advance of Hurricane Florence. Both the Naval Station Norfolk and Joint Expeditionary Base Little Creek have said they have almost 30 ships currently planning evacuate as soon as possible.
With an extensive beachfront, Camp Lejeune is preparing for Hurricane Florence as well. The largest U.S. Marine Corps base on the East Coast, Lejeune is located about 50 miles northeast of Wilmington, North Carolina.
Historic Hurricane
If the hurricane hits as hard as predicted, Florence will be the most powerful to strike the area in three decades. Water could reach up to 15 feet high, and rainfall will move inland over the next four to five days.
The center of the hurricane is heading over the southwestern Atlantic Ocean between Bermuda and the Bahamas and some are predicting it to intensify into a Category 4 storm. With winds possibly reaching as high as 130-156 mph by Wednesday, it should reach the East Coast on Thursday or early Friday.
The last category 3 hurricane to hit the Atlantic Southeast Coast was Hurricane Fran in September 1996. Fran caused extensive damage and was the fourth major hurricane of the 1996 Atlantic hurricane season.
Category 4 Hurricane History in the Southeast
The deadliest and most powerful hurricanes to hit the Southeast Atlantic North of Florida were Hurricane Hazel. in September 1954 and hurricane Hugo in September 1989. Hazel reached the U.S. right around the border between North and South Carolina, registering as a Category 4 hurricane. Before reaching the U.S., Hazel killed more than 400 people in Haiti. It then belted Canada, categorized as an extratropical storm.
Hurricane Hugo was briefly a Category 5 hurricane crossing over Guadeloupe and St. Croix. It Weakened as it passed over Puerto Rico to a Category 3 hurricane and was downgraded to a Category 2 as it rematerialized in the Atlantic. But, just before it reached just the Charleston area it re-strengthened into a Category 4 hurricane, with 140 mph sustained winds.
Hurricane Florence News from Myrtle Beach
Myrtle Beach area residents have been asked to evacuate if and when Governor Henry McMaster gives the order. Myrtle Beach Spokesman Mark Kruea said for those who make the choice to ignore the order, “You take your own life into your hands.”
Kruea also said Myrtle Beach does not have “mandatory” the evacuation policy, but they strongly warn about the dangers if its citizens choose to stay.
Hurricane Florence News from Charleston, SC
Hurricane Florence’s path looks Charlotte and the city’s surrounding area will experience the impact of the Hurricane’s power.
Charlotte authorities are closely monitoring the Hurricane’s progress to help its residents be ready when Florence makes landfall and moves inland.
Hurricane Florence News from Wilmington, NC
Wilmington and all of Southeastern North Carolina area could easily be affected by Hurricane Florence and are encouraged to take precautions by local government agencies.
The University of North Carolina Wilmington (UNCW) announced classes are canceled and issued a voluntary evacuation for all its students as the storm continues to rapidly approach the Carolina coast.
Hurricane Florence News from Florence, NC
Damaging winds and flooding rain are very possible later this week as Hurricane Florence moves inland. Florence residents are asked to start thinking now about how they will prepare for Florence and be vigilant about watching the progress of the Hurricane.

by Felicien | Sep 10, 2018 | Education
If you’ve ever attended a high-level education course or business meeting, chances are you’ve come across the PowerPoint presentation. Microsoft’s PowerPoint program has been helping students and professionals organize their thoughts and ideas for decades. From class presentations to complex business proposals, Microsoft PowerPoint 2016 holds a wide range of benefits for users. Familiarizing yourself with the program’s many features can help you create engaging and error-free presentations every single time.
How To Spell Check Your PowerPoint Presentations
It’s important to make a good impression on your audience when using PowerPoint. This includes proper spelling and grammar throughout the entirety of your presentation. Misspelled words and grammar errors can make for an embarrassing moment in front of classmates or colleagues. This is why it’s important to learn to utilize PowerPoint’s wide range of tools. Knowing when and how to check the spelling within your PowerPoint proves you’ve gone the extra mile to produce a professional presentation that helps your audience clearly understand your talking points.
There are several things you can do to improve the overall user experience. Here are a few steps to follow to spell check your PowerPoint presentation.
Run A Spell Check
PowerPoint automatically checks spelling for its users. As you type, you might find some words underlined in red. This can happen quite often in the first draft of your presentation, so don’t panic. While PowerPoint will draw attention to your errors automatically, if you’d rather wait until after you’re done with your presentation to spell check, you have that option, as well.
PowerPoint’s Spelling and Grammar tool was designed to help users create error-free presentations. Once you notice an error, simply right-click on the word to reveal an option for correction. You can also choose the “Add to Dictionary” option, which will avoid PowerPoint flagging the word for the remainder of the presentation.
If you are ready to spell check your entire presentation after you’re finished, click the “Review” tab and then click “Spelling.” PowerPoint will move through each error, offering you options to edit, until you have reviewed them all. PowerPoint will provide alternative options for every error. You may choose one of these suggestions, then click “change” to correct the spelling error. If there are no suggestions provided, or none that make sense for your presentation, you’ll be able to manually type in the word’s correct spelling.
You can repeat this process for each error you encounter as you navigate your presentation. Once the last error has been corrected, you’ll see a dialog box that will confirm your presentation’s spell check is now complete.
Contrary to popular belief, PowerPoint’s Spelling and Grammar tool isn’t flawless. For words like proper nouns and people’s names, the system may still detect an error even if there isn’t one. You can easily ignore spelling suggestions if they don’t apply. Just click “Ignore” to skip a word without changing it. You can also ignore all by clicking “Ignore All”. This will not only skip the word without changing it, but will also skip over other uses of the word for the remainder of the presentation.
Modify Your Proofing Options
Microsoft PowerPoint allows users to modify and customize proofing options to allow more control over the process. For instance, you have the option of customizing the way PowerPoint notifies you of spelling errors. The grammar check also carries the option of helping you correct contextual spelling errors, further simplifying the process as you type. To modify these proofing options, access Backstage view by clicking the File tab, then select the Proofing option to customize as needed.
Find And Replace Words
Finding and replacing certain words is easy with Microsoft PowerPoint. Doing this can help you save time as you work on your presentation. For Mac users, simply locate the “Search in PowerPoint” box in the upper-right corner of your screen, then click the arrow right next to it. This will provide the option to “Replace” text. In the “Find What” box, type in the word you’d like to locate, then type in the word you’d like to use instead, inside the “Replace With” box. You can click “Find Next” to locate the next occurrence of the word, or simply click “Replace All” to replace all occurrences.
Present In Different Languages
Microsoft Office, above all, is intended to make work more efficient for its users. PowerPoint for instance, allows users to type in different languages, such as Chinese or Arabic. To type your presentation in one of these non-Latin based languages, you first must change your keyboard layout. If you’re unable to locate your desired language through Office, you may need to add it manually or download a Language Accessory Pack. These packs can add extra display and/or proofing tools to help you create a highly professional PowerPoint presentation.
Microsoft PowerPoint 2016 is one of many tools within the Office Suite designed to make business better for users. Utilizing these tools to their fullest can potential can help businesses achieve their goals more efficiently than ever before.




