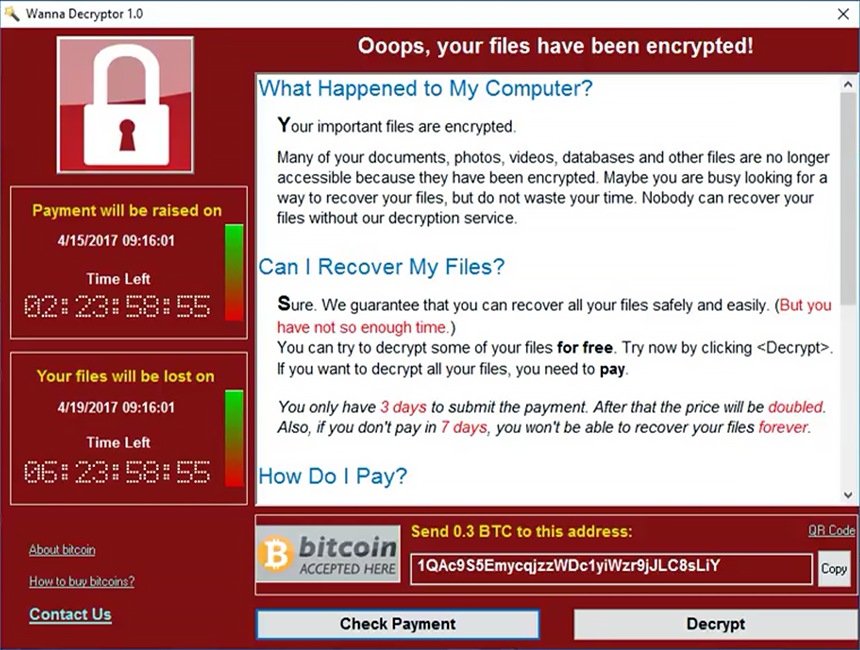
On May 12, 2017 a new strain of the Ransom.CryptXXX (WannaCry) strain of ransomware began spreading widely impacting a large number of organizations, particularly in Europe. This virus specifically targets Microsoft Windows computers.
A hacking tool known as Eternal Blue, developed by US CIA has been enhanced by the hackers to super-charge an existing form of ransomware known as WannaCry, three senior cyber security analysts said.
Wcry is demanding a ransom of $300 to $600 in Bitcoin to be paid by May 15, or, in the event that deadline is missed, a higher fee by May 19. The messages left on the screen say files will remain encrypted. It’s not yet clear if there are flaws in the encryption scheme that might allow the victims to restore the files without paying the ransom.
If you have yet to install the Microsoft fix—MS17-010— you should do so immediately. You should also be extremely suspicious of all e-mails you receive, particularly those that ask the recipient to open attached documents or click on Web links.
If you are an existing client of ours on our Managed Services Platform, you would have already received the fix through your weekly patching cycle, If not please check with your IT and or Security provider to ensure you are covered
Read Reuters Article : http://www.reuters.com/article/us-britain-security-hospitals-idUSKBN18820S
Hiring Tech: 2019 CEOs Tech Hiring Guide
As your business operations evolve and expand, you’ll likely reach a critical point in your company’s growth where the tasks required will outnumber the staff you have available. Deciding to outsource work might be a difficult decision, partly because of...
New Way To Communicate
The Power to Conference & Collaborate Better Can Be Yours Microsoft has just announced the June 2019 release of its Surface Hub 2, a tool for conferencing and collaboration among teams. This is the Surface Hub’s successor, and it boasts improvements to the...
Hackers Steal Company Information
Cybercriminals have started 2019 off by stealing more than 1.7 billion records. They look for data that is profitable in some way, whether they sell it directly or use it as part of another attack. A successful intrusion attempt comes from various factors, such as an...